Introduction to the Research
Introduction
The central goal of the proposed study is the comprehensive analysis of the problem of cybercrime and how it impacts the functioning of educational institutions of the UAE, teachers’ work, and their responses to a growing number of threats and risks associated with the issue. The topicality of the chosen question is explained by the increasing role of technologies in the modern world and their penetration to different spheres of human activity. They guarantee multiple benefits for managers and improve outcomes; however, at the same time, numerous loopholes in networks and security systems emerge because of the use of the Internet and diverse software (Dasgupta, Akhtar and Sen, 2020). Malefactors and attackers acquire the chance to interfere with the functioning of various institutions and damage them (European Commission, 2012). Due to its significance, the educational sector also attracts the attention of hackers who might steal or corrupt personal or financial data and precondition the critical deterioration of outcomes. For this reason, there is a need for an improved understanding of the problem, its roots, and strategies how to improve the situation and help managers and teachers to become more effective in struggling against cybercrime (Zhuang et al., 2015). The presented research study offers information related to the issue of concern acquired from reviewing the literature on the topic, the existing gap in knowledge, guidelines, and models that can be employed by teachers to remain capable of resisting the growing threat and protecting students’ personal data. The following section offers the research agenda of the study to understand its scope, main focus, and purposes that should be achieved.
Background and rationale of the study
Cybercrime is worldwide, which is committed in the enormous area known as cyberspace, is dissimilar from numerous other forms of crimes, infrequently researched in the criminal justice system, and can best be explained through a multidisciplinary lens (Payne, 2020). Of late, cybercrime has acquired top priority in organizations across the industry for the express purpose of seamless growth, development, and attainment of the goals (Diffee and Datta, 2018). The cybercrime did not spare educational institutions as well across the globe as well as in the United Arab Emirates (UAE), especially due to the shift of priorities towards online education. However, little is known about the nature and scope of cybercrime in the educational institutions, including the effects cybercrime has on teachers or educators in the UAE (Matsumoto, 2019). Furthermore, there are no clear guidelines on how to act under new conditions and remain capable of preserving the high efficiency of educational establishments in the UAE (Imranuddin, 2017). Moreover, the extant literature suggests an unclear vision of the effective cybersecurity model that can be employed in educational institutions to protect their educators/teachers, which means that they remain helpless (Philip and Salimath, 2018). Therefore, the aforementioned literature suggests a gap in research-based knowledge about both facilitators as well as inhibitors of cybercrime in educational institutions and the need for improved security measures to mitigate this new threat. Such a gap in the extant literature (Diffee and Datta, 2018; Imranuddin, 2017; Philip and Salimath, 2018) serves as the rationale for the study as it is critical to find appropriate measures to resist the growing threat and answer questions linked to the given issue.
The discovered lack of knowledge should be considered a significant problem limiting chances for successful struggling with cybercrime and protecting educational institutions. For instance, the existing body of research offers a limited number of cybercrime models and guidelines that can be adopted to minimize the adverse effects of cybercrime in the UAE educational sector (Diffee and Datta, 2018). It results in the absence of practical approaches to protect data and avoid substantial financial and reputational losses. This gap influences the formulation of the research questions as it is vital to find the practical and relevant frameworks that can be implemented in various establishments to help teachers and avoid being attacked.
Furthermore, the authors devote little attention to the correlation between organizational security culture and cybercrime mitigation. Today, every institution has its own guidelines for resisting threats and protecting its functioning; however, the existing culture might be insufficient and demand change to consider the newest trends and reconsider approaches to managing the problem. Moreover, organizations might have different learning capabilities, meaning that methods to teach specialists and prepare them might vary. Unfortunately, the existing body of research offers limited information on how these factors should be considered to create practical and easy-to-understand models that teachers can employ in various settings (Imranuddin, 2017). For this reason, it becomes fundamental to address these issues and fill the gap in knowledge by answering the research questions formulated regarding the outlined barriers and limits. Structuring information linked to the sphere can be viewed as a significant contribution to the research as it can be used in next projects devoted to similar issues and focusing on better cybesecurity risk management.
Justification of the research problem
As stated previously, cybercrime transforms into one of the major concerns for various institutions today. One of the main problems is the increased vulnerability of private data or information vital for the stable functioning of a unit, such as a financial one. For the educational sector, the problem is also critical because educators have to manage massive amounts of private data related to students and their academic success, payments, or other conditions vital for the educational process. Under these conditions, a specific concern appears.
Cybercrime is all-pervasive in educational institutions across the globe, including the UAE. However, we know little about antecedents of cybercrime in educational institutions, and that poor understanding of it, along with the absence of relevant tools available to teachers, precondition the deterioration of the situation (Imranuddin, 2017; Matsumoto, 2019). Such a prevailing situation calls for the designing and implementation of a cybersecurity model and specific guidelines to arrest cybercrime rates in educational establishments of the UAE.
Altogether, the central research problem of the study is the lack of understanding and guidelines how to struggle with the growing cybercrime rates in specific settings, such as the educational sector. The gap in knowledge related to this field, along with the continuously changing nature of cybercrime, results in the decreased applicability of existing methods and their becoming obsolete. At the same time, the lack of attention devoted to this aspect by teachers, along with the poor support with credible evidence or relevant data, contribute to the growing topicality of the given point. Today, attacks might cause substantial damage to various educational establishments, meaning that there is a need for an immediate solution and strategy to improve their readiness to resist cybercrime and protect data.
The claim linked to the selected problem is that focusing on training teachers and reconsidering the existing organizational learning and security cultures, it is possible to attain better cyber risk management and cultivate a safer environment. Improvement in this field will lead to better work of multiple educational establishments in the UAE and globally, as they all suffer from the increasing number of cyberattacks and experience substantial damage. Under these conditions, designing better guidelines and strategies to resist hackers and their maleficent actions, it is possible to fill the existing gap in knowledge and enrich the current body of research. Otherwise, the disregard of the growing topicality of cybercrime and its negative influence on educational establishments might result in the deterioration of the situation and the use of ineffective methods to protect valuable data. That is why it is vital to conduct the research devoted to the selected problem and improve its understanding.
Furthermore, the given problem statement indicates that the research study touches upon a nagging issue that might deteriorate the functioning of the UAE educational institutions and slow down the speed of their development. The shift towards online forms due to the pandemic and the increased convenience of this model preconditions the growing number of students using the Internet to share their private data and cooperate with teachers. It means that the problem’s relevance and topicality grow every year, and there is a need for specific methods to resolve it.
Research questions
The research study is designed to answer the following research questions:
- How organizational learning capability can be used to attain better cyber security mitigation in the educational sector of the UAE?
- How organizational learning capability and security culture can influence a cyber security mitigation and promote a robust strategy?
They are also supported by the following hypotheses formulated in accordance with the conceptual framework explained in the following parts:
- H1: Organizational learning capability promotes higher knowledge about potential threats.
- H2: Perceived cybersecurity risk directly impacts cybersecurity mitigation.
- H3: Organizational security culture moderates the relationships between organizational learning capability and perceived cybersecurity risk.
- H4: Direct correlation between organizational learning capability and cyber security mitigation is influenced by perceived cyber security risk.
The hypotheses come mainly from the idea that there is a correlation between cybersecurity risk and cybersecurity rates and the organizational capabilities and security of various educational establishments. At the same time, the reduction in the cybersecurity risk can precondition a significant improvement in attaining better results and promote a robust cyber security strategy demonstrated by an organization and guarantee their stable functioning in terms of the digitalization of the environment and the growing importance of online learning.
Research aim
The central research aim of the proposed research study comes from the topicality of cybersecurity and the research statement outlined above. The goal is to examine the influence of perceived cybersecurity risks in educational institutions of the UAE and how dynamic capability can be linked to attaining a better cyber security strategy. Moreover, this research study intends to fill the research gap in exiting literature devoted to the problem of cybersecurity and to outline how the effective guidelines and proposed cybersecurity model can be used to manage and mitigate in UAE educational institutions. The expected results are intended to enhance the concept of cybersecurity in the modern educational establishments of the UAE.
The selected aim is also linked to the research gap identified by using the literature review. The absence of direct guidelines and how they can be used in different settings results in the necessity to offer new ways to manage the growing cybersecurity risks. Under these conditions, it is vital to conduct research in this area. It means that the aim correlates with the problem, its topicality, and the existing research gap.
The aim and research questions form the framework of the study, and their observation is fundamental for achieving the desired outcomes and acquisition of a better vision of how cybersecurity affects the work of different institutions in the UAE functioning within its educational sector.
Research objectives
The aim and the research questions formulated above are supported by the following research objectives:
- Ascertain the current state of perceived cybersecurity risk in educational institutions in the UAE and propose guidelines that can be adopted.
- Determine the correlation between the organizational learning capability and the effectiveness of cybersecurity mitigation in the educational sector of the UAE.
- Define how the existing organizational security culture can influence risks linked to employee negligence and improve cybersecurity mitigation.
- Outline employee related risks and how they can be reduced through learning and organizational culture.
The following research objectives were formulated considering several aspects. First, it is vital to understand the scope of the problem in terms of the UAE educational sector. It will create the basis for the study and help to acquire a better vision of how to improve the current situation. Second, the correlation between organizational learning capability and cybersecurity mitigation is vital regarding attempts to protect existing educational establishments. Finally, the organizational security culture influences decision-making and serves as the critical point determining the effectiveness of attempts to reduce the number of successful attacks. The given objectives, research questions, and the research aim form the research agenda and help to comprehensively investigate the problem under consideration and create the basis for the discussion and future research.
Scope of the study
In such a way, as it comes from the objectives, purpose, and hypothesis of the study, the main focus of the research study is designing the effective cybersecurity model that will help to improve results of the educations establishments in the UAE and guarantee that teachers will remain capable of resisting new threats that emerge every year. The study focuses on the existing gap in knowledge related to the problem under the investigation and how it can be eliminated by offering new methods or protection and evaluating their effects on the functioning of educational establishments. The conclusions and guidelines that will be formulated as a result of the investigation can be necessary for the enhanced vision of how the problem can be managed in modern conditions.
A significant scope of the research is also explained by the importance of the results and formulated framework. Thus, the development of a comprehensive cybersecurity model is vital for the educational sector of the UAE, and, moreover, it can be used by other establishments in different countries because of the universal nature of the problem. Thus, the formulation of the guidelines presupposes the analysis of the main vulnerabilities and factors that precondition their emergence and multiple negative outcomes associated with cyberattacks. In such a way, the scope of the study and its topicality make it a vital research study needed for the cultivation of a safe environment and improved management of cybersecurity in various spheres of human activity.
Novelty of the research study
The study has both practical and theoretical novelty. First of all, there is an attempt to create relevant and effective interventions that would help to alter the situation in the education domain of the UAE and provide managers with tools that are needed to resist cybersecurity. The establishment of the comprehensive model can be viewed as a novel approach for the sector as it considers all existing problems and their diversity, which increases every year. The practical novelty also comes from the fact that additional training for educators means the generation of an improved understanding of how they can be addressed and what methods are the most effective in explaining the new material for them. For this reason, along with the works offering practical tools for preparing educators, the study helps to select among the most effective and working approaches to consider the current learning capabilities and provide organizations with knowledge vital for better cyber risk management. It means that the establishment of the comprehensive model comes along with the methods to integrate it into the work of a certain institution and ensure employees and specialists observe it. It explains the practical novelty of the research and its importance for cybersecurity management and better response to the growing threat.
At the same time, the theoretical novelty of the research comes from several factors. Initially, there is an attempt to analyze the problem of cybersecurity that affects the educational scope of the UAE. Previous attempts were focused on the analysis of the area in general and universal ways to resist it. However, their effectiveness might vary because of the accuracies of the working environment its diversities. The given research study considers the existing cyberattack theory offered by Zhuang et al. (2015) and considers the issue under investigation regarding this framework. However, using the assumptions made by these authors, the research also expands it and contributes to the formulation of new theoretical concepts. For instance, the study accepts the idea offered by Zhuang et al. (2015), presupposing that attackers might focus on some information sets and use them to achieve their goals. At the same time, this assumption is explained in terms of the UAE educational sector and applied to specific settings. It results in generating a better understanding of how unique threats typical for this sector can be managed. Moreover, the theoretical novelty of the research comes from the fact that unlike works by other authors, such as Preis and Susskind (2020), this one views organizational learning and security culture as major determinants of success in struggling with the cyber threat. For this reason, the study broadens the existing body of knowledge and creates the basis for new research studies.
In such a way, the practical and theoretical novelty of the research study justifies the choice of the issue of the research and demonstrates its importance for the educational establishments of the UAE. The educational scope of the UAE experiences multiple changes today because of its fast evolution and growth, and the resolution of the problem of cybersecurity by offering practical guidelines and the security model is critical for the future.
Abridged research method
The study uses the mixed quantitative-qualitative approach supported by the positivist philosophy and deductive reasoning. The choice of this philosophy and paradigm of the research is explained by the need to prove the formulated hypotheses and collect data among educators working in the UAE. For this reason, surveys are viewed as a potent tool to gather information needed for discussion and concluding about the research problem. Qualitative methods are used to conduct a literature review and create a theoretical basis for the research, while quantitative methods are employed to work with selected populations. Non-probability, purposive sampling strategy is also chosen to form a pool of participants. Statistical tools such as SPSS are utilized to process data. A more detailed description of the methodology and justification of choice can be found in the Methodology section.
Structure of the thesis
Chapter 1 introduces the PhD thesis and includes the research background, the research problem, justification of the research, research questions, the aim of the research, hypotheses formulated to discuss the problem, and objectives linked to these hypotheses. It briefly describes the process and its structure.
Chapter 2 offers a literature review about cybersecurity, its types, central risks linked to the problem, and its topicality in the modern educational establishments of the UAE. It also outlines the gap in knowledge on how to mitigate cybersecurity in this environment and delves into possible methods and approaches that can be used address the problem and create a safer environment. Finally, it summarizes the existing body of evidence and creates the theoretical framework for the research.
Chapter 3 describes the conceptual framework of the research study. It shows how the theory impacts the practice and formulation of hypotheses and variables linked to the problem. This part also builds a framework showing relations between variables and hypotheses. Finally, it proves the theoretical and practical coherence of the study, its practical utility, and the ability to promote positive change.
Chapter 4 provides a comprehensive description of the research design, paradigm, methods, and philosophy of the thesis. It outlines peculiarities of the sample, sampling techniques, and data collection and processing methods. Based on the research problem, the mixed qualitative-quantitative approach is viewed as the preferable option. It also touches upon ethical issues and validation of the research, which are integral part of the investigation process.
Chapter 5 provides a list of references used in the research study.
Review of Uae Education Sector, Cybersecurity and Challenges
Introduction
The given section of the study is devoted to the investigation and in-depth analysis of the literature related to the issue under concern. The review has several necessary functions. First, it creates the theoretical background for the discussion and improves the overall understanding of the selected question by outlining the scope of the problem, the cybersecurity rates, existing threats, and current approaches to managing risks that emerge because of the wide use and implementation of technologies. Second, it helps to understand the existing knowledge gap and consider the ways how to fill it by offering specific measures or recommendations. Third, it helps to highlight the current state of the educational sphere of the UAE, including various types of cyber threats and how teachers cope with them. To establish the framework for the discussion, the section offers a comprehensive analysis of scholarly sources linked to similar issues vital for the study, Euro Commission and other agencies’ reports, and secondary sources that can help to collect data necessary for conclusions.
The literature review section also helps to acquire an improved understanding of the potential risks associated with high cybersecurity rates and the inability to manage them in various environments. Because of the focus on the educational sector of the UAE, the review also helps to acquire a better vision of how it evolves in terms of the focus on online learning models and what problems it faces regarding high cybersecurity rates. The sources selected for the analysis are relevant, credible, and offer data that can be trusted. For this reason, the given section is a vital part of the study providing the knowledge fundamental for the discussion and formulating the theoretical framework needed for offering sufficient and practical solutions for the problem of cyberattacks.
Global Situation Regarding Cybersecurity and Growing Concerns
The rise of technologies preconditioned the radical shift in all spheres of human activity. Today, most organizations depend on the stable functioning of multiple departments and the IT-sphere as they are central tools for boosting performance and processing huge amounts of data incoming from different sources (Deloitte, 2018). The employment of innovations and creative solutions helps to attain up to a 100% increase in effectiveness and eliminate barriers to successful growth (Diffee and Datta, 2018). For this reason, technology, networks, and the Internet are viewed as the future of all spheres of human activity. However, the shift towards digitalized means of cooperation created the basis for numerous cybersecurity threats and issues. The sophistication of devices and ways to use them is a two-edged weapon as it also allows criminals to perform more complex crimes and cause substantial damage to all institutions globally (Yar and Steinmetz, 2019). For this reason, the international community looks for new and effective methods and systems to resist cybercrime and ensure the safety of the most important social institutions.
Multiple security agencies are focused on formulating the most relevant challenges linked to the problem. Because digitalization increasingly affects all spheres, it is vital to remain informed about the newest methods to resist emerging threats. The most topical issues include dependence on other parties, lack of cybersecurity expertise, difficulty in detecting cybercriminals, and low populations’ awareness about the current issues (Yar and Steinmetz, 2019). The existence of these problems is evidenced by the growing cybercrime rates and the substantial damage caused by using the Internet and specific devices (Yar and Steinmetz, 2019). Cybersecurity can also be related to major data breaches and the creation of loopholes in existing systems that can be used by third parties. Under these conditions, the world faces a serious threat that cannot be disregarded and demands cooperation and research to find working solutions.
Globally, numerous spheres are affected by cybersecurity and suffer from the growing number of attacks annually. Focusing on the education sphere, it also becomes the attractive target for attackers more often if to compare with previous years (Wilner, 2018). It is preconditioned by the fast digitalization of the sector, the use of innovative devices in educational establishments, and an increasing number of students providing their personal and financial data to institutions via the Internet (Yar and Steinmetz, 2019). Moreover, popular establishments attract the attention of malefactors from various regions because of their reputation and tuition cost. For this reason, students and teachers face a high risk of financial and personal data theft (Philip and Salimath, 2018). Correctly recognizing the topicality of these challenges and their negative impact on the whole sector, specialists emphasize the need for establishing new cybersecurity systems with the more active role of educators who are viewed as vital elements of the framework (Yar and Steinmetz, 2019). The existing body of literature shows that the improved awareness among teachers results in the reduced cyber risks and less significant damage done to institutions by these attacks.
Altogether, cybersecurity remains one of the central concerns for all modern institutions. The shift towards digitalized means of cooperation preconditioned the emergence of opportunities for attackers to use them. Teaches, as the most important actors, are considered responsible for guaranteeing positive outcomes and improving results. However, the existing body of literature emphasizes that it is vital to discuss all emerging threats and inform teachers about them. It remains the only way to help nations resist new issues and avoid problems in the future.
An overview of the United Arab Emirates
Society
The United Arab Emirates is one of the fast-growing nations and plays a more significant role at the international level every year. The rich natural resources, their strategic importance, and the extensive development of industries created the basis for radical shifts in the country and its society. The UAE is a predominantly Muslim country (Sunni Muslims), and the social life, along with political issues, is impacted by the Sharia Law (About the UAE, N.D.). However, the state focuses on the promotion of tolerance and equality and promotes religious freedom. The expatriate population includes Christians, Hinduists, and Buddhists (United Arab Emirates, N.D.). The country is characterized by the clearly defined difference between social classes as there is a divide between Emirati Nationals and the immigrant population (United Arab Emirates, N.D.). Most of the finances and power are distributed between representatives of this group.
Society also has a high level of income, improved quality of life, developed infrastructure, and vital social institutions, such as education and healthcare (United Arab Emirates, N.D.). As against other countries in the region, the UAE gives much attention to gender roles and the provision of equal rights to men and women, including them in social processes (About the UAE, N.D.). In general, the last decades can be characterized by radical changes in the UAE society vital for its further evolution, increasing power at the international level, and acceptance by other countries as one of the major players from the Middle Eastern region.
Economic outlook
The UAE possesses a fast-growing and potent economy with multiple opportunities for further growth. Currently, the state has the second-largest economy in the Middle East, with a GDP of $354 billion (United Arab Emirates, N.D.). It demonstrates that the nation is focused on creating the basis for further development and future rise. For a long period of time, the oil industry had remained the major source of income, with the state critically dependent on oil prices (United Arab Emirates, N.D.). However, today the UAE puts much effort into diversifying the economy by promoting new industries such as technologies, tourism, service business. The success of these strategies is evidenced by the fact that the UAE is ranked among the 20 for a service business (United Arab Emirates, N.D.). Additionally, the state promotes the evolution of small and middle enterprises to diversify its economy and decrease its dependence on revenues from petroleum and natural gas (United Arab Emirates, N.D.). For this reason, the company has the resources and basis for investing in new products, services, and digitalization of the central activities.
The political context
The United Arab Emirates is a federation of seven constituent monarchies. It includes the Emirates of Abu Dhabi, Ajman, Dubai, Fujairah, Ras al-Khaimah, Sharjah, and Umm al-Quwain (United Arab Emirates, N.D.). The UAE functions in terms of the federal, elective, and constitutional monarchy, with the President of the UAE as the head of the state. There is also the Prime Minister of the UAE who leads the government. The country does not have political parties. The Federal National Council consists of 40 members, with 20 appointed by the rulers of Emirates and 20 indirectly elected (United Arab Emirates, N.D.). The overall political situation can be described as a stable one. The country adheres to a political course presupposing the development of the state and the alignment of improved cooperation with the rest of the world. The President also supports the incentives vital for the socio-economic development of the state and its gradual empowerment.
The socio-economic development
The state devotes much attention to its socio-economic development as a vital part of its growth. The UAE has the top indicators regarding the factor due to the effective policies and potent financial regulations. The nation managed to achieve better progress than Britain, Japan, and France in the sphere of fiscal efficiency and reporting (About the UAE, N.D.). It creates the basis for the effective evolution of social and business spheres. Moreover, the credibility of officials and the level of trust for them is high (78%), proving the potency of introduced measures (United Arab Emirates, N.D.). One of the distinct features is the promotion of innovations and technologies in all spheres of human life. The UAE supports programs presupposing the wide use of devices and creative solutions to improve the quality of life and introduce new comfort levels for citizens (United Arab Emirates, N.D.). The outstanding progress can be seen in such spheres as healthcare, education, and infrastructure, characterized by the extensive use of technologies. In such a way, the country invests much of its income from the developed industry into the cultivation of the socio-economic sphere to improve the quality of people’s lives.
Long term and short term goals of the UAE
The UAE has established several critical goals to outline the vector for its further evolution. First, the country aims at establishing food security by decreasing the country’s dependence on imported products (United Arab Emirates, N.D.). It presupposes the cultivation of the local production and support to manufacturers who can guarantee stable supplies. Second, the nation focuses on innovating all spheres of life and industries to support its further rise. It can be achieved by financing in the high-tech sector and encouraging new research studies. The long-term goals also include the diversification of the economy to reduce the dependence on oil and petroleum as it will improve the country’s security and avoid crises preconditioned by differences in prices (United Arab Emirates, N.D.). The UAE also outlines the importance of fostering the rise of its education to prepare skilled and experienced specialists who can contribute to the development of the economy and its diversification (United Arab Emirates, N.D.). In such a way, the existing goals are focused on increased security of the state and reduction of its dependence on external factors.
An overview of the UAE education sector
Key education trends in the UAE
As stated previously, the UAE is now transforming into a knowledge-based economy, focusing on implementing technologies to attain better outcomes. For this reason, there is a significant increase in the number of educational institutions offering programs at all levels to ensure that the country is supplied with the demanded number of specialists (About the UAE, N.D.). The government, local regulators, and agencies support the given trend and encourage educators to create new courses and attain better outcomes. For this reason, due to the combined efforts of the government and local actors, the UAE has an evolved educational ecosystem characterized by multiple opportunities for students to acquire desired skills and knowledge (About the UAE, N.D.). The education trends focus on the most effective and new techniques and strategies supported by technologies to achieve desired academic results and guarantee the shift to a knowledge-based economy supported by local specialists. For this reason, the state is also focused on creating of safe digitalized environment vital for the cooperation between institutions and their further rise.
Levels of education sector
The educational system of the UAE is represented by private and public schooling. Primary and secondary education is compulsory for all citizens and is free. Thus, there are several levels of education peculiar to the state. First, kindergartens include children to 6 years and help them to evolve their basic skills such as reading, singing, writing (Sergon, 2020). Primary education is the next level, which is also compulsory in accordance with the existing laws, and it continues developing students’ skills (Sergon, 2020). The next stage is preparatory education, with the length of the program of about three years needed to prepare pupils for the next step, which is secondary education (Sergon, 2020). Statistics show that 40% of all pupils attend private schools, which are extremely popular in the UAE (Sergon, 2020). Having passed these stages, students can enter the University or other educational establishments of their choice. This multi-layered system guarantees the appropriate education of citizens and also helps them to acquire skills and knowledge vital for further success and academic achievements in different areas.
Policy issues relating to the UAE education sector
The major policy issues related to the UAE educational sector revolve around the reforms that are introduced to meet the UAE National Agenda goals 2021 and build the teacher capacity by fostering innovative change. Fist, the government promotes the massive digitalization of education and use of innovations to attain better outcomes and increase the autonomy of learners (Sergon, 2020). It is expected that such practice will contribute to the positive shifts the educational ecosystem and align the improved cooperation between teachers, students, and other stakeholders of the process (Sergon, 2020). Moreover, creation of the world-class system emphasized by the national agenda presupposes the improved data collection to outline the current problems and resolve them. For this reason, the Ministry of Education attempts to align the national network for educational establishments to improve data and experience sharing and help to reform the sphere by introducing appropriate changes when needed and supporting the high level of digitalization and innovation in all institutions. At the same time, there is still a serious gap in policies and regulations related to the monitoring of new guidelines’ implementation and protection of institutions in terms of increased importance of cybersecurity.
Impact of cybercrime on education sector
Cybercrime in the UAE educational sector
Narrowing the research and following the research objectives, it is vital to focus on cybersecurity in the UAE educational sector. The fast pace of its evolution and the increase in the quality of teaching attract the attention of researchers to the given field. Jiang and Rafeeq (2019) stated that the recent developments in communication technology were widely implemented in various institutions of the UAE and precondition its transformation. Today, multiple digital media platforms are used for educational purposes to align the cooperation between students and educations and ensure that they can benefit from this model (Jiang and Rafeeq, 2019). Matsumoto (2019) supported this statement and emphasized that as a relatively new country with a powerful economy, the UAE attempted to achieve the top global status in education. For this reason, the nation puts much effort and resources in transforming and digitalizing the education sector for it to remain demands to innovativeness and quality (Nuzhat, 2020). Moreover, the state focuses on globalizing its education to provide students with opportunities to meet their peers from different regions, share experiences and knowledge.
The achievement of these goals presupposes the extensive use of communication technology, social media, messengers, video communication, media platforms, and databases containing vital information critical for the process (Nuzhat, 2020). Under these conditions, cybersecurity breaches acquires the top priority as one of the issues that might prevent the sector from its further evolution. Cyber specialists report an increase in email compromises preconditioning the extortion and diverse ransomware attempts (Barfoot et al., 2020). Moreover, there is a constantly increasing risk of student and teachers’ impersonation because of reduced control and lack of protective measures (Barfoot et al., 2020). Imranuddin (2017) outlined the three types of common risks affecting the educational sector of the UAE, which were data theft, DDoS attacks (Distributed Denial of Service), and espionage, which threatens the intellectual property of higher institutions and might precondition failures in their functioning.
In such a way, for the UAE, the ability to protect its education system from cybersecurity acquires the top priority as one of the major tasks needed to support the high pace of evolution. Personal information, including birth records, educational history, social security, financial data, and intellectual property, should be protected by using innovative approaches available at the moment (AMEinfo Staff, 2020). Administrators, policymakers, and educators are viewed as the major actors responsible for achieving this goal. However, some problematic issues should be highlighted in terms of this task.
The current state of the problem of cybersecurity. Origins and definition
A review of the literature on cybersecurity and its impact on the modern world shows the tendency towards the growing importance of the given issue and the need for specific measures to manage risks associated with it. Thus, a report published by European Commission (2012) stated that about 53% of people in Europe used the Internet at least once a day, while only 29% reported the absence of access to this source. Moreover, 95% of all respondents use it at home, 39% at work, and 11% at schools or universities (European Commission, 2012). The report also shows that 53% of respondents use the Internet to buy various products, share critical data, such as financial or private ones, or for work and study purposes (European Commission, 2012). The given numbers demonstrate that the rise in technologies stimulates the rapid increase in the number of Internet users because of the availability of devices guaranteeing access to various networks.
In the UAE, a similar situation can be observed. During the last two decades, the government devoted much attention to developing the digital environment of the UAE. Due to the positive policies and significant financing, the country has transformed into the most developed and digital-friendly country in the Middle Eastern region (GMI, 2020). Statistics show that 99% of the population are active Internet users with constant access to the network during a day (The World Bank, 2019). 97% have active social accounts, and 92% use their mobile devices to acquire access to the Internet (Statistics about Internet in United Arab Emirates, N.D.). Moreover, 99% of the UAE citizens view the Internet as a potent and convenient tool to work, study, and share financial data, presupposing making purchases online, mobile banking, or other types of activity (Statistics about Internet in United Arab Emirates, N.D.). The numbers prove that the UAE, as the rest of the world, is characterized by the extreme digitalization of the environment and the omnipresent nature of the Internet.
However, along with multiple benefits guaranteed by the spread of technologies, there are also diverse risks linked to the process of digitalization of the environment and the dominance of the Internet. Aydos, Vural and Tekerek (2019) stated that the Internet of things, or a new generation of networks created by intelligent objects equipped with software and sensors, might pose a threat to the security of data. The integrated features of the Internet of Things, such as improved data processing capabilities, the ability to customize and collect information about users, along with its use in health, education, and financial spheres, make it the target of cyber threats and attacks (Aydos, Vural and Tekerek, 2019). In such a way, the boost in technologies is also followed by the emergence and the growing importance of cybersecurity as a new serious concern of contemporary society. Kremling and Parker (2017) defined the term as the use of a computer as a tool to perform illegal actions mainly by using the Internet and cause substantial harm to intellectual property, violate privacy, or steal critical data that can be used for diverse purposes. Holt, Bossler and Segfried-Spellar (2017) had a similar definition, emphasizing the fact that cybercrime through the Internet had acquired additional importance as computer technologies became fundamental for commerce, entertainment, education, and government.
The problem originated from the first hackers’ attempts to illegally access high-level computer networks for their own goals and has evolved into a complex and sophisticated sphere characterized by the existence of multiple ways and strategies to cause damage or generate benefit by employing loopholes in security systems (Yar and Steinmetz, 2019). In the 21st century, the issue became a global threat as there is no country or area with access to the Internet that had not been touched by hackers (Holt, Bossler and Segfried-Spellar, 2017). In such a way, the growth of technologies, the increasing affordability and availability of the Interment, its sophistication, and the emergence of new smart constant learning applications provided malefactors with new tools to affect the functioning of companies or individuals (Cyber safety and digital security, N.D.). The computer transformed into the instrument for illegal ends, and cybercrime is viewed as the criminal behavior belonging to novel illegal activities demanding strong responses and policies to manage them.
Significance and scope of cybersecurity. The major issues
The existing body of evidence accepts the critical importance of cybersecurity for the modern world and its outstanding significance. Department for Digital, Culture, Media and Sport (2018) reported that four in ten businesses (43%) and two in ten charities (19%) were attacked by hackers in the last 12 months. The same report states that the average cost of data lost because of cybercrime activities was about $13 million in 2018, which is $2 million more if to compare with $11.7 million in 2019 (Foster, N.D.). The numbers indicate that the average cost of cybercrime continues to grow and now comprises about $27.4 million (Foster, N.D.). The nagging character of the problem is also evidenced by the fact that only in the first half of 2020, 540 breaches of security impacting 164 million people were detected (Foster, N.D.). The given growth in the activity of hackers and third parties using the Internet and technologies to cause damage is associated with the COVID-19 pandemic, which increased the number of people working from home (Foster, N.D.). Criminals might use the personal information previously acquired as a result of the breach to commit new crimes. For instance, 780,000 records were lost per day in 2017, which provided hackers with new opportunities to interfere with the functioning of organizations (Foster, N.D.). It is expected that by 2021, cybercrime will cost about $6 trillion annually because of the tendency towards the diversification of threats and strategies used by criminals (Foster, N.D.). About 24,000 malicious mobile apps designed for stealing passwords (around 300 billion worldwide) and personal data are blocked every year (Department for Digital, Culture, Media and Sport, 2018).
As for the UAE, the recent review shows that there are about 2.5 million people who can be seen as victims of cybercrime (Foster, N.D.). Although there are attempts to reduce the risks, people still engage in online behaviors that might precondition the loss of data or breach of privacy. Because of the high number of Internet users in the country (97%), the problem becomes especially topical for the UAE, with its shift towards digital technologies and the use of online models for education, business, and cooperation. Moreover, being one of the fast evolving-nations, the country attracts the interest of attackers who want to generate money by stealing data about financial operations. Under these conditions, for the UAE, the problem also remains topical, and its scope continues to grow.
The statistics provided above make cybersecurity one of the major goals of diverse organizations today. 74% of all businesses and 53% of charities devote their prior attention to organizing and managing cybercrime as the factor that might cause serious damage to their functioning (Department for Digital, Culture, Media and Sport, 2018). Moreover, 33% of all companies have their own policies and frameworks designed for working in terms of the high importance of cyberattacks and substantial cause that can be associated with them (Department for Digital, Culture, Media and Sport, 2018). These are created to prevent attackers from harming the business and remain resilient to the most frequent cybercrimes. They are phishing scams, identity theft scams, online harassment, cyberstalking, and invasion of privacy, including data theft (Department for Digital, Culture, Media and Sport, 2018).
For this reason, the major issues of cybercrime come from its scope and significance. The fast-changing nature of the digital environment means that there is always a high risk of new breaches and loopholes that can be used by hackers. Attackers fast adapt to new conditions and employ innovative solutions to interfere with the work of a company. In general, it takes about six months to notice a data breach, which means that criminals have enough time to perform their actions. Under these conditions, the main tasks linked to cybercrime today is to guarantee the potent work of security systems and their ability to work in stressful situations. Unfortunately, there is a certain deficit in guidelines and cybersecurity models applied by managers working in different spheres as the existing ones are either extremely specialized or too broad and universal to be employed by every sphere.
The growing need for effective security measures
The need for sufficient security measures mentioned previously comes from several factors. First, digital transformation is nowadays a global phenomenon that influences every part of society and introduces multiple opportunities and risks (Government Offices of Sweden, 2017). Management of these risks has a potent effect on the ability to maintain and enhance prosperity and security (Government Offices of Sweden, 2017). The scope of the problem and its significance means that the question of cybersecurity is topical for the whole society as there is a need for a collaborative effort to resolve challenges and create a safe environment (Government Offices of Sweden, 2017). The cooperation between the public and private sector is a key to the creation of resilient and potent systems with an opportunity to resist emerging threats and remain capable of evolving in time (Kremling and Parker, 2017). Additionally, because of the global nature of the issue, the challenges of cybersecurity are shared with all countries that should take part in the dispute and elaborate on preventive measures, strategies, and tools to empower cybersecurity efforts (Government Offices of Sweden, 2017).
Another factor explaining the need for effective security measures is the continuously increasing demands on society’s cybersecurity and the accelerating pace of new threats; emergence. At the same time, the evolution of technologies and science makes the scope of threats more significant and extremely difficult to detect (Kremling and Parker, 2017). Moreover, new risks pose and additional difficulty related to assessment and their evaluation (Payne, 2020). In such a way, nations respond by offering regulatory changes and measures to increase their ability to resist a wave of cybercrime and continue their evolution (Kremling and Parker, 2017). The structured and risk-based approaches to cybersecurity are vital for the further transformation of society and increased effectiveness of both private and public sectors.
Finally, the growing need for security measures is explained by the advantageous nature of technologies, which fosters their penetration in various spheres of human activity and becoming irreplaceable considering new opportunities guaranteed by them. Banking, defense, education, science, industrial, and multiple other sectors critically depend on the stable functioning of systems that are integrated into their functioning (Government Offices of Sweden, 2017). For this reason, with the further evolution of digital devices and the digitalization of society, the question of how to protect technologies will become more topical. Digital transformation is one of the fundamental changes society witnesses today and has an extremely potent influence on the future of society. For this reason, it is critical to remain at the forefront of technological development and support it with appropriate cybersecurity measures that will help to avoid the emergence of new loopholes.
Organizations’ performance and cybersecurity
The existing literature on the issue outlines the direct correlation between cybersecurity and organizations’ performance. First of all, cybersecurity serves as the source of instability and the emergence of problems with management, organization, and finances. Dasgupta, Akhtar and Sen (2020) stated that the lack of effective cybersecurity guidelines and systems that could protect units from attacks might reduce their effectiveness by 50% and precondition their collapse. Because of the fundamental role of technologies for private and public sectors, their stability is critical for the achievement of desired goals and their ability to generate competitive advantage (Kremling and Parker, 2017). Additionally, online banking and transactions made every day means that the security of financial data also acquires the top priority for organizations and their performance (Payne, 2020). Under these conditions, the relationship between results and cybersecurity rates becomes evident and should be given much attention as a way to guarantee the stable work of various sectors.
The question becomes extremely topical for fast-evolving nations focusing on the digitalization of their economies and business sector. For instance, the UAE is viewed as the state with a favorable environment vital for the development of companies and the integration of technologies into their work. For this reason, the majority of companies and organizations in the state function by massively using the Internet and online tools that help them to achieve higher levels of excellence and generate a competitive advantage. It becomes one of the major features of the economy there; however, at the same, time this digitalization increases the vulnerabilities of various organizations to hackers and their actions. That is why, for the UAE, the creation of a robust and effective cybersecurity model is a way to enhance organizational performance and achieve better results in various spheres.
In such a way, the majority of authors agree that the modern digitalized society offers multiple opportunities for companies and organizations of both public and private sector to generate additional revenue by using technologies and computers (Kremling and Parker, 2017). Because of the hazardous online environment, these actors can also suffer from hackers’ attacks and cybersecurity rime committed with various purposes. Under these conditions, the existing body of evidence proves the direct correlation between organizational performance and cybersecurity. The given statement is also applicable for the educational sector, which becomes especially vulnerable to this sort of attack in terms of a pandemic affecting all regions of the world and preconditioning the shift towards the online models of learning.
Cyber risks in the education sector
Educators/teachers’ vulnerability to cyberattacks
Considering the significant scope of the problem and its ability to affect multiple organizations and cause serious damage, the researchers working in the field insist that not only IT staff should be responsible for dealing with this new challenge. Thus, Castelo (2020) assumed that administrators, educators, and school employees should be provided with the information necessary to understand the topicality and importance of cybersecurity. Otherwise, these specialists remain critically vulnerable to cyberattacks and can be viewed as the weakest part of the security systems (Castelo, 2020). Moreover, the decreased motivation levels linked to this factor can deteriorate their performance (Williams and Anderson, 1991). The recent survey outlines that only 15% of all educators correctly realize the scope of cybercrime and have the understanding of how to work on the Internet safely, while most respondents are sure that the IT workers should be responsible for organizing their online meetings or classes (Castelo, 2020). This vision transforms educators into the victims as hackers see them as easy targets for their attacks (Castelo, 2020).
Another problem increasing the teachers’ vulnerability is their unpreparedness to functioning in new digitalized environments. Specialists aged 50 and higher might experience multiple difficulties using a computer or the Internet to cooperate with colleagues or students from other locations (Payne, 2020). Along with the poor understanding of technologies, this cohort also lacks the idea of how malefactors can affect their work and the functioning of institutions by using their devices (Payne, 2020). It results in the emergence of dangerous situations and the appearance of loopholes that can be used by attackers to pursue their goals and generate benefits (Castelo, 2020).
In such a way, the literature proves that educators remain critically vulnerable to new forms of attacks that become topical today. One of the factors impacting the given vulnerability is the absence of clear guidelines and training available for teachers and helping them to feel safe and act wisely when using the computer with access to the Internet (Payne, 2020). In the UAE, the reform tries to correct the given situation and establish a digitalized environment; however, little attention is given to creating potent security models or sufficient guidelines to minimize educators’ vulnerability and make them active participants vital for security incentives and their implementation.
The gap in knowledge about facilitators and inhibitors of cybersecurity
Analyzing the problem of cybersecurity and the ways to solve it, Leukfeldt and Holt (2020) concluded that the low effectiveness of existing measures in educational institutions was explained by the poor knowledge of factors that might promote or restrain cybercrime. For instance, the survey among teachers with at least 3-year-experience shows that only 10% of them possess information about inhibitors of cybercrime that can be used in the real-life environment (Castelo, 2020). The same gap exists when speaking about the facilitators of this negative practice. In such a way, the given deficit in knowledge can be viewed as a problem reducing the effectiveness of security systems and measures implemented by the IT staff.
Thus, the poor understanding of facilitators and inhibitors of cybersecurity undermines the effectiveness of prevention strategies and limits the number of situations when they can be applied. Leukfeldt and Holt (2020) are sure that prevention strategies are the most effective ways to resist cybersecurity breached and minimize the chance of being attacked; however, they can be applied only if the staff is aware of the factors that might create the loophole in existing systems or, on the contrary, how to avoid being attacked by using specific applications. Moreover, Preis and Susskind (2020) outlined the necessity to familiarize all community members with strategies that could help to resist hackers as a way to improve municipal security. It means that the lack of information about this issue might have an extremely negative effect on outcomes.
For the educational sector of the UAE, the given gap in knowledge also remains topical. Imranuddin (2017) reported that the lack of understanding of how to avoid being attacked in terms of the UAE educational sector. It means that educators remain incapable of using protective software, such as anti-viruses or anti-phishing applications, to protect personal data, passwords, or information provided by students. Moreover, some of them find recommendations offered by the IT staff too complex to follow (Payne, 2020). Under these conditions, the lack of knowledge affects the work of the sector and undermines its ability to resist threats relevant today.
Cyber threats peculiar to the educational sector
As stated previously, the literature devoted to the issue emphasizes the importance and frequency of several types of threats observed in the educational sector today. DDoS attacks are common for all levels of education venue and are performed with the primary goal to disrupt the work of an institution, minimize its productivity, and precondition its inability to provide services to clients (Payne, 2020). The main problem associated with DDoS attacks is that they can be performed by amateurs if no robust security systems are used by the establishment to protect itself. Moreover, students and teachers can perform such attacks for various purposes, including the desire to show their protest or to have a day off (van de Weijer, Leukfeldt and Bernasco, 2019).
Data theft is another type of maleficent actions admitted by researchers. Kremling and Parker (2017) determined it as an attack influencing all levels of education as institutions had student and staff data, including critically important details such as addresses that could be used for various purposes. The cybercriminals can offer this data to third parties or extort money with its help. Kremling and Parker (2017) also stated that it could remain unnoticed for a long time, making it more dangerous for institutions.
Financial gain is linked to data theft and is viewed as one of the essential concerns affecting the education sphere today. Because of online models, institutions often have to deal with a high number of student fees and payments, which becomes an issue of interest for cybercriminals (Payne, 2020). Parents or learners pay via an online portal transferring huge sums of money to pay for the year of study (Al Ahbabi, 2019). The lack of appropriate protection might result in intercepting these sums by attackers and the critical damage to the institution (van de Weijer, Leukfeldt and Bernasco, 2019). For private schools, colleges, and universities, the problem becomes even more significant as the fee is higher, and the potential damage becomes more substantial.
Finally, espionage is another cybercrime that is associated with the educational sector. Most higher education institutions are also research centers that might possess valuable intellectual property that might attract cybercriminals acting at the request of third parties (Payne, 2020). For this reason, such institutions should be protected from attacks on their networks as it might precondition data leaks and the failure of projects presupposing participation of multiple students and educators (van de Weijer, Leukfeldt and Bernasco, 2019).
The analyzed literature emphasizes the critical importance of these threats because of their ability to impact educational embellishments’ functioning and cause substantial harm. Thus, for the UAE, the given threats also remain topical because of the global nature of cybersecurity and the ability of malefactors to act from various regions and interfere with the functioning of institutions located in distant areas. Reports show that about 65% of the UAE’s institutions were attacked by cybercriminals at least once (Al Ahbabi, 2019). For this reason, the problem remains extremely topical today.
Students’ and financial data loss
The risk of financial data loss because of data theft increases every year and poses a significant threat to the educational sector. Mello (2018) said that one of the aspects complicating the situation was the absence of full and consequent investigations of educational institution data breaches, which meant that multiple questions should be answered to improve the situation. Moreover, Mello (2018) emphasized that these substantial losses linked to the inevitable vulnerability of institutions increase the importance of consequences’ management and the ability to recover from such intrusions. For instance, students’ financial data and their payments are endangered because of the activity of cybercriminals and their focus on intercepting information that can be used to acquire this money (Mello, 2018). For an educational establishment, the loss of tuition payment might be a severe strike because of its dependence on these sums. Because online payments and teaching models become one of the main forms of cooperation between a student and an educator, the need for protective measures becomes the top priority for the sphere today.
Unfortunately, although the number of breaches increases, the public sector remains underresearched compared to the private one. Mello (2018) assumed that the lack of information was linked to the complexity of data collection and investigation in this sector and the need to gather governmental support to acquire clear details on recent hackers’ attacks on educational establishments. The existing study on government data breaches shows that human incompetence and software weakness were the most common breach type (The National, 2020). At the same time, the nature and frequency of these attacks can hardly be determined because of the lack of a unified reporting system vital for risk assessment and data collection (Mello, 2018). For instance, according to Mello (2018), in the education sector, educational establishments hold personal data on students, faculty, and finances and possess the low capability of processing them to find possible breaches.
In such a way, schools, colleges, and universities suffer from the high cost of data breaches involving financial data loss. A study by Ponemon Institute shows that an average cost constitutes about $200 per record, and even higher, about $260 per record in private organizations (The National, 2020). The costs might differ regarding the extent of a breach, time needed to identify it and harm it does to the institutions (The National, 2020). Under these conditions, it becomes critically important to prevent students’ data loss and protect it using innovative methods. However, the lack of knowledge and research in the sphere introduces additional complexity.
The lack of guidelines regarding cybersecurity in the UAE
The recognition of the growing threat associated with cybersecurity and its importance for the educational establishments in the UAE results in the increased attention to the problem and attempts to resolve it. Unfortunately, there is still a deficit of knowledge related to the question under research. The given literature review finds a lack of guidelines linked to cybersecurity and teachers’ behaviors and strategies that might help to resist it. For instance, Imranuddin (2017) stated that because of the significant education reform in the state, many teachers possessed a vague understanding of how to act under new conditions and remain effective. Matsumoto (2019) agreed with the given statement and added that there was still an insufficient vision of cybersecurity in the majority of educational establishments across the country, its roots, and factors that might precondition the growing rates of attacks. The problem is complicated by the fact that teachers and educators do not have tools, such as guidelines or cybersecurity models, that can help them to be resilient and capable of protecting the data of their students (Imranuddin, 2017; Matsumoto, 2019). For this reason, the situation becomes dangerous as the given gap in knowledge might have long-term negative effects on the sector.
Furthermore, speaking about attempts to improve schools’ effectiveness, Al Ahbabi (2019) said that in the majority of cases, little attention was devoted to the problem of cybersecurity as it is not viewed as a significant one. The given statement indicates a lack of understanding of how hackers can affect the functioning of schools and universities and prevent them from achieving their goals. The recent reform contributed to the creation of the digitalized environment that can help the sector to join the international discourse; however, at the same time, the pool of specialists and their vision of the current problems remained unchanged (Imranuddin, 2017). Teachers of all levels still disregard security measures when working online or use unsafe programs or applications during their work.
The given factors evidence the existence of a certain gap in knowledge about guidelines and security systems that can be used by educators and teachers working in the given sphere to attain better outcomes and protect different types of data from theft. This knowledge deficit might have a long-term impact on the whole sector and limit its opportunities for further rise because of substantial harm that might be caused by malefactors by using the Internet if no effective measures are employed (Parsons et al., 2015). The existing literature evidences that there is a need for the creation and integration of a robust cyber security strategy and guidelines that will equip senior decsion makers with tools needed to resist cybersecurity and its various forms while working in the digitalized environment (Imranuddin, 2017; Matsumoto, 2019; Payne, 2020).
Challenges of cybecrime
Major challenges to protecting education sector from cybercrime
Along with the lack of information about the effective methods of protecting data in the education sphere and the gap in knowledge about guidelines, some other challenges make the task to protect education from cybercrime more difficult. The authors, such as Matsumoto (2019), Imranuddin (2017), Wilner (2018), emphasized that modern institutions cultivated a culture of openness and welcome new people to join their communities. The same situation is observed in the UAE educational sector as universities encourage students from all regions to become active participants in activities organized online (Imranuddin, 2017). It becomes the first serious barrier to protecting the education sphere as the focus on the free exchange of information introduces multiple vulnerabilities that can be used by cybercriminals for various purposes (Wilner, 2018). Combined with the lack of awareness among students and staff about technology and limited technical skills, these two factors contribute to the growth in cybercrime rates.
Other serious barriers emerge because of the diversification of the sphere and its transformation into a global entity. Matsumoto (2019) stated that with the reform of education in the UAE, it became internationally oriented, which contributed to the high distribution of learners across different regions and, at the same time, introduced additional sophistication to the sphere. Another challenge comes from identity management, as users might have diverse roles in a system of an educational establishment, with different levels of authorization and access (Matsumoto, 2019). For this reason, there is no single application with the opportunity to manage student and educators’ identities, which might be used by malefactors to cause damage. Imranuddin (2017) also assumed that the educational sector had a unique environment characterized by the need to provide remote access to all stakeholders of the process, including students, parents, and educators from home computers and smartphones. The IT staff of institutions cannot control these devices, which means that increased risks of breaches emerge.
Finally, service users change every year because of their graduating and the appearance of new learners. It introduces new challenges of account management and the need to constantly update databases to avoid using obsolete information or relying on irrelevant data (Wilner, 2018). Altogether, the given factors make the sphere of education extremely vulnerable to attacks and, at the same time, demand a special approach to security as the integration of robust protocols should be aligned with the culture of openness vital for the sphere and needed to organize meaningful collaboration between students from different parts of the globe.
The existing methods to struggle with cybercrime in organizations
In such a way, the current body of evidence devote to the topic accepts the fact that the sphere of education demands a specific and unique approach to integrating a robust security system and culture as it should be capable of considering the unusual needs of the environment. However, at the moment, there is a deficit of such approaches related to the gap in knowledge and the underresearched nature of the sector (Mello, 2018). For this reason, the authors (Matsumoto, 2019; Mello, 2018) agreed in the opinion that some successful experiences from other sectors could be analyzed in an attempt to find desired solutions. Thus, today there are several methods to struggle with cybercrime in organizations that demonstrate the desired effectiveness. First of all, the IT staff responsible for creating potent protection systems is focused on data collection about the most common types of breaches and their root causes. It helps to minimize risks and introduce an effective protection method.
At the same time, Lord and Levi (2017) stated that the organizations constantly tried to find new ways of protecting their data and guaranteeing that malefactors will not be able to steal it. One of the existing approaches presupposes the multi-layered security system with the strict demands to identification and provision of limited access regarding the level of authority and needs of a certain worker (Lord and Levi, 2017). It helps to minimize the harm done to the organization if something is wrong and, at the same time, provides specialists with an opportunity to trace a cybercriminal or investigate the vulnerability he/she used. Moreover, effective reporting practices and data collection tools acquire the top priority as the way to remain informed about new threats and resist them.
Finally, the organizations give much attention to creating guidelines for their workers as a part of security systems to inform them about the most topical threats and how to avoid them. (Wilner, 2018) admits the fact that the IT staff, along with other employees, become active players when struggling with cybercrime because of effective recommendations and security models. These include the need for a full-service Internet security site, strong and updating passwords, regular updates, protection of home network, and controlling media settings (Wilner, 2018). Mello (2018) stated that the observation of these simple guidelines guaranteed a significant reduction in the number of breaches and attacks. For this reason, a similar experience can be used by educational establishments, but with the change demanded to consider their unique working environment.
The approaches to creating a safe environment
Because of the growing importance of cybercrime and its rates, the question of a safe environment also becomes topical. Diffee and Datta (2018) offered their own definition of a safe environment in terms of cybersecurity, stating that a network with the minimum number of vulnerabilities, the existence of a robust security system, and the improved work of employees provided with guidelines on how to act in terms of the increased danger coming from cybercriminals. In perfect conditions, the safe environment is also characterized by the fast and effective responses to different types of threats, data collection, and its provision to the IT department to create an effective method to struggle with them. However, in real-life conditions, establishing a safe environment is impossible because of the constantly changing nature of cybercrime and the emergence of new factors affecting systems (DLA Piper, 2019). Under these conditions, the potent approaches to creating a safe environment presuppose the minimization of vulnerabilities and better management.
Revolving around the problem, Kremling and Parker (2017) stated that one of the effective methods to create the desired surrounding was to engage all stakeholders in the process by demonstrating the importance of their contribution and risks that might emerge because of their lack of knowledge or competence. For this reason, the creation of guidelines on cybersecurity can be viewed as part of the security system’s establishment and its effective work. Moreover, Kremilng and Parker (2017) emphasized that no system could ensure complete protection for all threats because of their extremely diverse character and the constant appearance of new technologies used by malefactors to cause damage. For this reason, the only way to support the high safety of the environment is to constantly monitor its state, which is possible only with the involvement of all users who have access to valuable data.
Under these conditions, the problem of creating a safe environment becomes topical today. The existing literature outlines that no system can guarantee complete protection; however, it is still vital to continue collecting data about the problem and methods employed by cybercriminals to damage various institutions. It is a way to remain capable of future upgrades and protecting critically important knowledge and information from theft.
Organizational learning
Most reviewed sources state that working with personnel is one of the central interventions that might help to manage cybercrime in educational establishments. Under these conditions, the concept of organizational learning (OL) acquires the top priority. It can be defined as the process of gradual improvement within an organization through gaining experience and using it to generate practical and relevant knowledge (Smerek, 2017). This new information is translated into practice with the primary goal to enhance the vital aspects of the unit’s functioning and ensure there are conditions for new positive change (Smerek, 2017). In such a way, there are three major processes occurring in organizational learning, such as knowledge creation, knowledge retention, and knowledge transfer (Smerek, 2017). The successful change and implementation of new practices should also presuppose the increased attention to these aspects. Organizational learning also focuses on establishing specific culture favorable for engaging in training and sharing activities (Smerek, 2017). Finally, it offers strategies that can be employed to improve outcomes and teach employees how to respond to emerging problems and manage them effectively. Under these conditions, the application of OL to the problem of cyberattacks in educational organizations might help to attain better outcomes.
Organizational learning theory recognizes the importance of using knowledge to promote positive change. However, it is vital to ensure that this information will be available and understandable for all stakeholders; otherwise, the proposed alteration will fail due to the lack of understanding or unwillingness to accept new practices. That is why the application of organizational learning models can help to attain the enhanced adaptability throughout the organization, promote employee satisfaction, and increase effectiveness (Smerek, 2017). OL offers some methods to improve skills and create new knowledge, including learning from past experiences, learning from others, knowledge transfer, and research approach (Basten and Haamann, 2018). Regarding the research problem, the given methods can be sufficient to explain the major ideas of cybersecurity to staff members and familiarize them with past experiences to improve their responses to new threats (Smerek, 2017). At the same time, the research approach presupposes the data collection and processing to establish the basis for creating new practices meeting the demands of the current unit. Under these conditions, organizational learning is viewed as an important aspect of the paradigm supposed to resist cybercrime in educational establishments of the UAE.
Risk management
Improved risk management practices are another critical part of organizational learning theory. In general, it presupposes the continuous process of identifying, evaluating, and monitoring all possible threats to the work of an organization. They can arise from multiple sources regarding the sphere where a unit functions and its major tasks (Hopkin, 2018). Under these conditions, risk management becomes a complex and vital process critical for the stable functioning of organizations (Hopkin, 2018). For the educational sector of the UAE, risk management should also be viewed as one of the prior tasks because of the growing number of cyberattacks and serious damage caused by them. Thus, applying the organizational learning models, risk management can be improved by providing better knowledge about existing threats to teachers and additional courses to explain the major components of these risks (Hopkin, 2018). Employment of organizational learning strategies contributes to better results as they guarantee the decreased resistance to change and the enhanced understanding of new information (Hopkin, 2018). Under these conditions, cyber risk management in educational establishments of the UAE correlates with OL and its central approaches to creating a learning organization.
Cybersecurity and organizational learning
Discussing the problem of cybersecurity in the educational establishments of the UAE, it is possible to admit the critical importance of using organizational learning as the framework for achieving the desired goals. The existing literature demonstrates that the application of OL strategies to companies experiencing problems with managing new risks can promote improved outcomes. First, it helps to eliminate the gap in knowledge and make responses stronger (Basten and Haamann, 2018). Second, it creates the environment needed for better specialists’ work (Basten and Haamann, 2018). Under these conditions, using OL in terms of cybersecurity can help to reduce the number of successful attacks because of the better vision among employees on how to resist them and what measures can be applied to avoid being damaged (Smerek, 2017). Most authors also assume that the lack of attention to organizational learning might precondition the inability to address the new issues effectively and failure of incentives to establish a new paradigm to struggle with cybercrime and resist it (Basten and Haamann, 2018). For this reason, cybersecurity and organizational learning can be viewed together as the effective management of all risks depends on learning strategies peculiar to the organization.
The concept of a learning organization can also be considered an important one regarding the discussed problem. It is defined as a unit with experience in creating, acquiring, and transferring knowledge and altering its activities and behaviors according to this new information (Smerek, 2017). It creates the basis for continuous organizational improvement and better performance levels. Moreover, a learning organization is characterized by better responsiveness and the ability to manage rising threats faster (Smerek, 2017). For this reason, speaking about cyberthreat and cyber risks mitigation, shift to this model becomes a potent method to attain better results and succeed from the implementation of innovative knowledge and its transfer into practice (Smerek, 2017). For teachers, operating within the learning organization means a better chance of being involved in training activities improving their skills, and the ability to manage risks (Smerek, 2017). In such a way, the concept of learning organization becomes critically important for an enhanced understanding of what measures can be applied to units in the UAE to attain better results and promote positive change.
Cybersecurity culture and cybersecurity risk mitigation
As stated previously, the growing cybersecurity threat means the need for creating a specific environment favorable for better responses. Under these conditions, the establishment of a cybersecurity culture becomes one of the major concerns of organizations trying to resist these risks. The term can be defined as the set of values, attitudes, and patterns of the behavior determining commitment to information security (Corradini, 2020). The definition shows that culture is more important than awareness, as it means that people do not think about their actions and possible outcomes; instead, they act following their values and beliefs (Corradini, 2020). Formation of cybersecurity culture presupposes training, focus on increased awareness and communication, and implementation (Corradini, 2020). However, because the concept is closely related to the functioning of multiple specialists and their ability to consider new information, the application of organizational learning becomes a beneficial way to attain desired outcomes. In other words, the desired cybersecurity culture can be created by using organizational learning methods, such as training, courses, seminars, and additional explanations needed to promote higher responsibility and performance levels.
In such a way, OL and the creation of a cybersecurity culture can be effective ways in resisting exiting risks and their monitoring. It means that cybersecurity risk mitigation, or the process of considering new threats associated with the use of devices and provision of methods to evaluate them, becomes linked to the ability to establish an appropriate learning environment and provide teachers with an opportunity to acquire knowledge vital for struggling with cybercrime (Corradini, 2020). Moreover, effective management of this aspect depends on the correct evaluation of units’ capabilities and teachers’ awareness. Under these conditions, it is vital to create a cybersecurity culture characterized by OL strategies and increased attention to risk mitigation. Personnel training and increasing staff preparedness can be viewed as possible ways to achieve this goal.
Personnel training
The majority of authors who delve into the problem admit the necessity to work with the staff to improve their capabilities in resisting cybercrime. Holt (2018) accepted that there was a gap in knowledge among employees on how to resist attacks and work safely when using computers. In this regard, he views training as a way to improve staff’s comprehending of the existing risks and hazards linked to the digital environment (Holt, 2018). Moreover, personnel training about cybercrime and cybersecurity should acquire the top priority as an effective tool to reduce rates and costs of attacks (Holt, 2018). The analysis shows that in numerous cases, employees had a chance to avoid being attacked or created a favorable environment for the intrusion because of their poor computer literacy or knowledge of how attackers use vulnerabilities and dangerous software (Holt, 2018). Nevertheless, it is vital to select appropriate forms to match the existing learning capability of workers (Jerez-Gomez, Cespedes-Lorente and Valle-Cabrera, 2005). For this reason, personnel training can be a practical solution to a growing threat.
The significance of training drives the positive change in regulatory measures and policies created by organizations to resist the growing wave of attacks. Thus, Kremling and Parker (2017) admitted that the changes in policies were mainly focused on the inclusion of specific computer training necessary to improve the workers’ understanding of how hackers can affect their functioning and what measures should be used to guarantee the best positive outcomes. At the same time, there is a challenge associated with the introduction and implementation of robust protective measures because of the difference between industries and the need to diversify policies and approaches to attain desired results (Kremling and Parker, 2017). In other words, the education sphere, because of its complexity and the unique open environment, requires a unique approach to personnel training that will consider these features and provide teachers with effective methods of data protection. At the moment, there is a gap in literature linked to this aspect.
In such a way, the authors view personnel training as the key to creating a safe environment. Because the majority of attacks occur because of the incorrect use of software, the provision of staff with basic knowledge and skills of cybersecurity will help to reduce the cost and harm associated with cybercrime. However, it can be a sophisticated task because of the need to consider the central peculiarities of each sector. For the educational sphere of the UAE, this challenge is topical because of the high speed of its evolution and the lack of knowledge of how to manage the growing number of threats preconditioned by digitalization and the dominance of online forms of learning (Zhuang et al., 2015). Under these conditions, guidelines and personnel training should be given top priority to create the basis for the future rise.
Correlation between staff preparedness and cybercrime rates
The importance of personnel training is evidenced by the existing literature and statistics it offers. For instance, Holt (2018) outlined the correlation between awareness among staff and cybercrime rates in certain organizations. He admits that the better workers understand how technologies should be used and what loopholes can be explored by attackers, the lower chance of intrusion is observed in a unit (Holt, 2018). Moreover, in companies with policies focusing on cybercrime, workers cooperate with the IT staff and provide data and information needed for them to create a safe environment (Holt, 2018). In accordance with the recent research, the personnel training in the given sphere can help to attain a minimum of 40% reduction of attacks per year because of their ability to select the safest options and avoid phishing or other insecure links. In such a way, there is a proven relationship between the provision of appropriate knowledge to personnel and their ability to function effectively in terms of the growing cyber threat.
For the education sphere, the statistics are similar. For instance, in educational establishments of the UAE with the focus on the development of computer literacy among both educators and students, the number of cyberattacks is lower if to compare with the establishments with no attention to the given factor (Imranuddin, 2017). At the same time, the existence of basic recommendations also helps to increase the organization’s capability of resisting maleficent actions and decrease the cost of harm caused by them.
International comparison of protective measures
Comparison of identified cyber risks practices
The enhanced vision of exiting approaches to creating a safe environment and minimizing the threat coming from cyberattacks can be acquired by investigating international practices and comparing them with the current cyber risk practices in the UAE. The USA and its strategies are chosen for the comparison because of the availability of information about its current methods. Moreover, the state suffers from numerous cyberattacks every year, meaning that it devotes much attention to the given aspect and has policy regulations for the most important spheres and institutions to protect data and guarantee their stable functioning. Finally, the USA is one of the leaders in the IT-sphere, with multiple companies creating software and security systems aimed at protecting organizations and improving their functioning (Powell et al., 2020). For this reason, much attention is given to the US approach and its comparison with the identified cyber-risk practices.
In the USA, there are various legislative proposals to establish guidelines for organizations to improve their cybersecurity and data protection capabilities. Thus, the Cybersecurity Act of 2015 offered numerous provisions to improve the sharing of data related to cybercrime, threat, and breaches among companies to help them (Powell et al., 2020). The act also emphasizes the need to monitor information systems, operate defensive measures, share cyberthreat indicators or effective strategies, and form a unified approach to resolving the problem. Concerning the education sphere, the USA accepts that institutions of higher education have sensitive data about students, staff, faculty, and alumni (Powell et al., 2020). However, there is a lack of a centralized structure to protect them, meaning that improved data sharing and coordination should be aligned (Deloitte, 2018). In general, the UAE fosters a similar approach, but at the moment, it lacks guidelines and knowledge of how to align the unified method and create safe cyberspace to improve the cooperation between various institutions in the state (Deloitte, 2018). For this reason, some of the US practices can also be implemented into the work of local institutions.
Theoretical underpinning of the study
Cyberattack theory
The ability to resist cyberattacks and remain protected is linked to the existing understanding of the nature of cybercrime, its causes, and how attackers act to harm units. For this reason, there is a significant number of research studies focused on the development of cyberattack theory and its adaptation to existing needs. Zhuang et al. (2015) also focused on analyzing the major issues associated with this type of threat and assumed that any cyberattack success relied on information acquired by a hacker when the given attack is launched. For this reason, valuable information should be a fundamental element of any framework or theory of cyberattacks to create measures to protect it. Thus, the configuration information includes the knowledge about the configuration of a computer system, and a target device becomes part of the information interest of any attack (Zhuang et al., 2015). In such a way, any system has a specific information parameter meaning that any target device is presented by a set of information parameters (Zhuang et al., 2015). A hacker tries to acquire or modify any of these parameters to cause harm or generate benefit from his/her actions.
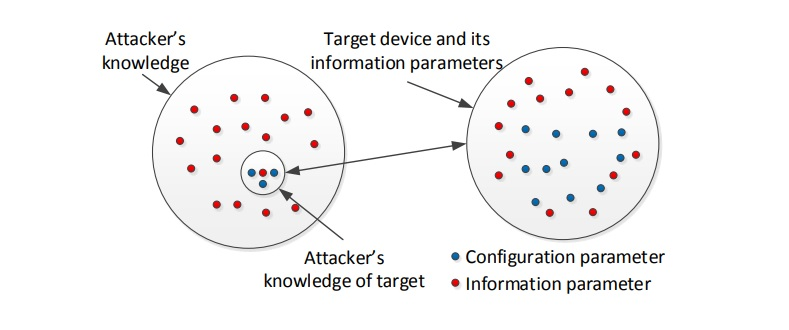
From the figure, one can see that the attacker’s knowledge of the target and his/her basic knowledge are interlinked and are needed for the successful action. It comprises the basis of cyberattack theory, which defines attacks regarding the existing information parameters and attempts to acquire them (Zhuang et al., 2015).
The given theory also defines an information parameter that becomes the target of any harmful actions. Zhuang et al., (2015) defined it as a unit of knowledge that had a specific value because of its impact on the configuration parameters or its importance for the functioning of the whole system. Any system is comprised of such parameters, which make it attractive for hackers and influence the choice of strategies. The target can also be defined as a device, or computer networks or communication channels, cellphones, routers, and other machines that can be interesting for an attacker who tries to obtain information or alter them (Zhuang et al., 2015). Consequently, a target system has a system information parameter and consists of a set of targets that are viewed by attackers as their primary goal (Zhuang et al., 2015). Finally, Zhuang et al. (2015) describe the term attacker as a single or team of intruders, where an actor can be represented by a human being or a specific program or software. The given terms create the basis of a cyberattack theory stating that the attacker influences the target system and device attempting to acquire or change information parameters (Zhuang et al., 2015).
The given cyberattack theory becomes vital for the analysis of the problem and search methods to resist cybercrime. Thus, regarding the type of attack, there is a need for specific measures that can help to minimize its negative impact on the organization and ensure that the information parameters will remain safe. For the educational sector, the given central concepts also remain applicable because of their universal character and relevance. However, the ways to resist these maleficent actions differ because of the diversity of target systems and devices that should be protected. It means that for the research study, it is vital to apply the theory considering the peculiarities of the UAE educational sector and search for the methods to reduce the vulnerability of target devices (Cyber safety and digital security, N.D.). To carry out any attack, a malefactor should possess the information about a planner or a service that offers authorized access to various databases and actions (Zhuang et al., 2015). For this reason, the protection of such units acquires the top priority.
Framework
The cyberattack theory offered previously is viewed as a significant part of the cybersecurity framework discussed today as the critically important concern for the modern digitalized world. Thus, it is taken as a fundamental element for sustaining a technologically sound model and guaranteeing the further evolution of multiple spheres of human activity (ABI Research, N.D.). ABI Research team (N.D.) outlines the fact that disruption of electricity or complete destruction of financial systems because of the rude interference in the functioning of a network is a reality today and poses a threat to national security. The hackers become more organized and function in political, criminal, terrorist, financial, and educational sectors, which means that their impact becomes more serious. For this reason, much attention is devoted to the creation and support of the cybersecurity framework as a part of national and industrial development strategies (ABI Research, N.D.).
The existing framework is characterized by the theoretical base defining malefactors and devices that are attacked, and the close cooperation between stakeholders as cybersecurity is viewed as a complex aspect demanding the collaborative effort to resist it (Kremling and Parker, 2017). The paradigm also presupposes incorporating various disciplines such as legal, technical, educational ones to create effective protection measures (ABI Research, N.D.).
At the same time, there are several obstacles to further evolution of the framework and its improvement. First of all, the lack of information sharing and knowledge gaps prevent governments and managers from developing sound and practical methods of detecting and eliminating vulnerabilities in existing systems (Kremling and Parker, 2017). Moreover, there is a lack of understanding of how cybercrime works in various sectors. For this reason, the solution lies in implementing cybersecurity mechanisms in all layers of society and cooperation between all actors to improve the world’s cybersecurity capability (Lassoued and Fawcett, 2020). One of the existing frameworks presupposes the focus on five major work areas, such as legal measures, technical measures, organizational measures, capacity building, and cooperation (ABI Research, N.D.). It means that by focusing on these elements of cybersecurity, organizations and governments acquire the chance of resolving the problems and creating a robust paradigm for addressing and struggling with cybercrime.
The current framework also presupposes the formulation of specific standards that can be used and altered by various spheres with the primary goal to adapt their functioning to new threats and remain capable of protecting data. The standards offered by organizations, such as Cloud Security Knowledge Alliance, offer their set of measures that can be applied to various situations and used to protect the main participants from maleficent actions (ABI Research, N.D.). The adherence to these standards can be useful in acquiring the needed experience and transforming it into the guidelines vital for the effective work of a unit in complex conditions of constantly changing cyber threats.
Nevertheless, it is vital to mention that the existing framework also has some gaps and limits because of its inability to consider all problems emerging today. Thus, Neyadi et al. (2015) stated that for every sector, the framework should be altered and adapted because of the unique nature of challenges it faces and the requirement for specific methods and knowledge to resist them. In such a way, the existence of the given framework can be viewed as the basis for future improvement as it can be used as the fundament for the creation of effective and sufficient security systems adapted for every sector and possessing their unique methods of prevention and monitoring (Imranuddin, 2017). At the same time, the framework is vital for the further discussion and improvement of organizations’ capabilities of resisting cybercrime.
Applicability of the theory and framework to the research study
The cyberattack theory and the framework for establishing cybersecurity outlined by the analyzed literature are vital for the research study as they create the theoretical and practical basis for integrating the guidelines and models of preventing cybercrime. At the same time, they can be viewed as general ones because of their focus on organizational excellence in general, with no details to peculiarities of a particular sphere. It means that the gap in knowledge mentioned previously is observed. Although there is a significant body of evidenced determining cybercrime, attacks, target devices, and information of interest, still little attention is given to the functioning of the educational sphere and the ways to protect it in terms of the shift towards online learning, online payment, and the culture of openness peculiar to the field (El-Guindy, 2014; Nikolaeva and Nathan-Roberts, 2016; Stone, 2017). For this reason, the basic assumptions of these models can be taken as the basis for the development of new recommendations and guidelines.
In the educational sphere of the UAE, the problem of cybersecurity and cybercrime remains topical as they precondition serious financial loss. For this reason, the application of cyberattack theory with changes to adapt it to this environment can help to attain multiple benefits. Considering the fact that students and educators’ laptops and computers can be viewed as target devices, and the information on them becomes the information parameter attractive for attackers, the primary goals of the cybersecurity system is to improve the protection of these elements by offering either specific software or recommendations to minimize risks (Kremling and Parker, 2017). Additionally, the problem of authorized access by using a planner also becomes topical as the lack of knowledge about how to protect passwords often precondition the appearance of vulnerabilities (Zhuang et al., 2015). For this reason, the employment of the cyberattack theory acquired from the literature review is favorable for the research study as it helps to offer effective solutions to the problem.
Moreover, the framework for cybersecurity outlined by the majority of authors is also relevant for the research study. Kremling and Parker (2017) stated that only the cooperation between the major stakeholders could be viewed as the way to attain success and guarantee that cybercriminals will have lower chances of causing harm to various organizations. For the educational sphere of the UAE, the cooperation between institutions, government, IT developers, and staff can also be viewed as the part of a new and improved paradigm critical for struggling with cybercrime and guaranteeing safety to students, educators, and their personal data (Martin, Naqvi and Schoenbach, 2019). The exchange of experiences and sharing information about recent attacks can become the central way of increasing awareness and preparing teachers for working in new conditions characterized by constantly changing risks and their scope.
In such a way, the analyzed literature offers a theory and framework vital for the research study. However, they lack the details because of the universal character, which means that for the UAE educational sector, these should be altered and adapted to a new environment. It also means that regardless of the focus on the creation of effective methods of data protection, there is still a serious under researched area devoted to how various systems can be adapted to organizations with a unique working environment. For this reason, the offered study with the focus on the influence of cybercrime on educational institutions of the UAE will benefit from the application of the ideas of a target device and information parameters as they can help to form the research framework and the theoretical paradigm for the study.
Chapter summary
Comparison of studies identified from the reviewed literature and key research problems identified
Altogether, the proposed literature review proves the assumptions of the research study. The existing body of evidence recognizes the critical importance of cybercrime and views it as a major threat to the stability of organizations in the future. The majority of authors emphasize the substantial harm done by the given form of maleficent actions and the high costs of attacks if they succeed. Moreover, the research works admit the necessity to introduce effective protection measures capable of monitoring the vulnerabilities, collecting data, and sharing it to create robust systems that can protect critically important data from attacks. Because of the tendency towards a further increase in the number of threats, the given task acquires the top priority as one of the musts of contemporary society. The high scope of the problem and its topicality justify the choice of the topic for the research and its relevance.
Moreover, the literature offers the theory and framework that can become the basis of the research study and help it to evolve. The definitions of cybercrime, attacks, targets, and security systems are fundamental for the research, and their improved knowledge acquired from the literature is necessary for achieving the goals mentioned above and answering the major research questions. The authors insist on the need for collaboration between the major stakeholders and data exchange as the determinant of success and the ability to remain informed about the change in the digital environment and new ways to attack systems or databases. Due to the dominance of online forms of cooperation, cybercrime acquires additional topicality because of its penetration in all spheres of human activity and transformation into a threat to the national security of all states.
At the same time, the review empowers our perspective on the problem as it proves a particular gap in knowledge related to the problem under investigation. Although there are multiple recommendations on how to act and behave to reduce the risk of being attacked, little attention is given to the educational sphere and methods of student and teacher data protection, which might transform into a serious concern in the future because of the shift of priorities towards the use of online forms of learning and payment (Nuzhat, 2020). That is why our assumptions become justified by the existing body of evidence. The culture of openness peculiar to the modern education sphere also creates the basis for the emergence of new loopholes that should be considered as malefactors can use them for their purposes. For the UAE educational sphere, the lack of guidelines and models also becomes evident, which means that the evolution of the sector is not supported with the growth in teachers’ awareness and their capabilities linked to resisting cybercrime and protecting their data.
In conclusion, the given section creates the basis for the whole research study as it offers the theoretical framework for the discussion and proves the topicality of the selected problem. Considering the hypothesis and research questions formulated above, the need for further discussion becomes apparent as there is a need to fill the discovered gaps in knowledge by offering robust and sufficient guidelines on how to minimize the level of threat peculiar to the UAE educational sphere and provide teachers with tools to increase their effectiveness in terms of the shift of priorities towards digitalization and functioning in the online environment.
Proposed Conceptual Framework
Introduction
The following section offers the conceptual framework for the research study and factors impacting its formulation. The central idea of the given study is that cybercrime becomes a growing problem for the modern world, and there is an urgent need for actions that might help to resolve it. For the UAE education sector, the theme also remains topical, for this reason, the proposed conceptual framework focuses on the analysis of the issue regarding its institutions and how they can become capable of resisting cybercrime and new attacks. The literature review offered above demonstrates that the possible interventions for the improvement of the situation presuppose the attention to organizational learning as the way to enhance teachers’ ability to resist cybercrime and provide them with innovative strategies needed to create a safe environment. Moreover, there is a demand for practical protection tools and methods. That is why the conceptual framework section focuses on how to address these issues and create the paradigm considering the existing knowledge linked to the problem of concern. For this reason, the conceptual framework is established with the idea to that organizational learning capability, security culture, and perceived cybercrime risk influence cybercrime mitigation and should be viewed as the key to establishing a safer environment. It is also aligned with the research problem to guarantee the credibility of findings, their relevance and to answer the research questions formulated above.
This part of the work offers the argument structure and explains how it is linked to the existing theory. For this reason, there is a definition of the research problem, a focus on the theoretical coherence, alignment of research strategy with the conceptual framework, and the explanation of objectives and hypothesis formulation. It means that the section justifies the choice of the research paradigm and improves the understanding of the argument and its structure. At the same time, it demonstrates the path selected to analyze the problem and acquire credible results that can be used to discuss the question and formulate a conclusion.
The section also suggests the visualization of the conceptual framework made for the enhanced understanding of the central assumptions and relations between variables. The scheme considers the main operational variables created regarding the literature review and the research problem. It also represents the presupposed relations between the hypotheses and can be used to acquire a better vision of the thesis’ main focus. Moreover, using the given scheme, it is possible to trace the main idea of the research and conclude about possible outcomes.
Finally, the section ends with the concluding section summarizing all major assumptions made regarding the conceptual framework and creating the basis for introducing the methodology part. In such a way, this part of the work can be viewed as the transition from theory to empirical testing and a bridge linking the theoretical concepts with real-life conditions, which is needed to select the effective methods and create the empirical research paradigm.
Defining the research problem
As stated previously, cybercrime is a global concern affecting various spheres of human activity and preconditioning serious harm. The topicality of the problem grows every year because of the high speed of society’s digitalization and shift to online forms of cooperation between individuals. Under these conditions, creating robust protection measures and the formulation of guidelines on how to resist attackers acquire the top priority. Investigators view it as a key to success and further improvement (Zhuang et al., 2015). Regarding the given research study, the efficiency of such methods and their introduction regarding the peculiarities of an establishment becomes the main research problem. However, because of the scope of the given question, the issue is narrowed to attain success in analyzing and discussing the vital aspects.
Cybercrime is also topical in the UAE because of the above-mentioned emphasis on cultivating a digital environment and creating a knowledge-based economy. It means that the nation’s educational establishments enter the phase of their extensive development. However, the existing guidelines on how to manage cybercrime might be insufficient because of the constant emergence of new threats (Diffee and Datta, 2018). Furthermore, various settings might demand specific interventions and methods to protect data, meaning that there is a need for new, constantly updating guidelines (Diffee and Datta, 2018). Moreover, there is limited knowledge about the nature and scope of this issue in terms of the UAE educational sector, meaning that teachers remain helpless and ineffective in managing this aspect. The lack of training and poor awareness serve as the leading causes for successful cyberattacks (Aliyu et al., 2020). However, the problem is also more prevalent across a wider context. For instance, Aliyu et al. (2020) say that all organizations today are vulnerable to cyberattacks and their protection becomes a central issue. Although there is a plenty of methods discussed by other authors, there is still a need for new, improved and more complex solutions integrating several regulations to make units capable of resisting attacks. Liu, Huang and Lucas (2020) also outline the necessity to develop IT infrastructure as the response to new threats as it guarantees fewer breaches and better ability to struggle with attackers. In such a way, the scope of the problem is significant and it has a wider context. Narrowing the focus, it is possible to state that the research problem of the study is the lack of cybersecurity guidelines and the gap in knowledge in the UAE education sector.
Furthermore, the work of any organization depends on multiple factors that affect its members. It means that the introduction of robust cybersecurity measures might not be enough if teachers do not possess the correct understanding of how it can be employed and what strategies might help to become more protected. It means that the research problem is also linked to the concept of organizational learning as one of the major tools helping to introduce change to the work of units and show new ways of interactions (Zhuang et al., 2015). Analyzing the problem of cybercrime in the UAE educational establishments through the prism of organizational learning, it is possible to select among the proven and effective practices that might help teachers to acquire additional freedom in selecting approaches offered by the IT department and cooperate with it to resist cybercrime and improve their awareness levels.
Moreover, the literature review shows the gap in knowledge about how teachers in the UAE can increase their awareness, cooperate with the IT staff and become better prepared for new challenges. For this reason, filling this gap can be viewed as a part of the research problem as it is critical to outline the framework characterized by the increased security and data protection, and available to educators. Organizational learning combined with practical strategies might help to achieve the goal (Wilner, 2018). Under these conditions, the research problem also includes the necessity to evaluate the applicability of organizational learning’s assumptions to the question of cybersecurity in the UAE educational establishments and select among the most effective ones. It will contribute to the improved understanding of how the gap can be addressed and how the main stakeholders can benefit from using different interventions or practices.
The existence of this deficit of information means that there is a need for the evaluation of facilitators and inhibitors of cybersecurity in educational institutions to help to establish guidelines that will be later used by IT staff and explained to educators. Filling the gap in knowledge will also help to introduce practical cybersecurity guidelines vital for the further improvement of institutions and their functioning. For this reason, the research problem of the study presupposes the in-depth analysis of aspects affecting the work of educational establishments of the UAE regarding cybersecurity and the ways to improve teachers’ capability of resisting cybercrime by using and reconsidering the organizational learning and security culture.
At the same time, organizational security culture and perceived cybercrime risk are two other factors affecting cybercrime mitigation. According to the existing body of literature, these elements play a central role in educators’ ability to resist new risks and acquire new skills (Diffee and Datta, 2018). Following this idea, security culture and cybercrime risk are viewed as two central variables fundamental for the research problem as they should be discussed and analyzed regarding the necessity to attain better outcomes and guarantee that specialists are capable of acquiring skills and competencies vital for their evolution and improved ability to protect data vital for the work of the higher educational establishment.
Altogether, the research problem focuses on several major aspects. First, there is a need for a comprehensive investigation of cybersecurity in the UAE. Second, the existing cybersecurity methods should be analyzed regarding organizational learning and the possibility of their integration into the work of an educational establishment. Third, the analysis of cybercrime mitigation in different settings regarding existing security cultures should be performed. The evaluation of the offered guidelines and their applicability to the situation should also be viewed as a part of the research problem as they affect the outcomes and remain in the focus of the study. In such a way, the formulated research problem is practical, relevant, and its consideration in terms of the research study can provide practical outcomes needed to improve the work of the sphere.
Theoretical coherence
The research problem of the study impacts the choice of theories relevant to the research and their integration into the research study. Thus, organizational learning theory is relevant for the research and needed to create the conceptual paradigm for its investigation. It emphasizes the importance of developing a specific learning culture in a certain organization to increase its ability to resist numerous threats and ensure that all members can use new approaches (Smerek, 2017). Following the given theory, organizations should cultivate a new culture encouraging knowledge sharing, provide opportunities for acquiring new skills, and offer conditions for innovation (Smerek, 2017). By providing teachers with instructions and guidelines on how to manage new risks and remain capable of resisting them, it is possible to resolve the problem of the lack of tools vital for protecting all participants from cybercrime.
Moreover, organizational learning theory can be correlated with cyberattack theory offered by most researchers. Thus, protection of information parameters becomes the leading priority for teachers and other specialists working in the same environment (Wilner, 2018). It means that the organizational learning activities and strategies should be focused on the question of how to create a new working culture characterized by realizing the importance of cybersecurity concerns (Smerek, 2017). Aligning these two paradigms, it is also possible to justify the choice of interventions and guidelines as robust and working tools vital for guaranteeing desired outcomes and reorganizing the work of the UAE educational establishments to make them resilient and capable of protecting data. Combining the organizational learning and cyberattack theories, it is possible to formulate the background of the study and justify the choice of tools that are viewed as necessary in terms of the existing tasks.
In such a way, the theoretical coherence of the study comes from the similarity of assumptions offered by various researchers. The majority of existing theories acknowledge the significance of data protection and the elimination of loopholes in protective systems by training and improving the skills of actors who operate within the same network (Smerek, 2017; Yar and Steinmetz, 2019). The organizational learning theory is taken as the basis for the planned improvement. It assumes that positive change can be attained by altering the climate and working conditions (Yar and Steinmetz, 2019). This task can be performed by using various interventions, including training and the creation of sufficient guidelines. Under these conditions, the authors state that organizational learning has similar assumptions on how the work of organizations can be improved, which increases the theoretical coherence of the study and justifies the choice of methods (Smerek, 2017). The concept is defined as the process of creating, sharing, and transferring knowledge within an organization to improve its work and guarantee all employees possess an improved vision of how behave in different situations (Garvin, Edmondson and Gino, 2008). It means that a learning organization is characterized by specific ideology, methods, and evaluation models helping to assess the current level of skills peculiar to specialists and offer additional training (Coopey, 1995). At the same time, the concept includes system thinking, team learning, personal mastery, mental models, and shared vision as the part of the organization focused on increasing its workers’ awareness ((Garvin, Edmondson and Gino, 2008). For instance, organizations with the focus on creating multiple opportunities for learning are characterized by the strong shared vision with the focus on training as the way attain better outcomes and avoid failures ((Garvin, Edmondson and Gino, 2008). It means that organizational learning is no limited only by educational efforts of the top management; however, it demands personal and team engagement in the development process to minimize the number of errors ((Garvin, Edmondson and Gino, 2008), Regarding the problem of cybersecurity, organizational learning might presuppose formation of a shared vision cultivating the idea of better awareness and ability to face new threats and deal with them.
In such a way, researchers state that training and learning supported by the central ideas of organizational learning can help organizations to improve their ability to resist cybercrime (Smerek, 2017; Wilner, 2018). The personal mastery of employees cultivated by specific training and education can contribute to the formation of a shared vision and collaborative effort to resist new threats and remain prepared for growing challenges in the sphere of cybersecurity (Wilner, 2018). The focus on this aspect can help to attain improved outcomes and minimize the negative impact of cybercrime on various education establishments. Additionally, higher cyber mitigation rates can be achieved due to establishing appropriate guidelines, training, and a practical resistance model.
Alignment of research strategy with the conceptual framework
Considering the theories mentioned above and the major assumptions offered by other authors, it is possible to align the research strategy with the conceptual framework of the study. The paradigm presupposes that the organizational learning capability directly impacts the perceived cybercrime risk, trigger intuitive responses, and influence cybercrime mitigation rates. Most teachers might have biased attitudes and subjective perceptions of cybercrime risk, meaning that it is vital to acquire relevant data of their current visions and ideas (Julisch, 2013). Organizational learning capability also includes sharing information between specialists and organization of the united effort to be capable of resisting cybercrimes and new attacks. Moreover, learning capability correlates with the existing cybersecurity culture, meaning that the emergence of the shared vision linked to a particular problem promotes the appropriate challenges in the existing cybersecurity and offers resources that can be used to alter the existing views. At the same time, this aspect also affects the functioning of the IT sector of the organization, its security culture, and ensure better outcomes. In such a way, it is possible to admit the existence of a particular system characterized by strong mutual relations. This conceptual framework impacts the choice of the research strategy vital for the improved data collection and its analysis.
Thus, Organizational learning capability is viewed as the dependent variable. Its operational definition views it as a dynamic organization-wide learning orientation based on competitive knowledge to keep enterprise competitive in the dynamic markets (Basten and Haamann, 2018). Regarding the given study, organizational learning capability is linked to educational establishments in the UAE and their readiness to adapt to recommended changes and use new practices that might help to improve teachers’ ability to resist cybercrime and protect students and their data. In terms of the research study, the given variable is critical as is demonstrates how the existing culture is related to cybercrime mitigation and what changes can be made to attain the desired outcome. Moreover, by measuring the organizational learning capability, it is possible to conclude about how it is linked to cyber security risk mitigation in the discussed setting and cyber security risk mitigation becomes the independent variable as it impacts the job performance and outcomes of any organization. Its operational definition states that it is the reduction in the number of successful cyberattacks and their effective prevention and monitoring (Basten and Haamann, 2018). The changes in this aspect should be noted to acquire the improved vision of the effectiveness of various interventions and their ability to promote positive dynamics by reducing rates and mitigating risks. At the same time, it is vital to evaluate cybersecurity mitigation strategy, which includes training, improving specialists’ awareness, and prevention via successful monitoring of the current situation. These factors are influenced by the organizational learning capability and cybersecurity culture, meaning that this analysis will help to conclude about the impact of other variables and how they are aligned to the issue under concern.
The research strategy also presupposes the formulation of moderating and mediating variables, which are organizational security culture and perceived cyber security risk correspondingly. The first one is viewed as the organizational beliefs and values wherein employees undertake responsibility and take the required steps to expand the security of an enterprise’s information systems and networks (Basten and Haamann, 2018). Organizational cybersecurity culture depends on organizational learning and demonstrates the existing practices, employees’ attitudes, and overall environment employed to mitigate cyber risks and struggle with attackers (Knapp et al., 2006). Additionally, it presupposes establishment of an appropriate environment vital for security-minded thinking and possessing all necessary elements of better decision-making regarding cybercrime. Thus, practicing sufficient security is an accepted way to doing business or functioning of various organizations, including the educational ones. Under these conditions, choosing organizational cybersecurity culture as a dependent variable, it is possible to better analysis of the current research problem and improved vision of how cybercrime mitigation can be aligned (Knapp et al., 2006). Additionally, it represents teachers’ awareness levels regarding cybercrime in general and problems that might deteriorate their work at the moment (Basten and Haamann, 2018). The operational definition of perceived cybercrime risks determines it as the employee’s perception of crimes committed via the Internet by cybercriminals. This variable is also vital for the research as it demonstrates teachers’ perceived risks and consequences they might precondition. It is also linked to the organizational culture and might have various effects on cybercrime mitigation.
The following table containing all variables and measurement scales is offered:
Table 3.1: Variables and measurement study scales
First of all, it is vital to investigate organizational learning capability as it affects other variables and outcomes. Moreover, it is linked to organizational learning and cyberattack theory, meaning that there are several conceptions supporting the importance of the given factor and its positive effect on cybercrime mitigation and reduction. At the same time, the existence of other variables and their interdependence introduce the need for effective methods of performance analysis to determine if there are positive shifts in job performance and cybercrime mitigation preconditioned by the increased attention to training staff, cultivating their awareness, and establishment of the cybersecurity system.
Altogether, the following conceptual conclusions can be offered. The study rests on the researchers’ assumption that cybercrime is the critical factor affecting the work of educational organizations and making them vulnerable to various threats (Smerek, 2017). At the same time, in accordance with the proposed theories, the elimination of this threat demands the improved knowledge of its roots, possible causes, and factors that can help to improve the existing situation. Under these conditions, combining the theory and reality, it is possible to create conceptual conclusions stating that the comprehensive and in-depth analysis of the problem demands cooperation with teachers to realize their vision of the issue and ability to resist it in terms of cyberattack theory. Adhering to this model, it is possible to ensure sufficient and effective data collection in terms of the proposed hypothesis and its processing to apply to real-life settings.
Coherence between theory and reality of the study
The importance of the given research study is explained by the practical applications that are associated with conclusions and recommendations. The coherence between the theory and reality of the study comes from several factors. First, as stated previously, the researchers emphasize the need to formulate appropriate guidelines that might help educators to resist new attacks and remain capable of performing their major functions in terms of the growing cyber threat (Zhuang et al., 2015). For this reason, the determination of the central aspects affecting teachers, such as facilitators and inhibitors of cybercrime, have real and practical importance as it will help to establish more effective security systems considering all existing features and trends.
Second, the organizational learning theory remains one of the most effective frameworks for introducing positive change and improving employees’ knowledge. It can be applied to different cases to address the nagging problem and explain how to resolve it. However, speaking about the need to manage cybercrime and create effective strategies to train teaches, organizational learning offers a limited number of concepts and recommendations (Basten and Haamann, 2018). For this reason, the theoretical background created by using this framework can be translated to practice by outlining the methods that can be used to improve the organizational learning capacity of educational establishments in the UAE and provide teaches with additional tools needed to resist cybercrime and remain capable of achieving the existing goals. It justifies the relevance and feasibility of the study and its ability to contribute to the generation of practical knowledge.
The link between the theory and reality is also justified by the fact that for the UAE, the perceived cybercrime risk is viewed as one of the central problems and risks threatening the further rise of its educational sector. At the same time, the establishment of the organizational safety culture is a practical and sufficient solution that is accepted by most researchers working in the area as one of the possible methods to increase organizations’ ability to struggle with attacks (Philip and Salimath, 2018). For this reason, the study is linked to really existing goals and theories focusing on the further improvement of various institutions in terms of the high speed of digitalization peculiar to the modern world.
Another factor providing the bridge between outlined theory and real-life conditions is the need to protect students from cyberattacks. Educational establishments of the UAE guarantee the safety and protection of data for all applicants and view it as a major concern. However, the activity of malefactors and the diversification of tools available to them means that students might suffer from illegal activities. For this reason, improving organizations’ ability to struggle with cybercrime becomes a prior goal to protect learners and guarantee they can benefit from a favorable and safe environment. Applying the major theoretical assumptions to real-life conditions, it is possible to create methods of data protection that can be recommended for other establishments to protect their learners and teaches. The practical importance of this task explains the choice of the topic and its relevance.
Finally, the coherence between the theory and reality of the study is explained by the major objectives and goals. The research study focuses on eliminating the gap in knowledge related to cybercrime in the educational establishments of the UAE, meaning that it is expected to acquire practical resolutions for the problem that can be applied to practice. The existing body of evidence also acknowledges the need for useful recommendations and guidelines on how to resist the growing number of cyberattacks and preserve the effectiveness of workers (Philip and Salimath, 2018). Under these conditions, the theory and study are interconnected and help to attain practical outcomes.
In such a way, coherence between the theory and reality of the study is explained by several factors. The lack of appropriate guidelines, the need to protect the educational sector of the UAE, and the demand for robust cybersecurity measures justify the need to work on the problem and acquire its better vision. Thus, regarding cyberattack and organizational learning theories, the improved knowledge of facilitators and inhibitors of crime and processes that might affect an organization’s capability of resisting it is critically important. It means that transition this knowledge into practice becomes vital. That is why the offered research study creates the bridge between theory and reality by discussing the problem of cybercrime, its real nature, and how it can be managed by using working interventions.
Objectives/hypotheses formulation
As stated in the Research Agenda, the study focuses on the following hypotheses:
- H1: Organizational learning capability promotes higher knowledge about potential threats.
- H2: Perceived cybercrime risk directly impacts cybercrime mitigation.
- H3: Organizational security culture moderates the relationships between organizational learning capability and perceived cybercrime risk.
- H4: Direct correlation between organizational learning capability and cybersecurity mitigation is influenced by perceived cybercrime risk.
Hypothesis 1 can be viewed as the major assumption made regarding the existing literature. Most research works emphasize that the ability to learn and acquire new skills is vital for struggling with cybercrime and attackers (Preis and Susskind, 2020). Moreover, the organizational learning theory also admits the critical importance of cultivating specific learning culture within a unit (Smerek, 2017). Researches emphasize that cybersecurity risk levels peculiar to various organizations depend on their workers’ awareness levels and the ability to acquire new information (Philip and Salimath, 2018). It means that units with a developed culture and focus on promoting persona and professional employees’ growth benefit from better results and reduced number of threats (Preis and Susskind, 2020). This statement is vital for formulating the hypothesis and cogitating about the methods to struggle with cybersecurity. Under these conditions, H1 becomes the main statement of the research study, presupposing consideration of all outlined variables and their processing to determine the nature of relations between these two aspects. It is expected that the hypothesis will be proven in the course of research.
Hypothesis 2 revolves around the concepts of perceived cybercrime risk and cybercrime mitigation. Individual’s subjective evaluation of their risk influences their work in the Internet and digital devices (Holt, 2018). Research shows that more confident users with increased awareness perceive less cybercrime risk and are more willing to use online services, or engage in different activities via the Internet (Holt, 2018). In such a way, cybercrime mitigation and perceived risk are interdependent and the change in one aspect might trigger the appropriate alteration in another one (Nuzhat, 2020). Following this idea, improved cybercrime mitigation can be achieved by affecting educators’ perception of various threats and how they can be managed using resources available to them.
Hypothesis 3 is introduced regarding the body of evidence stating that organizational security culture is vital for managing threats and protecting members from different hazards, including cyberattacks and the activity of malefactors aimed at causing harm or stealing information. Under these conditions, affecting organizational security culture and improving it, it is possible to improve the learning capability of a unit and cybercrime risks (Holt, 2018). At the same time, Diffee and Datta (2018) are sure that organizational security culture is one of the most important elements influencing teachers’ ability to remain informed about existing threats and be ready to resist them. The high levels result in educators’ better vision of their contribution and methods that can be used. From another perspective, establishments with a comprehensive security culture try to improve their employees’ skills and competencies, which results in better outcomes (Diffee and Datta, 2018). For the educational sector of the UAE, this idea helps to offer working guidelines and implement them. For this reason, the hypothesis becomes vital for considering the impact interventions might have on the work of institutions and what measures can be viewed as effective ones.
Hypothesis 4 is formulated regarding the fact that employee’s perception of existing risks is central for establishing an effective cybersecurity culture and mitigating risks peculiar to a particular establishment. Possessing the correct knowledge of how malefactors might act and the consequences of their actions, teachers might have better motivation to use available security measures and feel free to ask for assisance (Nuzhat, 2020). Moreover, educators’ visions of current risks and their subjective judgements can moderate the effectiveness of organizational learning and reduce the unit’s ability to provide appropriate training for all specialist. Under these conditions, the proposed hypothesis considers these statements and focuses on the correlation between mitigation of risks and learning capability regarding the current representations peculiar to all teachers.
Altogether, the four hypotheses formulated above rest on existing studies and the most important ideas linked to cybercrime regulation and management. The literature review shows that most researchers are sure that the strong cybersecurity culture and advanced learning capabilities of a certain organization serve as the barrier limiting criminals and their attempts to cause substantial damage to a particular organization. At the same time, the investigators are sure that employees’ perception of crimes is a critical element of existing protective frameworks that should be given attention and cultivated to ensure the organization’s ability to evolve and struggle with cybercriminals (Yar and Steinmetz, 2019). These statements serve as the basis for formulating the hypotheses and proving their relevance, feasibility, and applicability to the study. Because the leading aim of the research is to determine how specific guidelines can promote better cybercrime mitigation, following these hypotheses, it is possible to conduct the research and conclude about the current state of the educational establishments in the UAE and problems linked to cybercrime they face.
Furthermore, these hypotheses are formulated regarding the proposed variables and relations between them. The theoretical framework formed by the literature review also justifies the choice of the variables and their use to build hypotheses and the theoretical framework.
Considering the above, the following conceptual model can be proposed:
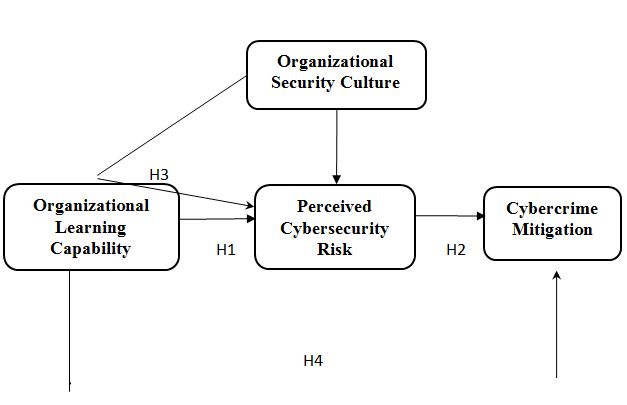
It represents the interdependence between various variables and how a change in one of them can affect others. The conceptual model also incorporates the theoretical assumptions peculiar to the field and demonstrates how they can be applied to the selected research problem to ensure its in-depth analysis. The hypotheses are supported by the research objectives:
- Ascertain the current state of perceived cybersecurity risk in educational institutions in the UAE and propose guidelines that can be adopted.
- Determine the correlation between the organizational learning capability and the effectiveness of cybersecurity risk mitigation in the educational sector of the UAE.
- Define how the existing organizational security culture can influence risks linked to employee negligence and improve cyber security.
- Outline employee related risks and how they can be reduced through learning and organizational culture.
The proposed conceptual framework comes from the existing literature, major assumptions linked to cybersecurity sphere, and can be used in future research papers to investigate the nature of relations between outlined phenomena and conclude about the most effective ways to struggle with the problem.
Chapter summary
Altogether, the proposed chapter states the research problem, which is the lack of cybersecurity guidelines and potent security models in education establishments of the UAE, meaning that there is the need for an in-depth analysis of all factors that can help to fill this gap. It also represents the conceptual framework for the research. It rests on cyberattack theory and theoretical assumptions of other researchers found in the relevant literature. Moreover, the major assumptions of organizational learning are also used to create the framework for the discussion. It views change in organizations as a complex process that should be supported by various tools and methods. Precisely, the positive alteration demands the cultivation of a climate characterized by the existence of features vital for achieving success. Applying this statement to the research problem, it is possible to admit that promotion of higher awareness levels among teachers and their training should be performed using organizational learning methods. Only under these conditions, positive outcomes can be generated. That is why the given theory becomes an important part of the conceptual framework and should be taken into account then translating theory into practice.
The framework outlines the relations between formulated variables and explains the major factors explaining the formulation of hypotheses and their application to the research problem. The variables are established regarding the research problem and the major objectives of the research. Considering the fact that it is vital to determine factors reducing cybercrime, the variables include cybercrime mitigation, organizational learning capability, organizational security culture, and perceived cybercrime risk. These phenomena are interconnected and formulate a system that should be evaluated to acquire the improved vision of the main processes related to the research problem.
The theoretical coherence of the research study comes from its alignment with the existing research on the topic and the employment of the major assumptions offered by other authors. Moreover, the study combines the theory and reality, which means that it suggests conclusions that might possess high practical utility and can be used by the educational establishments in the UAE to improve their ability to resist cybercrime. Research findings can be used to protect students and teachers’ personal data from attacks, theft, or its use for various purposes. Under these conditions, the theory collected in terms of the research study is vital for resolving practical issues peculiar to the educational sector of the UAE. Moreover, as far as the research rests on cyberattack theory, and organizational learning approaches, combining these two frameworks, it contributes to the emergence of a new, more practical paradigm that can fill the existing gap in knowledge and help to attain better results.
The study also rests on the four major hypotheses formulated based on theoretical knowledge acquired from the scientific literature. Because most of the reviewed sources acknowledge the significance of training and increased awareness in struggling with cybercrime, the hypotheses focus on investigation how the planned interventions might precondition the shift towards more effective practices and contribute to generating positive results.
Altogether, the given section is vital for the improved vision of the theoretical underpinnings of the study and how they are used to select variables, formulate hypotheses, and select the research methods. The section also creates the link between real-life tasks and the knowledge collected by the literature review. The conceptual framework impacts the choice of the research methods as it outlines the structure of the argument and how it should be presented.
Research Method
Introduction
The chapter provides an overview of the methodology selected for investigating data linked to the research problem and its analysis. The choice of the appropriate methods is crucial for any research study as it preconditions the credibility of findings, their applicability, and practical utility. At the same time, the tools of data collection are aligned to the hypotheses, research questions, goals, and the conceptual framework of the study to guarantee that all identified issues are evaluated correctly. For this reason, the given section provides a detailed description and justification of the choice of the research paradigm, philosophy, and methodology of the research. The choice of a research stance and the approach is explained by outlining the strong and weak sides of both modes and comparing their ability to ensure the proper data collection in terms of the research study. Resting on the information from multiple sources, the given section justifies the decision to employ a specific paradigm and explains the peculiarities of its use.
Moreover, the data analysis methods employed to process the collected information and formulate conclusions are also reviewed in the chapter. Because the study presupposes the involvement of participants, the chapter offers ethical considerations vital to avoid biases and guarantee the observation of the basic participants’ rights. At the same time, there given part of the study suggests information about a pilot study that can be conducted in terms of the research study. The pilot study is a critically important part of any investigation presupposing the involvement of human beings as it helps to realize whether the selected methods are applicable to the situation. For this reason, the chapter offers information about the pilot study as a vital element of the research study framework.
Altogether, the chapter promotes an improved understanding of the scope of the research study and how the study is conducted. It highlights the most important areas of the thesis linked to data collection, working with information, its processing, and using to make conclusions that can be used by other researchers or applied to real-life conditions. The section also sets the ground for enhanced data collection and can be used to create a results section.
Overview of qualitative and quantitative research methods
In general, qualitative and quantitative designs are effective methodologies needed to collect a certain type of data and analyze it to acquire information and knowledge evidencing particular assumptions. The choice of the approach depends on the research question, involvement of participants, and type of desired data needed to conclude about an investigated phenomenon. Thus, qualitative tools are exploratory or interrogative and are focused on collecting information about people’s attitudes, evaluating their needs, visions, or attitudes to a particular phenomenon (Creswell and Guetterman, 2018). From this perspective, using interviews or ethnographic researches, these methods can provide a researcher with a better vision of the research topic. Moreover, qualitative research mainly focuses on working with non-numerical data linked to the concept under investigation (Creswell and Guetterman, 2018). In most cases, this paradigm rests on social sciences, such as psychology and sociology, as investigators are interested in ways society or its representatives respond to a particular issue. For this reason, qualitative research methods help to reveal specific behaviors, reactions, and perceptions among the target audience that are important for investigators and might help to answer research questions (Creswell and Guetterman, 2018). The diversity of data collection methods is linked to the necessity to acquire a complete vision of a particular group and ensure its central peculiarities are taken into account.
The quantitative research design presupposes surveys and observations supported by the statistical analysis tools aiming at answering certain questions and proving hypotheses by numbers and facts (Creswell and Creswell, 2018). This type of investigation presupposes using mainly numerical data to find correlations, interdependencies, causal relationships, or make predictions about specific populations (Creswell and Guetterman, 2018). The correlational, descriptive, and experimental research can be conducted using quantitative data collection methods to acquire the needed information and process it. The central advantage of such tools is their ability to provide accurate and relevant statistical data about a particular concept or phenomenon. For this reason, systematic observation, survey, and secondary data research can be applied to research studies that demand broad numerical data.
Both paradigms provide a researcher with multiple options, meaning that the choice of the appropriate approach depends on the study’s nature and the hypotheses that to be either proven or refuted.
Overview of research philosophy and paradigm in the research
The research philosophy and paradigm of the research are two other critical factors impacting the data collection process and closely linked to the investigated phenomenon. Thus, the research philosophy shows how the research assumption evolves and the nature of knowledge used for the investigation (Zukauskas, Vveinhardt and Andriukaitiene, 2018). The researchers can adhere to a positivist, intepretivist, pragmatist, and realistic research philosophy regarding the scope of their study and the expected outcomes. The positivist framework deals with objective reality. For this reason, an expert is dissociated from various values to acquire accurate data and conclude about the real state of affairs. Realistic philosophy rests on the ideas of positivism and interpretivist conceptions which are vital for analyzing the subjective nature of human beings and their changeable nature (Zukauskas, Vveinhardt and Andriukaitiene, 2018). The pragmatism presupposes that facts are critically important for any research and precondition results. Finally, the interpretivist vision considers the nature of analyzed phenomena applying them to real existing conditions.
As for the research paradigm, it is an approach to thinking about particular research and the basis for the choice of philosophy and research methods (Zukauskas, Vveinhardt and Andriukaitiene, 2018). The three fundamental paradigms are positivist, constructivist, and critical, and their employment presupposes the use of various research methods and data analysis techniques (Zukauskas, Vveinhardt and Andriukaitiene, 2018). The constructivist philosophy views reality as relativistic one (Zukauskas, Vveinhardt and Andriukaitiene, 2018). It is socially and experimentally based, meaning that such methods can be applied to the research. (Zukauskas, Vveinhardt and Andriukaitiene, 2018). The critical framework presupposes the analysis of existing reality by employing the relevant research methods. Finally, the positivist paradigm offers objective tools for analyzing the concepts and their nature (Zukauskas, Vveinhardt and Andriukaitiene, 2018). The difference between these three paradigms serves as the basis for the investigation as they help to understand the choice of a relevant investigation tool and apply them to real conditions.
In such a way, the choice of the research philosophy and the paradigm of the research is fundamental for the following investigation of the selected issues and creation of the basis for the discussion and concluding on the analyzed phenomenon.
Philosophical stance and paradigm of the research
Prior to formulating the research method and approach, it is vital to outline the philosophical stance and paradigm of the research. The proposed research study presupposes an in-depth investigation of the problem of cybercrime related to the functioning of educators in the UAE. It requires the analysis of their attitudes and the evaluation of the existing body of knowledge to acquire the demanded conclusions. For this reason, the positivist research philosophy and paradigm are chosen. It assumes that the analyzed reality is objective, and the acquisition of knowledge is organized in objective ways with no influence of other values (Zukauskas, Vveinhardt and Andriukaitiene, 2018). At the same time, the paradigm is supported by pragmatist ideas because of the importance of knowledge, which is derived from experience and can be used for offering recommendations (Haig, 2018).
Employment of the given paradigm also offers several advantages to researchers. First, the positivist approach helps to set, validate, and analyze the hypotheses needed to investigate a certain problem in terms of the study. The reliability and the reliance on quantitative data help to outline patterns and trends peculiar to a particular issue. (Creswell and Guetterman, 2018). At the same time, it offers a certain degree of freedom to a researcher, meaning that he/she can select among the existing approaches and apply the most effective one (Creswell and Guetterman, 2018). Another advantage is the representative nature of the paradigm as it offers reliable data that can prove or refute certain regularities.
Moreover, the positivist research paradigm helps to show existing patterns and trends. Considering the fact that the research goal is to determine the effect of cybercrime on the educational sector of the UAE, the ability to acquire information about current trends becomes highly valuable as it helps to get the improved vision of how the sector functions and that issues affect it at the moment.
In such a way, the goal of the study, the main research questions, and the need to collect information about particular trends affect the choice. Adherence to the given paradigm helps to select appropriate research methods and improve data collection to guarantee the credibility of findings.
Justification of quantitative and quantitative research methods
The proposed study employs the quantitative research paradigm as the major data collection method. The choice of the given approach is justified by several factors. First, the positivist philosophy and paradigm presuppose quantitative tools to gather objective data and analyze it, avoiding subjectivity (Creswell and Creswell, 2018). At the same time, the qualitative methods are more effective in testing theories or hypotheses and proving their relevance regarding the current situation. Second, the use of the quantitative data collection tools also presupposes creation and distributing surveys as the effective data collection tools providing researchers with information vital for the investigation. Third, quantitative data can be better interpreted because of the absence of the context and other factors that can impact results. Nevertheless, the theoretical basis for the study is formed by using the literature review tool, which is traditionally viewed as a qualitative data collection method. For this reason, it is possible to conclude that the study adheres to the mixed quantitative-qualitative approach. The qualitative method helps to analyze literature and create the basis for theorizing, while quantitative elements are used to either prove or refute formulated hypotheses.
The choice of research methods can also be justified by appealing to the research problem. It sounds in the following way:
Cybercrime is all-pervasive in educational institutions across the globe, including the UAE. However, we know little about antecedents of cybercrime in educational institutions, and that poor understanding of it, along with the absence of relevant tools available to teachers, precondition the deterioration of the situation (Imranuddin, 2017; Matsumoto, 2019). Such a prevailing situation calls for the designing and implementation of a cybersecurity model and specific guidelines to arrest cybercrime rates in educational establishments of the UAE.
It means that the chosen methods must be capable of investigating this problem and helping to answer the major research questions. From this perspective, the qualitative-quantitative framework helps to acquire data about cybercrime accidents in the educational institutions of the UAE. It helps to analyze the experiences of educators regarding their ability to resist crime and get new ways of managing the educational process to create a safe environment for students and protect them from malefactors.
The survey and statistical tools are viewed as the main data collection methods. Because of the need to assess and evaluate teachers’ performance in terms of cybercrime, they are considered sufficient to cooperate with the participants of the research. Information provided by them can help to determine the effectiveness of the proposed guidelines and changes (Haig, 2018). Moreover, the facilitators and inhibitors of cybercrime and their impact on the functioning of educational establishments can also be analyzed by employing the given paradigm. In such a way, the use of the approach is justified by the nature of the study and the scope of the research problem. It is vital to acquire information about educators’ experiences and their ability to resist the growing wave of cybercrime by applying innovative solutions and methods.
Research approach
The study also employs a deductive research approach. The given model presupposes the in-depth analysis of other research studies and theories linked to the phenomenon or issue under research to acquire an improved understanding of the concept. At the same time, deductive reasoning also means testing already existing hypotheses and their discussion by using data collected in the course of the research (Creswell and Guetterman, 2018). Considering the fact that the offered study already has four hypotheses formulated regarding the current situation in the educational sphere of the UAE, the use of the deductive approach is viewed as the preferable option to organize the study and test the assumptions by processing data acquired from participants (Creswell and Creswell, 2018). Deductive reasoning also correlates with the positivist philosophy and the quantitative methods to collect data and employ it to prove or refute specific theories and suggestions.
The choice of the research approach is also linked to the research problem. As stated previously, cybercrime remains the major threat for educational establishments of the UAE, and teachers have to be ready to struggle with it. The analysis of their preparedness levels and the ability to learn new information to resist crime can be performed by using deductive reasoning (Creswell and Guetterman, 2018). It is possible to assume that their level of preparedness is sufficient to operate within the given complex environment, and teachers demonstrate satisfactory results when learning new skills and competencies needed to struggle with cybercriminals. This assumption can be either proven or refuted by using deducting reasoning (Creswell and Guetterman, 2018). Cogitating about the given statements, it is possible to employ data collection methods and gather the information that is critical for making conclusions.
The deductive model offers additional tools for working with existing hypotheses, which is vital in terms of the given research problem. Considering these factors, it is possible to justify the employment of this model and the beneficial results acquired due to its use. Moreover, it is useful in analyzing teachers’ experiences and visions of the nagging problem. For this reason, the study follows the deductive model.
Pilot study
A pilot study is a critical part of any research study needed. It helps to test data collection methods, research protocols, sampling strategies, and analysis methods preparing for the final and larger study. At the same time, it allows to avoid failures, biases, and problems during the final stage of the research study and contributes to the acquisition of a better vision of how to conduct a study and what areas or factors are of the top priority. For this reason, a pilot study is also an important part of working on the proposed research study and guaranteeing the absence of critical problems.
The pilot study is aligned to the research problem to ensure an in-depth investigation of the issue under concern. Thus, cybercrime as a phenomenon peculiar to most modern institutions is investigated in terms of its effects on teachers and their ability to resist new challenges (Imranuddin, 2017; Matsumoto, 2019). That is why the pilot study focuses on using the research paradigm, philosophy, and methods mentioned above. The final intervention presupposing data collection among participants can be corrected using the results of this pilot study. For this reason, by aligning the pilot study to the research problem, it is possible to meet the goals of the research study.
A pilot study can be conducted in one educational establishment of the UAE among the educators working there. A survey with the questions needed to cover the most important areas can be distributed among the participants and check whether the instructions are clear and individuals can follow them. The limited number of participants helps to test the survey, research protocol and improve working with individuals to avoid bias and ethical issues that might emerge. For the pilot study, 20 participants will be used to test the effectiveness of the data collection tool. Specialists working in the UAE higher education will be interviewed. Results of the given pilot study are critical as they are used to introduce the necessary changes to the existing model and make it more effective in collecting data linked to the problem. Furthermore, the pilot study is critical for validating the research study and gathering information needed to conclude about the applicability of the chosen paradigm and its contribution to data collection.
Sample
The sample in the study consists of teaching and non-teaching employees of the tertiary level educational institutions in the UAE. A questionnaire is available in the extant literature on cybercrime risk awareness culture, knowledge management system, perceived cybercrime risk, and organizational performance, which are rated by the sample in this study on a 6-point Likert scale. As stated previously, for the pilot study, a sample of 20 individuals can be sufficient. It shows whether the selected strategy is applicable to the research and can be used in practice. Moreover, the pilot study demonstrates mistakes in surveys or using scales and correct them prior to the main phase of the research. However, for the final research study, the involvement of a bigger number of participants can be desired to collect data needed to prove or refute the hypotheses and avoid biases or corrupted information portions. A minimal sample cannot help to acquire the improved vision of the problem and outline the existing regularities. However, a maximal sample makes the study overcomplicated and might precondition the emergence of biased data. Moreover, for quantitative researches, comparatively big samples are demanded to acquire statistical information that can either support or refute the existing statements. For this reason, data from 300 participants can enhance the relevance and practical utility of the research and create the basis for the discussion of the effectiveness of proposed interventions, their utility, and the ability to promote positive change in the educational sector of the UAE. Choosing the margin of error, confidence level 95%, and a standard deviation of 0.5, and using the formula, it is possible to conclude that 300 participants suffice (Creswell and Guetterman, 2018). It guarantees the credibility of collected data and avoid flaws or using corrupted facts. Three hundred respondents can provide high confidence levels, moreover, they represent a significant part of teachers affected by cybercrime. 300 questionnaires will be sent to the participants. The given number can also help to achieve the desired confidence levels and guarantee that the results of the study can be used in the following research studies because of the absence of biased or corrupted data portions.
In such a way, the sample size is preconditioned by the need to achieve the desired confidence levels and avoid critical deterioration of data. The target populations can provide detailed answers and create the basis for further research. The current research problem, which is the growing cybercrime rates, also influences the choice of setting, number of participants, and data collection tool.
Sampling strategy
The nature of the research presupposes the need for specific data acquired by working with a narrow target audience. It must possess the experience of functioning in terms of the UAE education sector and be at risk of being affected by cybercrime. Moreover, they have the need for data protection methods and guidelines that can help them to improve their functioning and attain better outcomes. Regarding these peculiarities, non-probability purposive sampling is employed to select participants for the study and collect data among them (Creswell and Creswell, 2018). Non-probability sampling presupposes that there is no random selection. A list of criteria is used to select people for the research. These features help to improve data collection and ensure that the authors acquire data vital for their research (Creswell and Creswell, 2018). Additionally, non-probability sampling avoids including random populations in research, which can be beneficial when working with broad groups (Creswell and Creswell, 2018). As for the research study, non-probability sampling helps to create a pool of teachers and specialists who have the needed experiences and can provide statistically relevant data.
Purposive, or judgment sampling, presupposes that a selection of participants using personal vision of the research study and what features of individuals might help to acquire the detailed results. However, because of the peculiarities of the research problem and the target population, voluntary response sampling can be employed, as teachers can be busy, and their involvement demands much free time. Using non-probability and purposive sampling, it is possible to create a pool of respondents who meet the requirements for the target population.
In such a way, adherence to this strategy ensures that all individuals possess the needed experience and knowledge to monitor the impact of proposed interventions and either prove or refute formulated hypotheses. For this reason, non-probability sampling is viewed as a beneficial approach to forming the pool of participants and ensuring they can share information significant for the research and the whole research study. Moreover, this strategy provides much space for investigators as they are free to select individuals considering their availability and readiness to take part in the research study.
Data collection methods
The quantitative research paradigm offers a wide variety of methods and tools that can be used to collect data. Additionally, the deductive approach and the positivist paradigm also influence the choice of methods. For the given research study, a survey seems the preferable option as one guaranteeing the most effective data collection. First, it increases the convenience as questionnaires can be distributed online among the participants of the research. It also becomes topical regarding the Covid-19 pandemic and the need to observe social distancing. Moreover, educators taking part in the study might have limited free time, for this reason, they can answer all questions when they have an appropriate opportunity for it. For this reason, it is expected that 300 questionnaires are sent to the participants of the research.
Another advantage of the survey is its ability to get relevant feedback regarding the investigated problem. All participants can show their real attitudes and emotions by providing their answers and additional information (Creswell and Guetterman, 2018). Surveys are also more direct as they can ask questions from the participants and improve the vision of the problem (Creswell and Guetterman, 2018). The ease of creation and implementation also justifies the use of this method of data collection as they can be utilized in different situations and environments.
It is also expected to conduct about 50 interviews to collect data. The interview is another potent tool that is used in mixed researches to acquire information about a particular sample, its attitudes to the problem under research, and visions of the future. Regarding the research problem, integration of interviews seems the preferable option as it ensures that accurate and relevant information is acquired it also provides the chance to realize the current state of the education sector in the UAE and consider the use of various methods to improve the situation and resist cybercrime. Supporting information acquired by surveys with interviews, it is possible to create a complete image and conclude about the relevance of particular theories.
The literature review conducted to create the theoretical basis for the research is another data collection method as it helps to acquire an improved understanding of the current state of the problem and ensure that the formulated hypotheses are relevant. These data collection methods also impact the analysis tools and the results.
Data analysis
Quantitative research methods presuppose working with numerical data and processing to acquire desired results and use them when discussing the hypothesis. For this reason, the structural equation modeling (SEM) technique, leveraging SPSS and AMOS statistical software, are be used to examine all four hypotheses of the study. The choice of these approaches is explained by their effectiveness and the ability to work with numerical data provided by the participants (Muijs, 2010). SEM is a set of specified techniques of statistical data analysis needed to measure and analyze relations between different variables. In such a way, it can be implied to evaluate the correlation between cybercrime mitigation, organizational learning capability, organizational security culture, and perceived cybercrime risk. The given variables create the conceptual framework of the study, meaning that by applying the SEM technique to data acquired from participants, it is possible to determine how the organizational learning capability and security culture affect cybercrime mitigation and risk. SPSS and AMOS statistical software are employed to process numerical data portions acquired from individuals and represent them.
Additionally, SEM can be used to determine whether the offered hypotheses are relevant and can be proven by information acquired in the course of the study. The nature of relations discovered by applying this analysis tool demonstrates whether a variable affects an investigated issue (Muijs, 2010). Using SEM regarding the research problem, it is possible to discover whether teachers’ ability to learn new protection measures and their training can help to minimize the level of threat and mitigate risks. Under these conditions, statistical methods seem the appropriate choice for the study. Moreover, the tools are characterized by the high reliability and the high accuracy of results, which is needed to discuss findings and provide credible evidence of the major assumptions.
Ethical consideration of the research
The study observes the existing code of ethics in several ways. Because the research presupposes the involvement of individuals to collect data, it is vital to consider all ethical issues and the Code of Ethics related to any investigation. All participants provide their informed consent to take part in the study and share their personal data. It is a fundamental part of the study needed to avoid conflicts and problems. The filled forms are provided by all participants before the start of the research. It is a critical demand to participation as it guarantees that involved participants realize the scope of the research study, its focus, and the nature of questions they are asked. Persons who have not provided informed consent forms cannot be involved as it can deteriorate data and precondition the emergence of ethical issues. Second, anonymity and confidentiality is guaranteed to respondents and their answers. It means that survey blanks do not have any personal information that can disclose a participant. Because the focus of the research is to investigate the nature of current experience, how cybercrime affects establishments, and conclude about possible interventions, the inclusion of participants’ names is unnecessary. At the same time, the participation is voluntary, and they are provided with an opportunity to leave at any stage of the research study. In such a case, there are no penalties or any other actions that might affect a person. These three major conditions are fundamental for considering all ethical issues and avoiding undesired outcomes or data corruption. Finally, the publication of data is also made regarding the participants’ approval. Observation of these major aspects helps to follow the Code of ethics for research involving human beings and attain the high relevance and accuracy of data.
Validation and verification of the model
The application of any model to real-life conditions demands its verification and validation as the guarantee of its correspondence to ethical standards and observation of the rules of the research. For this reason, the letter of verification supports the research study, meaning that the study has been submitted to the University’s Institutional Review Board/Ethics Committee for review regarding research with human subjects. Additionally, the verification of the model presupposes its approval by the supervisor.
The model and outcomes of the study can be verified by comparing results with previously published papers devoted to the same issue. The effectiveness of learning in terms of organization and its positive impact on employees are the object of numerous research papers, meaning that by comparing results, it is possible to ensure that they are credible and have a significant practical utility. Manuscripts with parameters as close as it is possible can be taken to analyze them and make a conclusion.
Experimental validation is another possible way to prove the model and its relevance. It can be performed by simulation using the parameters acquired in the course of the research. Otherwise, a controlled experiment in a specific educational establishment of the UAE can be conducted to monitor the changes in the work of teachers and correlate them with the provided research findings.
Finally, applying benchmarks and consulting with experts in the field, it is also possible to prove the validity of the proposed model and its applicability to real-life situations.
Using these options, the validity of the research study can be checked. Moreover, it guarantees that the research study design is sufficient and can help to attain the desired outcomes and evaluate the outlined research problem.
Chapter summary
Altogether, the chapter outlines the methods, paradigm, and philosophy of the research. It explains the choice of the positivist approach supported by the mixed, quantitative-qualitative design needed to acquire the desired data and used it for discussion. The choice of the methodology is linked to the research problem. The issue under investigation is how cybercrime affects educational establishments of the UAE and whether providing additional training for teachers and their education can help to reduce risks and mitigate them better. For this reason, the qualitative-quantitative design assists in collecting both numerical and personal information, process it, and offer reliable conclusions. The adherence to deductive reasoning helps to evaluate the existing literature and prove or refute the hypotheses. The section identifies that non-probability sampling is used to select participants for the research. It provides the freedom to include individuals regarding the demanded set of skills and create the pool of specialists relevant for the research. The data analysis is performed using statistical tools. The chapter outlines the ethical considerations of the research study and emphasizes the need to follow the code of ethics to avoid issues and corruption of data. Validation and verification of the model can be performed by comparing the study results with previous works that have similar parameters. Additionally, simulation or applying specific benchmarks can prove the relevance of outcomes and their applicability to real-life situations. Altogether, the section explains the research methodology and its choice in terms of the goals of the study, its hypotheses, and objectives.
Reference List
ABI Research. [N.D.]. Global cybersecurity index. Conceptual framework. [Online]. Web.
Aliyu, A., Maglaras, L., He, Y., Yevseyeva, I., Boiten, E., Cook, A., and Janicke, H., 2020. A holistic cybersecurity maturity assessment framework for higher education institutions in the United Kingdom. Applied Sciences, 10(10), pp. 3660.
CPC.gov. [N.D.]. About the UAE. [Online]. Web.
Al Ahbabi, N.M., 2019. Key stakeholders’ perceptions about school improvement strategies in UAE. Improving Schools, 22(2), pp.113-129.
AMEinfo Staff. 2020. Cybercrime in education – UAE schools navigating the post-pandemic future. [Online]. Web.
Aydos, M., Vural, Y. and Tekerek, A., 2019. Assessing risks and threats with layered approach to Internet of Things security. Measurement and Control, 52(5-6), pp.338-353.
Barfoot, R., Ellaby, S., Hutchinson, K., Osman, R., Sfeir, A., BouMalhab, N., Ford, R., Lovell, G., Parata, E. and Wilkinson, D. 2020. COVID-19 education: ongoing issues affecting the education sector across the GCC. [Online]. Web.
Basten, D. and Haamann, T., 2018. Approaches for organizational learning: a literature review. SAGE Open. [Online].
Castelo, M. 2020. Cyberattacks increasingly threaten schools — here’s what to know. EdTech: Security. [Online]. Web.
Coopey, J., 1995. The learning organization, power, politics and ideology introduction. Management learning, 26(2), pp. 193-213.
Corradini, I., 2020. Building a cybersecurity culture in organizations: how to bridge the gap between people and digital technology. Springer.
Creswell, J.W. and Creswell, J.D., 2017. Research design: Qualitative, quantitative, and mixed methods approaches. Sage publications.
Creswell, J.W., 2002. Educational research: Planning, conducting, and evaluating quantitative (pp. 146-166). Upper Saddle River, NJ: Prentice Hall.
U.ae. [N.D.]. Cyber safety and digital security. [Online]. Web.
Dasgupta, D., Akhtar, Z. and Sen, S., 2020. Machine learning in cybersecurity: a comprehensive survey. The Journal of Defense Modeling and Simulation, p.1548512920951275.
Deloitte. 2018. Elevating cybersecurity on the higher education leadership agenda. [Online]. Web.
Finnerty, K., Motha, H., Shah, J., White, Y., Button, M. and Wang, V., 2018. Cyber security breaches survey 2018: Statistical release.
Diffee, E. and Datta, P., 2018. Cybersecurity: the three-headed Janus. Journal of Information Technology Teaching Cases, 8(2), pp.161-171.
DLA Piper. 2019. Data protection laws of the world. UAE general. [Online]. Web.
Iriqat, Y.M. and Molok, N.N.A., 2019, April. Information security policy perceived compliance among staff in palestine universities: an empirical pilot study. In 2019 IEEE Jordan International Joint Conference on Electrical Engineering and Information Technology (JEEIT) (pp. 580-585). IEEE.
European Commission. 2012. Special Eurobarometer 390. Cyber security. [Online]. Web.
Foster, J. [N.D.]. 21 terrifying cyber crime statistics. [Online]. Web.
Garvin, D. A., Edmondson, A. C., and Gino, F., 2008. Is yours a learning organization?. Harvard business review, 86(3), pp. 109.
GMI. UAE Internet Statistics 2020. [Online]. Web.
Government Offices of Sweden. 2017. A national cyber security strategy. [Online]. Web.
Haig, B.D., 2013. The philosophy of quantitative methods. The Oxford handbook of quantitative methods, 1, pp.7-31.
Holt, T.J., 2018. Regulating cybercrime through law enforcement and industry mechanisms. The ANNALS of the American Academy of Political and Social Science, 679(1), pp.140-157.
Holt, T.J., Bossler, A.M. and Seigfried-Spellar, K.C., 2015. Cybercrime and digital forensics: An introduction. Routledge.
Hopkin, P., 2018. Fundamentals of risk management: understanding, evaluating and implementing effective risk management. Kogan Page.
Imranuddin, M., 2017. A study of cyber laws in the united arab emirates.
Jerez-Gomez, P., Céspedes-Lorente, J. and Valle-Cabrera, R., 2005. Organizational learning capability: a proposal of measurement. Journal of business research, 58(6), pp.715-725.
Jiang, S. and Rafeeq, A., 2019. Connecting the Classroom with the Newsroom in the Digital Age: An Investigation of Journalism Education in the UAE, UK and USA. Asia Pacific Media Educator, 29(1), pp.3-22.
Julisch, K., 2013. Understanding and overcoming cyber security anti-patterns. Computer Networks, 57(10), pp. 2206-2211.
Knapp, K. J., Marshall, T. E., Kelly Rainer, R., and Nelson Ford, F. 2006. Information security: management’s effect on culture and policy. Information Management and Computer Security, 14(1), pp. 24-36.
Kremling, J. and Parker, A.M.S., 2017. Cyberspace, cybersecurity, and cybercrime. SAGE Publications.
Lassoued, I. and Fawcett, A. 2020. The new world of tech: cybercrime and cybersecurity in the UAE. [Online]. Web.
Leukfeldt, E.R. and Holt, T.J., 2020. Examining the social organization practices of cybercriminals in the Netherlands online and offline. International journal of offender therapy and comparative criminology, 64(5), pp.522-538.
Liu, C. W., Huang, P., and Lucas Jr, H. C., 2020. Centralized IT decision making and cybersecurity breaches: Evidence from US higher education institutions. Journal of Management Information Systems, 37(3), pp. 758-787.
Lord, N. and Levi, M., 2017. Organizing the finances for and the finances from transnational corporate bribery. European Journal of Criminology, 14(3), pp.365-389.
Martin, J.D., Naqvi, S.S. and Schoenbach, K., 2019. Attribute substitution and stereotypes about the online Arab public sphere: Predictors of concerns about Internet surveillance in five Arab countries. new media & society, 21(5), pp.1085-1104.
Matsumoto, A., 2019. Literature review on education reform in the UAE. International Journal of Educational Reform, 28(1), pp.4-23.
Mello, S., 2018. Data Breaches in Higher Education Institutions.
The National. 2020. Cost of data breaches in Saudi Arabia and UAE climbed 9.4% in 2019. The National. [Online]. Web.
Neyadi, A., Kaabi, A., Kaabi, L., Al Ghufli, M., Shamsi, M., and Khan, M. 2015. Internet governance & cyber crimes in UAE. International Journal of Scientific & Technology Research. 4(11), pp. 350-357.
Nikolaeva, S.G. and Nathan-Roberts, D., 2016, September. Various Aspects of the Human Factor in Online Education: Quantitative Literature Review. In Proceedings of the Human Factors and Ergonomics Society Annual Meeting (Vol. 60, No. 1, pp. 1279-1283). Sage CA: Los Angeles, CA: SAGE Publications.
Nuzhat, S., 2020. Globalization of Education in UAE: The Local Legislative Education Policies for International Branch Campuses and Its Tensions Given the Political, Religious, and Cultural Differences. Journal of Education, p.0022057420914917.
Parsons, K.M., Young, E., Butavicius, M.A., McCormac, A., Pattinson, M.R. and Jerram, C., 2015. The influence of organizational information security culture on information security decision making. Journal of Cognitive Engineering and Decision Making, 9(2), pp.117-129.
Payne, B.K. 2020. Defining cybercrime. In: Holt, T. and Bossler, A. eds. The Palgrave handbook of international cybercrime and cyberdeviance. London: Palgrave Macmillan, pp.3-25.
Philip, J. and Salimath, M.S., 2018. A value proposition for cyberspace management in organizations. Business Information Review, 35(3), pp.122-127.
Powell, B., Chipman, J., Schloss, L. and Riggan, M. 2020. Cybersecurity best practices in USA. [Online]. Web.
Preis, B. and Susskind, L., 2020. Municipal Cybersecurity: More Work Needs to be Done. Urban Affairs Review, p.1078087420973760.
Sergon, V. 2020. Guide to the education system in the United Arab Emirates. Expatica. [Online]. Web.
Statista. [N.D.]. Statistics about Internet in United Arab Emirates. [Online]. Web.
Stone, N.J., 2017, September. Online education: The how, who, where, and when. In Proceedings of the Human Factors and Ergonomics Society Annual Meeting (Vol. 61, No. 1, pp. 1237-1241). Sage CA: Los Angeles, CA: SAGE Publications.
Santander Trade. [N.D.]. United Arab Emirates: economic and political outline. [Online]. Web.
van de Weijer, S.G., Leukfeldt, R. and Bernasco, W., 2019. Determinants of reporting cybercrime: A comparison between identity theft, consumer fraud, and hacking. European Journal of Criminology, 16(4), pp.486-508.
Smerek, R., 2017. Organizational learning and performance: the science and practice of building a learning culture. Oxford University Press.
Williams, L.J. and Anderson, S.E., 1991. Job satisfaction and organizational commitment as predictors of organizational citizenship and in-role behaviors. Journal of management, 17(3), pp.601-617.
The World Bank. 2019. Individuals using the Internet (% of population) – United Arab Emirates. [Online]. Web.
Wilner, A.S., 2018. Cybersecurity and its discontents: Artificial intelligence, the Internet of Things, and digital misinformation. International Journal, 73(2), pp.308-316.
Yar, M. and Steinmetz, K.F., 2019. Cybercrime and society. Sage.
Zhuang, R., Bardas, A.G., DeLoach, S.A. and Ou, X., 2015. A theory of cyber attacks: A step towards analyzing MTD systems. In Proceedings of the second ACM workshop on moving target defense (pp. 11-20).
Žukauskas, P., Vveinhardt, J. and Andriukaitienė, R., 2018. Philosophy and paradigm of scientific research. Management Culture and Corporate Social Responsibility, 121.
Appendices
Appendix A. Questionnaire
Questionnaire
Appendix B. Consent Letter
Dear Participant!
At the moment, I am undertaking a PhD called “A model for managing and mitigating cybercrime risks: Case UAE educational institutions.” My research revolves around cybercrime, its scope, and how it affects the work of educational establishments. To achieve the project’s goal. it is vital to interview teachers from the UAE to determine their role in existing cybercrime systems and models, awareness, and the ability to resist risks. The central purpose of the project is to examine the influence of perceived cybercrime risks in educational institutions of the UAE. Moreover, this research study intends to fill the research gap in existing literature devoted to the problem of cybercrime and to outline how the effective guidelines and proposed cybersecurity model can be used to manage and mitigate in UAE educational institutions. For this reason, your answers to are vital for a better understanding of these factors and the credibility of findings.
I would be grateful if you help me in conducting the research sharing information and your knowledge. The questionnaire (please see the appendix) will take no longer than 30 minutes to complete and give data needed to determine the current state of cybersecurity in the educational establishments of the UAE. You are guaranteed that your confidentiality will be preserved, and no harm will be done to you or the organization by our project. I hope that the research will help to fill the existing knowledge gap and enhance the work of educational establishments in the UAE.
If you have any questions, you can always contact me using the following ways:
- Email__________________
- Phone number______________________
I greatly appreciate your participation and readiness to help and share some important information.
Yours sincerely,
PhD Research student.
Appendix C. PHD Timetable