Introduction
RFID is an abbreviation for radio frequency identification and consists of three essential elements; tag, tag reader and host system (Roberts, 2006), all of which will be discussed in more detail shortly. Melbourne university library services just recently made some breaking historical news when the first ever RFID technology was launched with EFTPOS in 2010 (Fetech Group, 2010). This was implemented in its libraries located at Melbourne city and Eastern part of Melbourne (Fetech Group, 2010). This revolutionary technology for libraries which was installed at Melbourne library was a significant milestone towards safeguarding the library materials and attainment of an automated self-service to its rapidly increasing number of customers. Notable to mention is that, Melbourne city library has registered approximately 3000 customers in addition to about 3500 book loan transactions performed on weekly basis (Fetech Group, 2010). This paper discusses the benefits proffered by RFID technology in regard to Melbourne library, its technology and efficacy in maintaining high security of books and other materials in libraries in which it is used.
Overview of RFID technology applications
The RFID technology application is currently not limited to library use only as it is widely used for other purposes in various sectors. A study by Zhu et al (2011) explores the areas in which RFID technology has been utilized so far which it identifies as largely to be in supply chain management because of its many benefits that it has in terms of costs, convenience and reliability. Besides, tourism, health, logistic industries and other sectors, use of RFID technology is effectively used in libraries because of its suitability which we shall discuss in the following section of the paper (Zhu, Mukhopadhyay and Kurata, 2011).
At Melbourne library for instance, statistics indicate that since the RFID system was introduced, 94% of all transactions performed are self-serviced (Fetech Group, 2010). This is one of the major benefits of the RFID technology that Ferrer et al (2010) describe as “self-service enabler” which is possible because the technology does not require manning. This is possible because this new technology involves the use of advanced radio wave technology to differentiate between legal and illegal borrowed items (Fetech Group, 2010). RFID system can also be used at security check point, precisely to track illegal items carried across checkpoints. This RFID system using radio wave technology transmits data/information from an electronic tag fitted on the library item such as a book, which helps to identify the object as legal or illegal (Rfid-library, 2010).
Some RFID tags reading strength varies, for example some tags are capable of being detected electronically from several meters away; this RFID technology is popular and highly recommended for use especially in big size libraries to protect books that are worth millions from theft. This is mostly achieved by the fact that RFID technology has capabilities of scanning books as people pass by without stopping them and once an illegal book or item is detected, the alarm is triggered thereby alerting the security guards who will eventually take over (Coyle, 2005). The system can also scan across books while on the shelves checking those ones in bad condition and those which require repairs (Rfid-library, 2010). The figure below indicates the relay process that takes place during the working process of a RFID device.
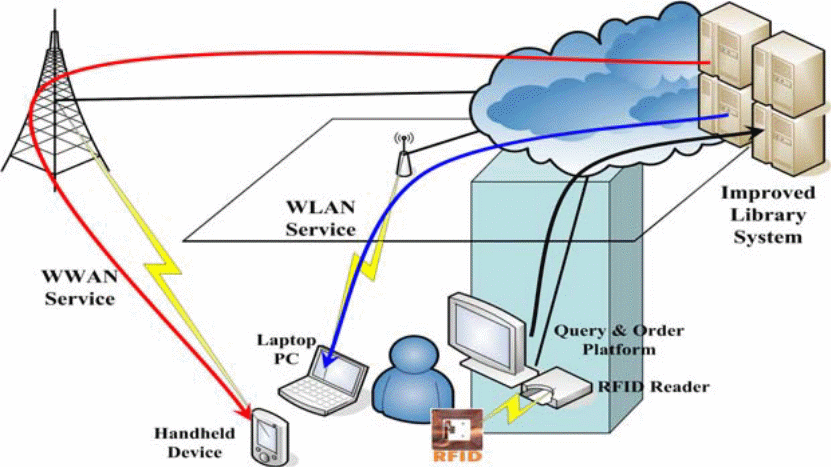
In this case the RFID tag is the most important component since it is the point of contact that is traced by the signal through a preconfigured IP address as shown in the diagram above (Chen et al, 2007).
This wireless technology used in RFID is similar to that used in cellular phones technology which uses radio waves to communicate with other objects. The RFID technology for libraries was designed specifically to replace the old bar code scanners and Electro-Magnetic security strips technology among others which have been used in many libraries in the past (Rfid-library, 2010). The RFID system which was formerly known only for security operation has with time gradually advanced to a multipurpose role of tracking down lost items and over the years more complex and accurate tracking features have been integrated in the system to increase its efficiency in checking and clearing items besides other purposes (Technovelgy Incorporation, 2010).
The RFID system technology which uses radio frequency technology, together with the microchip technology has been ranked as the world latest and most reliable technology being used in many libraries, to safeguard items and track down stolen items (Technovelgy Incorporation, 2010; Chao, Yang and Jen, 2007). In fact, RFID is considered “as one of the ten greatest contributory technologies of the 21st century” according to one research study done by Chao et al (2007). RFID is most suited to library security since the technology does not require any line of sight to operate or a fixed plane to read tags, contrary to what other old fashioned theft detecting systems require (Rfid-library, 2010).
Most importantly, RFID has a memory storage component that enables it to store variety of crucial information for each item that it is fitted with (Chao et al, 2007); it is this ability that is central to the working of the whole system. This is also its greatest strength over all other similar technologies because, the distant between the reader and the tag is not always critical unless in few cases where the exit gates are extra wide. In summary, the major areas where RFDI technology is being utilized are; in libraries, health sectors, supply chain management, museums, aviation and hospitality industry among others (Ngai, Moon, Riggins, and Candace, 2007).
Justification of the study
The main reason as to why various libraries globally and in most modern society are adopting the RFID system is to ease their daily operation and promote reliability. Currently, most libraries are adapting to the new criteria in regard to security that they are required to meet, efficiency, cost reduction on their daily operations and privacy. This automatic RFID system and self service have therefore enabled most libraries under all categories (big size, small size), to improve on their mode of circulation and perfectly manage inventory controls (Want, 2004). This translates to daily library operations which are more secure, quick and which require fewer personnel to implement; this reduces operational costs since only very few personnel need to be hired (Want, 2004). All this is achieved because of the fact that RFID security system can access information on tags fitted on books using radio waves automatically much faster than most similar technologies thereby saving time when locating books.
Technology behind RFID
RFID system is primarily composed of major components which are essential in tracking or detecting an object wirelessly. This components include; the antennae, the radio frequency tag (or the transponder) and the reader or transceiver which is integrated with a decoder (Beal, 2010; Ferrer, Dew and Apte, 2010). The RFID tags are categorized into three major categories; “passive, semi-passive and active” (Liu and Bailey, 2009). Passive tags have weak signals and are therefore limited in terms of the range in which they can function effectively; semi-passive tags are those that utilize both battery power and readers signal strength while active tags are those that only utilize battery power for its operations (Liu and Bailey, 2009). The RFID system coordinates its operations under a low end-radio frequency precisely used for RFID systems globally as per the laws set by the governing body; the federal communication commission (FCC) (Rfid-library, 2010).
For this purposes, RFID must be used solely to manage a library and perform frequent automatic check in/checkout of items, thereby protecting them from theft.
RFID system components include; the antenna which is constantly emitting radio waves signals and in the process turning on/activating the RFID tag which is always present on the library item (Bonsor, Keener and Fenlon, 2011) The antenna also reads and encodes any additional information on the tag any time it passes across security gates. The information acquired from the tag is thereafter transmitted by the antennae to the reader, which is then quickly converted to radio waves and finally reflected back to the tag to be stored (Bonson et al, 2011) The most important function of the RFID systems is to facilitate the transmission of data into portable small devices referred as tags which are then read and accessed by the RFID reader.
The data stored by the tag include identification details, location, price, date borrowed, date of expiry and many more information needed by the library (Piramuthu, 2007). The latest advanced technology capability of RFID system that enables it to perform both tag identification and antitheft detection, ranks it as the most efficient technology that is currently being used in ultra modern libraries. As mentioned before the system requires no line of sight for the tag/target to be identified since the tag contains some specialized security bits which are used in conjunction with the readers. This enables the reader to scan through more than one target at the same time efficiently saving time. By saving time, the staffs are in most cases relieved of duties, just waiting for the alarm whenever an illegal item attempts to passes across the sensor gates (Pandey, 2010; Coyle, 2005). All this operation is always accomplished automatically.
Tracking devices used in libraries and technology behind their operation
EM (Electro-magnetic tracking device)
The EM device is usually fitted with sensors which are widely used for theft detection in libraries; the EM (electro-magnetic) security technology precisely operates on a magnetic field basis (Cdtagstorage Incorporation, 2009). The system is usually fitted with a sensor which partners with the target (another component similar to the RFID reader) and a tag respectively. The targets have a unique characteristic whereby they cannot be turned off by any magnetic device whatsoever. Moreover, the sensor is usually reinforced with an automatic alarm which is configured by the sensor to sound whenever an item is passed on illegally (Cdtagstorage Incorporation, 2009; Coyle, 2005).
These targets are composed of strips of metals containing pieces of magnetic particles specifically for enabling resensitizing and desensitizing functions; this is primarily accomplished by use of high powered magnetism devices (Cdtagstorage Incorporation, 2009). Furthermore, when turning off or desensitizing the strip, the librarian must rub the area of strip location with a specific magnetic device; this enables the library staffs to pass through the specific material across the security aisle without sounding the alarm (Cdtagstorage Incorporation, 2009). Whenever any library material is returned back, it is immediately reset or turned on by the librarian using gadgets such as desktops and specific handheld devices.
The same devices are also used to demagnetize or remagnetize other library materials. Most of the available strips are for books, videocassettes, computerized discs, audio cassettes among others. Notable to mention is that, this EM system must always be installed some fair distance away from the gate or any metallic door and computer terminals. This distance always varies depending on the number of existing computers (Cdtagstorage Incorporation, 2009).
RF (Radio Frequency)
This RF (Radio frequency) devices theft detection system operates under the basis of low-end radio frequency; the radio frequency systems usually rely on radio frequency waves set and regulated by the federal communication commission (FCC) (Cdtagstorage Incorporation, 2009; Want, 2004). This board only works on this RF frequencies and never interferes with other foreign FM frequencies for example the radio station frequencies. The most fundamental role of security targets is just to circulate library materials with information’s whenever tuned on which means that the librarian must tune off the targets manually when needed and a special designed detuning tag or card is used to do this.
The principle behind this detuning is that; once detuned, the signal emitted is interrupted allowing passage of the borrowed library item across the security aisle without alarm detection (Coyle, 2005). Once the library item is returned, the librarian will eventually remove the detuning tag activating the signal reception once again at the security aisle set by the antennae. This RF technology is globally considered to be safe for use on audiovisual media since it does not always require reactivation and deactivation of material frequently which makes it more preferable.
One major advantage of RF security system is that it cannot be falsely activated by coins or jewellery, since the system is hardwired through a special standardized existing outlet (Cdtagstorage Incorporation, 2009). In addition to that, the RF sensor must also be installed some fair distance from the metallic door or a computer terminal. The main difference with EM systems is that the distance required is slightly less than what EM systems require.
Bar code scanner
This is one of the new tracking devices employed in most libraries globally; bar code is basically a scannable number which can be detected by use of specific type of radiations (Leadtools Organization, 2011). There are several types of bar codes including the 1D barcode and the 2D barcode; this advanced technology basically integrates the creation, detection and finally the decoding of barcodes symbols with imaging technologies (Leadtools Organization, 2011). This barcode scanner operates at a high speed and is very reliable. There is a database set aside where the library properties are recorded and registered against each specific barcode. When an item is borrowed, the bar code number is cross referenced against the information on the database ensuring that the alarm is not triggered falsely (Leadtools Organization, 2011). If the item is illegally acquired, an alarm is turned on and library security takes over.
Smart card
Smart card technology is used in many modern libraries especially those attended by thousands of users since its quick and very reliable technologically. A smartcard driver contains embedded integrated circuits and also possesses micro processor components and memory (Clercq, 2011). The card basically is made up of polyvinyl chloride (plastic) in which relevant information and protocols which may include signals are sent in form of digital messaging to the computer where all the library information is stored, this message is also sent to the smartcard where it is stored (Clercq, 2011).
RFID system
The RFID which is commonly employed in modern libraries globally is composed of four components namely; the RFID tag, the sensor/ reader, the tag and the server (Controlelectric Organization, 2004). All these components collectively work together to ensure that the RFID functions reliably and effectively. The tag is usually the heart of this system and is typically fixed at the cover of the book, either front or back page or directly onto the computerized disc or videos (Shahid, 2005). Technologically, the tag is equipped with an electronic antennae and a programmable chip; in addition to all this, each thin paper tag is fitted with an engraved antenna with a microchip capable of holding a capacity of 64 bits (Shahid, 2005).
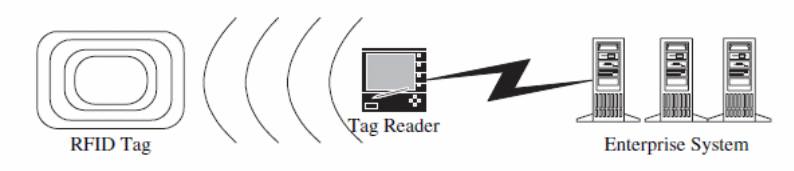
Among the three types or varieties of tags available, there are read-only tags which are not rewritable once encoded at the time of manufacturing (Shahid, 2005). There are also read/write tags which are the best preferred for use by many libraries; this is because of their information flexibility (Shahid, 2005).
The RFID reader
The reader is described as the component that “can read data from and write data to compatible RFID tags” (Ngai et al, 2007). The RFID reader plays an important role when it comes to interpretation of information.
The reader powers the antennae to fully generate an RF field, which has capabilities of detecting a tag that passes through the field (Shahid, 2005). The information stored on the chips of the tag is interpreted by the reader (RFID exit gate sensors) and the information is automatically sent to the server (Shahid, 2005). The server has a role of checking the circulation database, commands an alarm to sound when the material scanned is not correctly checked out but does not do so when the signal is internally verified (Shahid, 2005).
The antenna
The Antenna produces radio signals specifically meant to “activate a tag, read and write data on it” and can be described as the link between the tag and the reader (Cdtagstorage Incorporation, 2009). For example, it can be fitted on library door frames to detect and receive data from the tags passing through. Technologically, the antenna is the one that controls the RFID systems’ data acquisition and communication since it constantly circulates the electromagnetic waves for continual inspection of the specific tag (Shahid, 2005).
The server
This is considered as the central heart of the RFID system; it is the major communication gateway which receives data from several readers and exchanges the received information with the circulation database (Shahid, 2005). The server is installed with softwares such as the Session Initiation Protocol (SIP/SIP2), the Application Programming Interface (APIs), among other approved software based on the specific library vendor (Shahid, 2005).
RFID label printer
The RFID printer is another important component of the RFID system; it is basically used when printing labels (with individual bar code) for library books, library logo and all library designs (Cdtagstorage Incorporation, 2009). As long as the printing is done, it simultaneously and automatically updates on the chip; after the whole process, the same label is transferred to the book (Cdtagstorage Incorporation, 2009).
The external book return
This is a feature that enables users to return library items such as books even when the library is closed since the machine is fitted with slots which have “chips for RFID reader sandwiched between the walls” (Shahid, 2005). The machine works in a way that the user must first be identified before proceeding to place the book on the return slot and wait for the receipt. The chip RFID reader then analyzes the user’s record(s) of all books borrowed and those returned and then produces a receipt containing the updated report (Shahid, 2005).
Conclusion
It is quite clear from the above discussion that the use of RFID technology is a comprehensive system which as we have seen presents various benefits, especially to modern libraries. This is clearly reflected based on the fact that it is very fast and efficient in facilitating passage of library items across security items and is the most reliable technique to use as security in the library (Pandey, 2010).
Health hazards
The RFID system technology however has its limitations, the major disadvantage is that it is expensive to install since the cost of the reader and the gate sensor is in the range of $2000 to $5000 each, while each tag costs about $40 to $75 (Usingrfid Organization, 2008).
Also, the use of RFID is hazardous; when the RFID transponder gets into direct contact with the human flesh (skin) since it causes tissue reactions (Antichip Organization, 2008). Moreover, the use of these radio frequencies is dangerous to patients who have undergone metallic implantation since the frequencies are likely to react with the conductive metallic implants resulting to severe burns on the patient (Antichip Organization, 2008). Note that when the customer buys and agrees to use the RFID system, the customer may unknowingly agree not to sue the company responsible for any health side effects caused by the system (Ashley, 2011).
Solution
Health experts have offered a number of solutions for the above challenges that are associated with RFID technology. First, one should possess a Medic Alert bracelet for safety against the RF chips as this would assist the emergency units whenever such a person is in danger and thereby facilitate recovery (Antichip Organization, 2008). The RFID systems which use radio wave to operate are also hazardous to the environment and human health due to their radioactive emissions (Davidcke, 2010). These electromagnetic radiations, similar to those emitted by the antennae of the RFID affect mostly those who frequently use these systems (Davidcke, 2010). The only way to prevent this is to restrict the usage of such radiations in high power areas, as well as reduce unnecessary frequent monitoring (Antichip Organization, 2008).
Advantages and disadvantages
First, RFID technology with proper implementation is quite reliable (Pandey, 2010). Secondly, the simplified nature of operation in addition to the self-patron check in/ checkout of the system has enabled modern libraries to operate with few security personnel, cutting management costs especially on salaries. Thirdly, the RFID system is integrated with an anti-theft software which detects and commands the alarm to ring whenever any item is stolen from the library (Pandey, 2010). Fourth, the system is very fast and scans through all library items, identifying items which are worn out and require repair. Fifth, the system is considered to have long-term service guarantee(s) when the protocols of operation follow the set standards (Pandey, 2010).
The main limitation of the RFID system however, is that it is not cost effective in the short term; it is very expensive to purchase and the RFID tag have a life span of 100,000 transactions before they expire and need replacements (Rfid-library, 2010). But at least this is better and less cheap than the barcode which has a shorter lifespan and the related costs of personnel required to man libraries in the absence of RFID technology. The other disadvantage of RFID system has to do with the breach of the users’ confidential data and privacy which presents security issues (Piramuthu, 2007). If the user has another tag containing his/her personal information for instance, it will automatically be read by the RFID reader thereby exposing the clients personal information possibly to dangerous persons (Usingrfid Organization, 2008; Piramuthu, 2007).
Furthermore, several cases of RFID reader collision have been reported. This is when the signals extracted from one reader are interfered with by signals from another reader within the range covered. However, this has lately been corrected by the use of Time Division Multiple Access (TDMA), which commands the reader to read at different times to avoid this collision (Shahid, 2005).
References
Antichip Organization, 2008. Health risks-Antic hips. Web.
Ashley, G. 2011. Podcast script- health risks of microchips on human body. Web.
Beal, V. 2010. Radio frequency identification. Web.
Bonsor, K., Keener, C. & Fenlon, W. 2011. How stuffs works-RFID. Web.
Cdtagandstorage Incorporation, 2009. Security and Theft. Web.
Chao, C., Yang, J. and Jen, W., 2007. Determining technology trends and forecasts of RFID by a historical review and bibliometric analysis from 1991 to 2005. Technovation, 27: 268–279.
Chen, J., Chen, M., Chen, C. and Chang, Y. 2007. Architecture design and performance evaluation of RFID object tracking systems. Computer Communications, 30: 2070–2086.
Clercq, J. 2011. Smart card technology. Web.
Coyle, K., 2005. Management of RFID in libraries. The Journal of Academic Librarianship, 31, 5: 486–489.
Controlelectric Organization, 2004. Types of RFID. Web.
Davidcke, 2010. RFID Chips will be forced thanks to Health Bill! Web.
Ferrer, G. Dew, N. and Apte, U. 2010. When is RFID right for your service? International Journal of Production Economics, 124, 2: pp 414-425.
Fetech Group, 2010. Melbourne library services. Web.
Liu, A. and Bailey, L. 2009. PAP: A privacy and authentication protocol for passive RFID tags. Computer Communications 32: 1194–1199.
Leadtools Organization, 2011. Lee tools barcode SDK. Web.
Ngai, E., Moon, K., Riggins, S. and Candace, Y. 2007. RFID research: An academic literature review (1995–2005) and future research directions. International Journal of Production Economics, 112, 2: 510-520.
Pandey, K. 2010. Advantages and disadvantages of RFID technology. Web.
Piramuthu, S. 2007. Protocols for RFID tag/reader authentication. Decision Support Systems 43: 897–914.
Rfid-library, 2007. Library RFID Management System. Web.
Roberts, M., 2006. Radio frequency identification (RFID). Computers & Security, 2 (5): 18 – 26.
Shahid, S. 2005. The use of RFID technology in libraries. Web.
Technovelgy Incorporation, 2010. What is RFID? Online) Web.
Usingrfid Organization, 2008. RFID advantages and disadvantages. Web.
Want, R., 2004. A Key to Automating Everything. Scientific American, 2: 56–65.
Zhu, X., Mukhopadhyay, S. and Kurata, H. 2011. A review of RFID technology and its managerial applications in different industries. J. Eng. Technol. Manage, 12: 1-16.
