Abstract
Deploying a wireless sensor network (WSN) in unattended environments such as the military makes it vulnerable to Sybil attacks entailing the security and privacy of the WSN to become crucial. Using firewalls and other encryption schemes is impossible because the nodes are resource-limited. A triple key management technique using secure routing protocols, random key distribution mechanisms provides the required security solution.
Introduction
Studies by Du, Deng, Han and Varshney (2006, p.67) and Du, Deng, Han, Varshney, Katz, and Khalili (2005, 250) have shown the rationale for securing wireless sensor networks (WSN) deployed in hostile environments against a range of attacks such as Sybil attacks. Attacks that compromise such networks, especially in military and business environments have disastrous consequences. Roosta, Shieh, and Sastry (2006, p.210) and Anurag, Rathor, Biradar, and Ghose (2010, p.23) proposed solutions to such attacks is the use of a triple key management framework, random key pre-distribution, and secure routing protocols. Roosta, Shieh, and Sastry (2006, p.211) realized the weakness of using the graph key distribution SN nodes for secure routing of data.
Research by Anurag, Rathor, Biradar, and Ghose (2010, p.23) established that the miniaturization of WSN nodes makes the privacy and security of the WSN a fundamental issue. Anurag, Rathor, Biradar and Ghose 2010, p.590 and Biradar and Patil (2011, p.15) contributions to studies by Anurag, Rathor, Biradar, and Ghose (2010, p.23) show that WSN nodes are resource-limited in CPU, memory, communication bandwidth, and energy approaching integrating security solutions into each node in the WSN a critical challenge. According to Undercover, Ayancha, Joshi, and Pinkston (2004, p. 260), Biradar and Patil (2011, p.12), Blom (1984, p.336), and Du, Xiao, Guizani and Chen (2007, P. 25), traditional network security solutions such as intrusion detection/prevention (ID/IDP) firewalls, the use of computationally-intensive public-key cryptography, encryption and decryption, and authentication security mechanisms cannot be applied for WSNs
Many security solutions available for WSN expose WSN nodes vulnerable to attacks, making the rationale for the use of triple key management security (Poornima & Amberker 2009, p. 5-17; Sharma, Ghosh & Ghose 2010, p.50; Perrig, Szewczyk, Wen, Culler & Tygar 2011, p.96).
The three-phase process for the triple key management with optimal security solution includes “pre-key distribution, path key management, and shared key discovery” (Biradar & Patil, 2011, p.25). According to Ibriq and Mahgoub (2007, p.211) and Biradar and Patil (2011, p.15), the security framework for WSN in this report relies on three-way communication paradigms which are many to one, one to one, or many to many.
Problem Statement
The wireless network is the most vulnerable type of network to security attack. Unauthorized access to a wireless network is easy. This is because it transmits data over open space. Unauthorized access to a wireless network is easy. Wireless also coined new threats and modifies the current information security hazard profile. For example, since communications accrue “through the air” using radio frequencies, the danger of capture is greater than with wired networks. If the message is not encrypted, the attacker can reach it, thereby weakens confidentiality.
Furthermore, Ad hock wireless sensor networks are resource-limited to accommodate the traditional computationally intensive cryptographic (such as asymmetric cryptography) and intrusion detection/prevention (IDS/IDPS) security mechanisms. A secure method that addresses the vulnerabilities in WSN nodes is a triple key management scheme using network, senor, and cluster keys making them secure in commercial and military environments. The triple key management scheme overcomes the weaknesses in the basic random key pre-distribution scheme; the master key-based key pre-distribution scheme, and the single key distribution scheme.
Aim
The aim is to develop a completely secure WSN based on the triple key management scheme that is applicable in hostile environments and able to resist attacks against the WSN. This will be done through three layers of security, which is “pre-key distribution, path key management, and shared key discovery.
Objectives
- To make a completely secure wireless network at each node.
- Apply the triple key management for each node in the WSN.
The importance of this study
A Wireless Sensor Networks (WSN) is vulnerable to a wide range of attacks given the resource limitations and ad-hock nature of the nodes. The security goals of the WSN can only be met on a Key management scheme based on triple keys. This study is important because it shows the importance of triple key management for creating a completely secure network that is resilient against attacks.
Literature Review
Introduction
This section details extensive research conducted by Eschenauer and Gligor (2002, p.45), Gautam, Lee, Pyun, and Jae-Young (2009,p.119), Ibriq and Mahgoub (2007,p.216), Hu, Ziobro, Tillett, and Sharma (2003,p.170), Karlof, Wagner (2003, p.23), and Kaplantzis (2006, p. 19) among other authors on random key distribution, key management schemes including the triple key management, WSN secure routing protocols, secure key management schemes, and malicious node detection mechanism, and attacks on WSN.
Attacks on WSN
Research by Gautam, Lee, Pyun, and Jae-Young (2009, p.119) shows that WSN is vulnerable to attacks that compromise the integrity of the WSN nodes by decreasing the nodes’ fault tolerance capabilities, data distribution, and multipath routing of packets. Hu, Ziobro, Tillett, and Sharma (2003,p.170), Karlof and Wagner (2003, p.23), and Kaplantzis (2006, p. 20) that Sybil attacks as being critical in WSN because the attacks compromise the integrity of the network by ensuring broadcast packets based on direct vs. indirect communication, stolen vs. fabricated identities are undetected. Eschenauer and Gligor (2002, p.45) and Gautam, Lee, Pyun, and Jae-Young (2009, p.119) show that Sybil attacks are propagated directly or indirectly using misbehaving nodes, voting, routing, data aggregation, and distributed storage techniques. A detailed study on solutions based on direct validation, indirect validation, resource testing are deficient countermeasures against such attacks. Liu, Ning, and Li (2005, p.50) questions and affirms that modern techniques which depend on radio resource testing, post verification, RSSI based detection scheme, registration, code attestation, and random key distribution do not provide complete security to a WSN underscoring the need for a triple key management scheme.
The random key distribution
Studies by Du, Xiao, Guizani and Chen (2007, p.230) have significantly contributed to the knowledge that the triple key management mechanisms ensure a better and complete security solution using the random key distribution mechanism. In this case, a “node identity is mapped into the indices one-way function using its keys” (Guizani & Chen 2007, p.232), and “indirect validation with the probability of using a randomly generated identity p” (Guizani & Chen 2007, p.232), which compels an intruder to make 1/p trials before gaining a usable Sybil identity to compromise the network” (Guizani & Chen 2007, p.232). The polynomial-based Single-space pairwise key distribution technique has shown drastic resistance to Sybil attacks (Blundo, Santis, Herzberg, Kutten, Vaccaro & Yung 1992, p.475). Studies by Gautam, Lee, Pyun, and Jae-Young (2009, p. 23) and Lee & Stinson (2004, p.300) provide extensive proof that integrating a pre key distribution mechanism and cryptographic schemes into the security paradigm of WSN provides a completely secure network against attacks.
Triple Key Management Scheme
Findings by Liu & Ning (2005, p.10-20) that the triple key management mechanism provides optimum security by enabling the use of two pre-deployed keys for each of the WS nodes, and a cluster key that is in-network generated. Du, Xiao, Guizani, and Chen (2007, p.23) and Boyle and Newe (2008, p.34) have demonstrated that such a network has a base station that generates both the sensor and network keys. Here, the “communication mechanism involves a sensor key which is used to encrypt and decrypt data routed to the base station, which is decrypted by each target node and rerouted to the cluster header” (Hancke & Leuschner (2007, p.49). In this case, the cluster header communicates with the base station and adds its ID and the packet load together (Liu, Ning & Du 2008, p.28). Authentication on the MAC packet received at the base is used to verify the integrity of the packet as illustrated in figure 2 below.
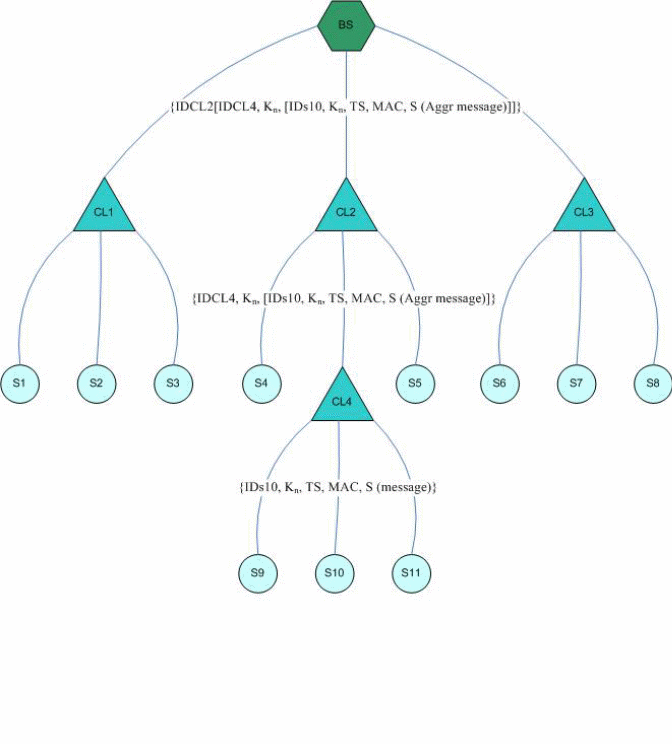
In the context of this study, similar studies by Liu, Ning, and Du (2008, p.28) on the security of triple key management schemes are in agreement with other studies which show that each of the nodes has two pre-deployed keys. The first key is the network generated key to satisfy the requirements of a hierarchical network. The network key (kn) is generated by the base station which is pre-deployed in each node in the network to encrypt data to enforce data integrity as it hops from one node to the next.
The next key in the triple key management scheme is the sensor key (Ks), which is generated by the base station to decrypt information that is sent to the base station. Study results show that the “key is generated and pre-deployed in each of the sensor nodes in the network and shared by all nodes in the network” (Hancke & Leuschner 2007, p.49). The last key is the cluster key (kc) that is shared by the clusters in that network and only belongs to a specific cluster in the network to decrypt data that is forwarded to the cluster leaders in each of the cluster nodes.
Hancke and Leuschner (2007, p.49) and Luk, Mezzour, Perrig, and Gligor (2007,p.488) regard the critical elements in the mechanism to include the network key, the cluster key, and the sensor key. In the above case, the broadcast data is encrypted by the base station using Kn and the sensor node decrypts the message using the Ks (sensor key). Figure 1 shows a base station that encrypts and sends its ID, with a network key (Kn) and a time stamp TS, and a message authentication code MAC for the message (m) as illustrated below.
The message construct sent to the cluster node by the underlying node is as shown below.
The message is rebuilt by the cluster and the final value is as shown below.
In a typical scenario, if a finite filed is taken of GF(q) whose coefficients are defined in the polynomial P(x, y, z) of degree c, then, P(x, y, z) = P(y, x, z), the following scenario unfolds (Mittal & Belagodu 2009, p.20).
Polynomial fi (x) = P(x, y, i) is received by node ni
Polynomial fj (x) = P(x, y, j) is received by nj
Polynomial fl (x) = P(x, y, l) is received by node nj,
P (i, j, l) is the common key for the i, j, and l
In the above context, the triple key distribution for the time, T-T1, T2, T3, as follows.
By Chan, Perrig & Song 2003, p.212
In the above case, T= [3]92, 3, 7).
The key distribution mechanism uses a prime number q as the ‘power’ with degree c for the 3-legged trade (Poornima & Amberker 2009, p.11).
If |X| = v, involves a set of elements constituted in X which are included in the relation (k ≥4) are constituted in X so that the elements are T1, T2, T3 sets of the subsets, then the following condition holds for the key distribution.
The innovative nature of triple key management
The triple key management scheme provides secure services by combining different techniques that contribute to the security and privacy of the wireless sensor network. Studies by Ayancha, Joshi, and Pinkston (2004, p. 260) have shown that the security of the network is enhanced because a small number of keys are placed in each sensor node and each procedure has a low probability of making two nodes to share a similar key. The security is enhanced by the use of a key establishment to create secure paths between pairs of sensor nodes which are later used to connect different pairs of nodes when discovering new paths. Another unique factor that makes the scheme secure is that compromised keys can easily be revoked from the system. It is possible to ensure information security using secure passive monitoring for each of the data routed in the paths that are established in the network. In addition to the combination of several techniques used to make the scheme secure, the c-degree polynomial underlies the driving concept of secure key distribution.
WSN protocols
Secure routing Protocols for WSN
Studies by Perrig, Szewczyk, Wen, Culler, and Tygar (2011, p.96) show that a secure routing information protocol enables effective implementation of authentication and integrity checking defenses against spoofing of routing information and Sybil attacks. Findings by Perrig, Szewczyk, Wen, Culler & Tygar (2011, p.96) agree with Boyle and Newe (2008, p.70) which show that security holes in WSN networks are caused by interception and attacks on broadcast routing information by the base station. Here, an intruder intercepts and modifies broadcast routing information when there is no proper authentication. According to Perrig, Szewczyk, Tygar, Dwen & Culler (2002, p.530) asserts that a security solution is to use a secure routing protocol that relies on the concept of one way hash chain. In this case, the “input information is hashed based on a hashing algorithm which takes a variable length of text and produces a fixed length hash value” (Boyle & Newe 2008, p.70). The computational infeasibility of reversing the hash value into the original message provides the message integrity required to ensure secure information broadcast to destination hops in the WSN by the base node (Pietro, Mancini, Mei, APanconesi &. Radhakrishnan 2008,p.3).
The technique involves the sharing of keys with each network node based on the one-way hash chain generated by the base station having Kn keys of length n, with K1 sent to each node in the base station with loose synchronization (Spencer 2000, p. 2). The packets arriving at the base station are authenticated using the message authentication code (MAC), with each of the packets arriving at i intervals (Pottie & Kaiser 2000, p.550. The destination node uses the key to authenticate the message packets which had arrived previously (Das 2008, p.139). It is critical to note that the nodes possess the key Kv with v<i. In the process, when there is a successful verification event for Kv, the replacement that occurs for the packet that had arrived becomes successful, making Ki to be accepted by the destination node. That prevents any attack based on an already spoofed packet as illustrated below.
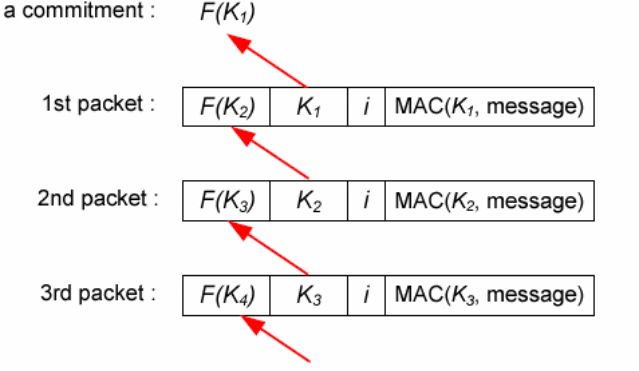
The sequence (F (Kn+1) jKnji) of the packet authentication process shown above shows the relationship between the packets on transmission, with i denoting the actual contents of the packet on transmission (Chan, Perrig & Song 2003, p.200).
Security aware protocols
Anjum, Pandey, and Agrawal (2005, p.199) argue that the security-aware ad hoc Routing (SAR) protocol based on the security attributes integrated into the ad hoc route discovery provides sufficient security on WSN. (Cam, Cam, Muthuavinashiappan, Ozdemir and Nair 2003, p.29990) affirms that SAR overcomes apparent weaknesses in traditional methods of determining distances between nodes based on hops by providing new routing measurements based on geographic location and other attributes that enable secure implementation based on the forwarding behavior of broadcast packets. According to Anderson, Chan, and Perrig (2004, p.209), the distance between WSN nodes might not be the shortest, and the most secure, based on a quantifiable secure route. Based on the SAR protocol, the nodes in the network are mirrored into a hierarchy based on explicit partial-ordering of privilege levels.
Hancke and Leuschner (2007, p.45) detail a study on the Quality of Protection (QoP) bit vector method. In QoP, Each node is assigned trust levels which cannot be arbitrarily changed. Hancke and Leuschner (2007, p.45) state that the interception, modification, or subversion of messages on the transmission is protected by the triple key management mechanism integrated into the security solutions. Hancke and Leuschner (2007, p.45) argue that the security of the packets on transmission based on the (Security-aware AODV) protocol requires the addition of the RQ SEC REQUIREMENT to discover a packet en-route. Nodes that receive the RREQ packet assess the integrity and security compliance status and the protocol forwards the packet if it is deemed secure. Packets that fall short of the security requirement are dropped.
TinySec Protocol
Karlof, Sastry, and Wagner (2004, p.172), have detailed that TinySec is implemented on the link layer and addresses security requirements of the resource staffed nodes in the WSN based on the link-layer cryptography (Zhou & Fang 2007, p.1009). The link-layer protocol security requirements include message integrity, access control, and message confidentiality (Zia & Zomaya 2006, p.24). Research has shown that current protocols are deficient in providing message integrity, authentication, and confidentiality on WSN. The IPSec, SSL/TLS protocols cannot be applied on resource staffed WSN nodes because they are resource-intensive. TinySec provides security solutions based on authentication only (TinySec-Auth), and the authenticated encryption (TinySec-AE) security options (Karlof, Sastry & Wagner 2004, p.172; Varshney 2006, p.23). TinySec uses “MAC to authenticate data payload which has been encrypted” (Zia & Zomaya 2006, p.24) and “MAC computations done on the packet data” (Zia & Zomaya 2006, p.24).
Malicious node detection mechanisms
Khalil, Bagchi & Nina-Rotaru (2005, p.90) argue that many applications are vulnerable to intrusion attacks and can provide misleading reports about misbehaving nodes. Some of the mechanisms under such a category include the Bayesian fault recognition algorithm which relies on the spatial relationship of environmental conditions (Undercoffer, Ayancha, Joshi, Pinkston 2004, p.29; Undercoffer, Avancha, Joshi & Pinkston 2002, p.1). Other schemes that have been tried but failed include the autoregression technique which relies on the strength of the signal transmitting data, the network voting algorithm, and the weighted trust evaluation based on trust levels on a hierarchical network (Khalil, Bagchi & Nina-Rotaru 2005, p.96). All the above mechanisms have suffered various weaknesses when used in WSN (Tubaishat, Yin, Panja & Madria, 2004, p.8).
The mechanisms integrated into the WSN network with a triple key management scheme to provide a completely secure network uses a Dual Threshold. In this context, α1 and α2 defined with appropriate trust values are used (Law, Hung, Kwok 1995, p.3440). The mechanism has been proven to provide enhanced node detection performance. The mechanism operates by enabling each sensor node in the wireless network to have trust values updated each time an event occurs to provide the correct report.
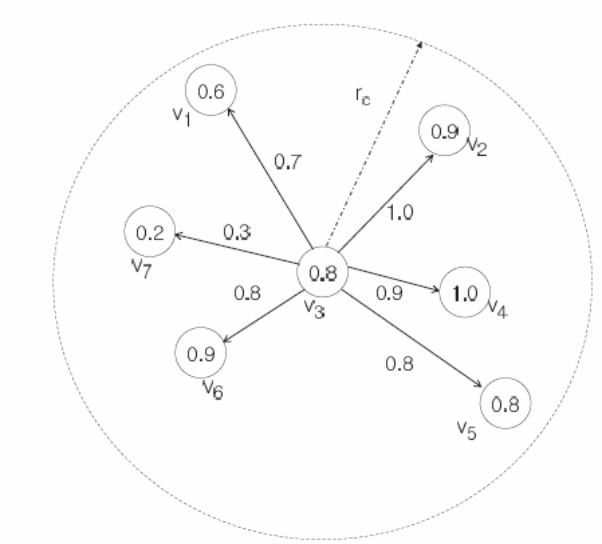
A study by Lazos and Poovendran (2004, p.23) shows that the weighted graph illustrated above shows that weight wij, has values that range between 0 and 1, etc. A typical example where wij =1. Here, Lazos and Poovendran (2004, p.23) show that the corresponding nodes have a trust value is vj as shown above. On the other hand, when the value of wij is equal to zero, there is no trust value and a flag Fi is set to 1. The node is faulty. Detections can be based on distributed events based on the dual-threshold technique (Khalil, Bagchi & Nina-Rotaru 2005, p.88-92; Çamtepe & Yener 2004, p. 300). As mentioned above, there are two thresholds, α1 and α2; with α1 being used to detect an event while ensuring a low false alarm rate exists. On the other hand, the threshold α2 helps nodes that are on or near the boundary region of an event to pass the test reflecting accurately the level of detection as illustrated in figure 4 below.
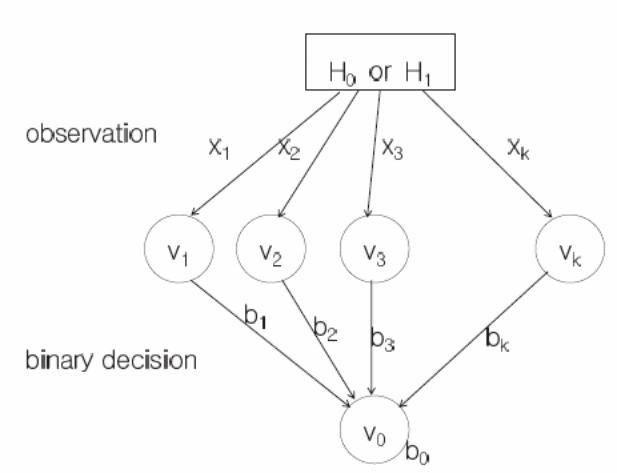
The malicious node detection scheme is summarized in the following pseudo-code.
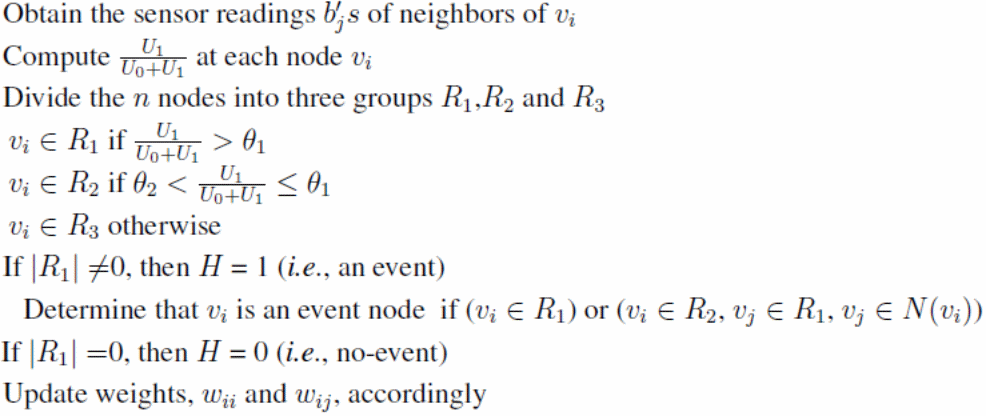
Methodology
The tools installed and used to build the wireless network include nesC [GLVB+03] programming language for TinyOS that defines modules interconnections interfaces, the Sensor Network Application Construction Kit ({SNACK [GKE04]) for node-level abstractions for routing assessment purposes, FABRIC [Pfi07] that defines a service stack for user interface applications, and tiny DB [MFHH05] for databases and data storage for the nodes and TinyDSM [PLP09] allows for caching data.
Node mapping software, RF Monitoring Software for packet sniffing and power level signal monitoring and Nessus vulnerability assessment tool freely available as open-source software are used (Capkun& Hubaux 2005, p.1920).
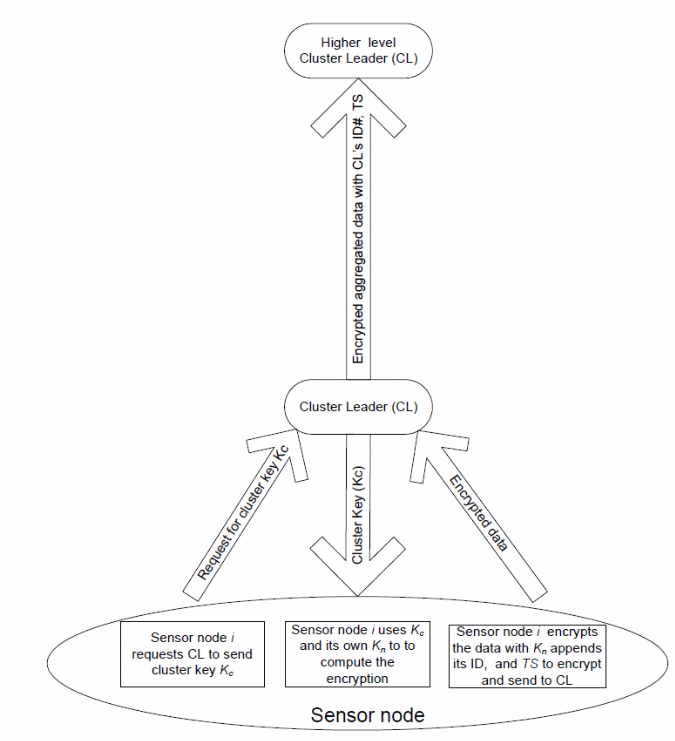
Figure 5 above provides a conceptualized view of the wireless sensor nodes in the network, the communication mechanism that integrates security solutions to ensure data integrity (Chong & Kumar 2003, p.1250; Zhu Xu SSetia, Jajodia 2003, p.330; Zhou, Fang & Zhang 2008, p.20; Zhou, Ni & Ravishankar 2006, p.4).
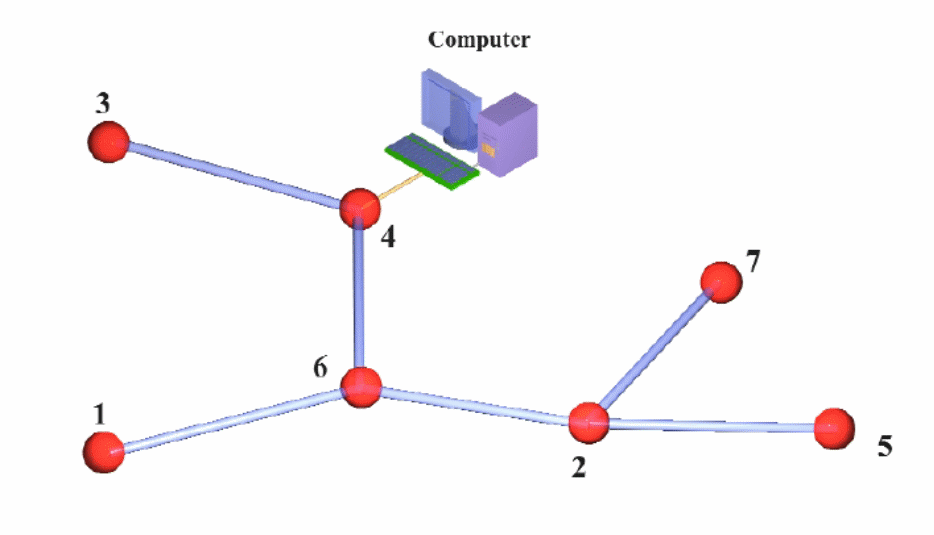
The host PC shown above provides the basis for measuring the time interval involved in the system. The computer generates instructions to the base node to broadcast messages before downloading data from the host node shown in the diagram above (Sharma, Ghosh & Ghose 2010, p.30; Sastry, Shankar & Wagner 2003, p.8; Srinivasan, Teitelbaum & Wu 2006, p.280; Savvides, Han & Strivastava 2001, p.170).
Case study
This paper will be informed by a case study of a wireless sensor network (WSN) used in a military communication environment consisting of a power source, sensor nodes, and a base station, which collects, processes, and analyses data transmitted on the wireless network. The nodes’ drawbacks include low memory, low processing power, power supply, limited routing protocol, and incompatibility with cryptographic schemes used in conventional networks. This WSN uses a combination of one-to-one, one-to-many, and many-to-many communication mechanism using the event-driven TinyOS operating system and Security-Aware ad hoc Routing (SAR) to enable secure routing as shown in the following figure.
Attacks in this network include active/passive (repeated attacks aimed at damaging the network), insider/outsider (can be external or internal with complete access to the network), and mote/lap (having absolute access to sensor nodes). The case uses a combination of dynamic key generation and static key mechanisms to implement system security. The number of nodes in the network dictates the size of the network as shown in figure 9.
The results include the ability to detect malicious nodes, provision of secure packet routing, and avoidance of false nodes as shown in the diagram below.
The security is guaranteed on the WSN mechanism.
The model provides guaranteed security, reliability, and privacy of the wireless sensor network by reducing path loss. Typically, the security is provided at each “sensor node protocol stacks”. Studies by Du, Xiao, Guizani, and Chen (2007, p.230) show that the protocol stack provides different layers of security with the physical layer providing data encryption. The data link layer provides reliable point to point connections between the network nodes with the network layer providing an efficient path for data communication. The uniqueness with the strength of the network is that the physical layer attacks associated with the tempering and jamming of the network, collisions attacks are done on the data link layer of the sensor nodes can be thwarted. Also, “other benefits associated with the triple key management scheme include the strength and ability to thwart hello flood attacks, wormhole attacks, acknowledgement spoofing, and Sybil Attack” (Karlof, Sastry & Wagner 2004, p.172).
Results
Results show that variations in signal strengths are inversely related to the distance between the nodes. The parent nodes always remain aware of their child nodes in the hierarchical WSN. Each node can calculate the time difference between the nodes when the packets are sent and received. Also, directional antennas provide an angular distance between the nodes.
Analysis
A better and constructive method of securing a Wireless Sensor Network is to use a triple key management scheme. The model has a critical advantage over earlier models because the most secure protocol, TinySec, which functions on authenticated encryption on the link layer, overcomes the weaknesses in other protocols because of its architecture and capabilities against spoofing, Sybil attacks, and disallowing bogus routing information to flow through the network. The positive outcomes rely on broadcast packets that hop with guaranteed integrity, authenticity, and confidentiality. Here, the Security-Aware ad hoc Routing (SAR) protocol for discovering secure routes for packets on transmission using the Quality of Protection (QoP) bit vector technique provides more security. The advantage of triple key management is that the system can detect and drop nodes behaving abnormally automatically.
Conclusion
The motivation for this work is the research done on different security protocols and key management schemes and their vulnerability when used in wireless sensor nodes (WSN) using resource staffed nodes that do not allow computationally intensive cryptographic methods. Hostile environments require secure communication that is possible because of clustering, abnormal node detection capabilities, secure triple key management mechanism, and secure routing protocols that provide reliable data delivery. The network provides secure authentication for the nodes, authenticated broadcast, and confidential communication among the nodes. The security and privacy of the network depend on the triple key management scheme.
References
Anjum, F. Pandey S & Agrawal, P 2005, “Secure localization in sensor networks using transmission range variation,” in Proc. of the 2nd IEEE International Conference on Mobile Ad-hoc and Sensor Systems (MASS’05), Washington, DC, USA. IEEE, vol.1, no.2, pp. 194–203.
Anderson, R. Chan, H & Perrig, A 2004, “Key infection: smart trust for smart dust,” in Proc. of the 12th IEEE International Conference on Network Protocols (ICNP’04), Berlin, Germany. IEEE, vol. 4, no.2, pp. 206–215.
Anurag, K S, Rathor, S. Biradar, S R & Ghose M K 2010, Power-efficient Routing & Increased Yield Approach for WSNs, (IJCSE) International Journal on Computer Science and Engineering, vol. 02, No. 03, 2010, 586-592
Biradar, R V & Patil, V C 2011, Special Issue on Ubiquitous Computing Security Systems‖, UbiCC Journal, vol. 4, no.1, pp.15
Blom, R 1984, “An Optimal Class of Symmetric Key Generation Systems,” Advances in Cryptology—Proc. Workshop Theory and Application of Cryptographic Techniques, (EUROCRYPT), vol. 1, no.2, pp. 335-338.
Blundo, C, Santis, A.D, Herzberg, A, Kutten, S, Vaccaro, U & Yung, M 1992, “Perfectly-Secure Key Distribution for Dynamic Conferences,” Advances in Cryptology—Proc. Ann. Int’l Cryptology Conf. (CRYPTO), pp. 471-486.
Boyle, D & Newe, T 2008, ‘Securing Wireless Sensor Networks: security Architectures’, Journal of Networks, vol 3,no. 1, pp 65-77.
Cam, H, Cam, H Muthuavinashiappan, D, Ozdemir, S & Nair, P 2003, “Energy efficient security protocol for wireless sensor networks,” in Proc. of the 58th IEEE Semiannual Vehicular Technology Conference (VTC2003-Fall), Orlando, Florida, USA, vol. 5. IEEE, vol.2, no.2, pp. 2981–2984.
Çamtepe, S A & Yener, B 2004,”Combinatorial Design of Key Distribution Mechanisms for Wireless Sensor Networks,” Proc. Ninth European Symp. Research Computer Security (ESORICS), pp. 293-308.
Capkun S & Hubaux, J.-P 2005, “Secure positioning of wireless devices with application to sensor networks,” in Proc. of the 24th Conference of the IEEE Communications Society (INFOCOM 2005), Miami, USA, vol. 3. IEEE, March 2005, pp. 1917–1928.
Chen, B, Jamieson, K, Balakrishnan, H & Morris, R 2002, “Span: an energy-efficient coordination algorithm for topology maintenance in ad hoc wireless networks,” Wireless Networks, vol. 8, no. 5, pp. 481–494.
Chan, H, Perrig, A & Song, D 2003,”Random Key Predistribution Schemes for Sensor Networks,” Proc. IEEE Symp. Security and Privacy, pp. 197-213.
Chong, C Y & Kumar, S P 2003, “Sensor networks: Evolution, opportunities, and challenges,” Proceedings of the IEEE, vol. 91, no. 8, pp. 1247–1256.
Das, A K 2008, “An Identity-Based Random Key Pre-Distribution Scheme for Direct Key Establishment to Prevent Attacks in Wireless Sensor Networks,” Int’l J. Network Security, vol. 6, no. 2, pp. 134-144, 2008.
Deng, J & Han, Y S 2008, “Multipath key establishment for wireless sensor networks using just-enough redundancy transmission,” IEEE Transactions on Dependable and Secure Computing, vol. 5, no. 3, pp. 177–190.
Du, W. Deng, J. Han, Y S & Varshney, P K 2006, “A Pairwise Key Pre-Distribution Scheme for Sensor Networks Using Deployment Knowledge,” IEEE Trans. Dependable and Secure Computing, vol. 3, no. 1, pp. 62-77.
Du, W, Deng, J, Han, Y S, Varshney, P K, Katz, J & Khalili, A 2005, “A Pairwise Key Pre-Distribution Scheme for Wireless Sensor Networks,” ACM Trans. Information and System Security (TISSEC), vol. 8, no. 2, pp. 228-258.
Du, X, Xiao, Y Guizani,M & Chen, HH 2007 “Effective key management for sensor networks, an effective key management scheme for heterogeneous sensor networks”, Ad Hoc Networks, vol. 5, Issue 1, pp. 24-34.
Eschenauer, L & Gligor, V 2002, “A Key Management Scheme for Distributed Sensor Networks,” Proc. Ninth ACM Conf. Computer and Comm. Security, pp. 41-47.
Gautam, N, Lee, W, Pyun, Jae-Young 2009, “Track-Sector Clustering for Energy Efficient Routing in Wireless Sensor Networks,” International Conference on Computer and Information Technology cit, vol. 2, no. 1, pp.116-121.
Hancke, G P & Leuschner, CJ 2007, SEER : a simple energy efficient routing protocol for wireless sensor networks‖, South African Computer Journal, vol. 39, pp. 45
Ibriq, J & Mahgoub, I 2007, ‘A Hierarchical Key Establishment Scheme for Wireless Sensor Networks’. 21st International Conference on Advanced Networking and Applications, vol. 1, no.1, pp. 210-219.
Hu, F, Ziobro, J, Tillett, J & Sharma, N K 2003, “Secure wireless sensor networks: Problems and solutions,”Journal of Systemics, Cybernetics and Informatics, vol. 1, no. 4, pp. 90–100.
Karlof, C & Wagner, D 2003, “Secure routing in wireless sensor networks: Attacks and countermeasures,” Ad Hoc Network Journal, vol. 1, no. 2-3, pp. 293–315.
Karlof, C Sastry, N & Wagner, D 2004, “Tinysec: a link layer security architecture for wireless sensor networks,” in Proc. of the 2nd international conference on Embedded networked sensor systems (SenSys’04), Baltimore, Maryland, USA. ACM, vol.2, no.1, pp. 162–175.
Kaplantzis, S 2006, Security Models for Wireless Sensor Networks, Web.
Khalil, I, Bagchi, S & Nina-Rotaru, C 2005, “DICAS: Detection, diagnosis and isolation of control attacks in sensor networks,” in Proc. of the 1st International Conference on Security and Privacy for Emerging Areas in Communications Networks (SECURECOMM’05), Athens, Greece. IEEE,vol. 1, no.2, pp. 89–100.
Law, C.-F. Hung, K.-S. Kwok, Y.-K 1995, A novel key redistribution scheme for wireless sensor networks, in: IEEE International Conference on Communications (ICC’07), IEEE Computer Society, Washington, DC, USA,vo.1, no.3, pp. 3437–3442.
Lazos, L & Poovendran, R. 2004, “secure range-independent localization for wireless sensor networks,” in Proc. of the 3rd ACM workshop on Wireless security (WiSe’04), Philadelphia, Pennsylvania, USA. ACM, vol.1, no.2, pp. 21–30.
Lee, J & Stinson, D R 2004, “Deterministic Key Predistribution Schemes for Distributed Sensor Networks,” Proc. Ann. Symp. Selected Areas in Cryptography, pp. 294-307.
Liu, D, Ning, P & Li, R 2005, “Establishing Pairwise Keys in Distributed Sensor Networks,” ACM Trans. Information and System Security (TISSEC), vol. 8, no. 1, pp. 41-77, 2005.
Liu, D & Ning, P 2005, “Improving Key Pre-Distribution with Deployment Knowledge in Static Sensor Networks,” ACM Trans. Sensor Networks, vol. 1, no. 2, pp. 204-239.
Liu, D, Ning, P & Du, W 2008, “Group-Based Key Predistribution for Wireless Sensor Networks,” ACM Trans. Sensor Networks, vol. 4, no. 2, pp. 1-30.
Luk, M, Mezzour, G, Perrig, A. & Gligor, V 2007, “Minisec: a secure sensor network communication architecture,” in Proc. of the 6th international conference on Information processing in sensor networks (IPSN’07), Cambridge, Massachusetts, USA. ACM, vol.1, no.2,, pp. 479–488.
Mittal, N & Belagodu, T 2009, “On Maximum Key Pool Size for a Key Pre-Distribution Scheme in Wireless Sensor Networks,” Int’l J. Computers and Applications, vol. 31, no. 1, pp.23.
Perrig, A, Szewczyk, R, Wen,V, Culler, D & Tygar, J D 2011, Spins: Security protocols for sensor networks. Wireless Networks, 8:521 – 534, 2002. International Journal of Computer Science and Security (IJCSS), vol. 5, Issue 1, pp. 96.
Perrig, A, Szewczyk, R Tygar, J. DWen,. V & Culler, D E 2002, “Spins: security protocols for sensor networks,”Wireless Networks, vol. 8, no. 5, pp. 521–534.
Pietro, R. D. Mancini, L. V. Mei, APanconesi, A &. Radhakrishnan J 2008, Redoubtable Sensor Networks, ACM Transactions on Information and Systems Security, Vol. 11, No. 3, Article 13.
Poornima, A S & Amberker, B B 2009, ‘Key Management Schemes for Secure Communication in Heterogeneous Sensor Networks”, International Journal of Recent Trends in Engineering, vol 1, no. 1, pp. 5-17.
Pottie, GJ & Kaiser, W J 2000,”Wireless Integrated Network Sensors,” Comm. ACM, vol. 43, no. 5, pp. 551-558.
Roosta, T, Shieh, S & Sastry, S 2006,“Taxonomy of security attacks in sensor networks and countermeasures,” in Proc. of the 1st IEEE International Conference on System Integration and Reliability Improvements (SIRI’06), Hanoi, Vietnam, vol.1, no.2, pp. 13–15.
Sastry, N, Shankar, U & Wagner, D 2003, “Secure verification of location claims,” in Proc. of the 2nd ACM workshop on Wireless security (WiSe’03), San Diego, California, USA. ACM, vol.2, no.3, pp. 1–10.
Sharma,K, Ghosh, S K & Ghose, M K. 2010, ‘Establishing an Integrated Secure Wireless Sensor Network System: A New Approach’, International Journal of Next Generation Networks ( IJNGN), vol. 1, no. 1, pp.12-60.
Savvides, A, Han, C.-C & Strivastava, M B 2001, “Dynamic fine-grained localization in ad-hoc networks of sensors,” in Proc. of the 7th annual International Conference on Mobile Computing and Networking (Mobi-Com’01), Rome, Italy. ACM, vol.2, no. 2, pp. 166–179.
Spencer, J. 2000, “The Strange Logic of Random Graphs, Algorithms and Combinatorics 22”, Springer-Verlag, ISBN 3-540-41654-4.
Srinivasan, A, Teitelbaum, J & Wu, J 2006, “DRBTS: Distributed reputation-based beacon trust system,” in Proc.of the 2nd IEEE International Symposium on Dependable, Autonomic and Secure Computing (DASC’06), Purdue University, Indianapolis, USA. IEEE, vol. 1, no.1, pp. 277–283.
Tubaishat, M, Yin, J, Panja, B & Madria, S 2004, “A secure hierarchical model for sensor network,” ACM SIGMOD Record, vol. 33, no. 1, pp. 7–13.
Undercoffer, J. Avancha, S. Joshi, A & Pinkston, J. 2002, “Security for sensor networks,” in Proc. of 2002 CADIP, vol.1, no.2, pp.23.Research Symposium (CADIP’02), Baltimore, USA.
Undercoffer, J, Ayancha, S, Joshi, A., Pinkston, J 2004, ‘Security for Wireless Sensor Networks’, Wireless Sensor Networks, Kluwer Academic Publishers Norwell, USA, vol. 1, no.1, pp. 253- 275.
Varshney, P K 2006 International Journal on Computer Science and Engineering (IJCSE),vol. 02, no. 03, pp. 586-592.
Zia, T.A & Zomaya, AY 2006, ‘A Secure Triple-Key Management Scheme for wireless sensor networks’, in the proceedings of INFOCOM 2006 ,25th IEEE, International Conference on Communications, Barcelona,vol. 1, no.1, pp1-2 ,23-29.
Zhou, Y & Fang, Y 2007, “A two-layer key establishment scheme for wireless sensor networks,” IEEE Transactions on Mobile Computing, vol. 6, no. 9, pp. 1009–1020.
Zhou, L. Ni, J & Ravishankar, C V 2006, “Supporting Secure Communication and Data Collection in Mobile Sensor Networks,” Proc. IEEE INFOCOM, pp. 1-12.
Zhou, Y, Fang, Y & Zhang, Y 2008, ‘A survey of Securing Wireless Sensor network’. IEEE communication surveys, vol. 10, no. 3, pp. 6-28.
Zhu, S. Xu SSetia, S. Jajodia, S 2003, Establishing pairwise keys for secure communication in ad hoc networks: a probabilistic approach, in: Proceedings of the 11th IEEE International Conference on Network Protocols (ICNP’03), IEEE Computer Society, Washington, DC, USA, 2003, pp. 326–335.
