Introduction
Virtualization and cloud computing are new technologies that have widely been adopted by many organizations offering computing services. Among the reasons for the trend are that many organizations have found virtualization and cloud computing cost effective. That has strongly reinforced the need to understand the technologies (cloud computing and Virtualization), benefits associated with the technologies, and the baseline reasons for organizations such as Goolge.com to move towards the virtualization and cloud computing technologies to offer their services despite the security risks associated with the technologies. Typically, virtualization is a technology that provides a platform for offering services on the cloud. That establishes a strong link between virtualization and cloud computing. However, cloud computing takes virtualization to the next level in computing by offering cloud-computing services on the virtualization platform. Both virtualization and cloud computing are susceptible to a number of potential security risks that need to be evaluated and mechanisms integrated into the systems to enhance security and ensure data integrity and confidentiality in the users of the technologies. Cloud computing is susceptible to security risks such as confidentiality, availability, and data integrity. On the other hand, virtualization is susceptible to security risks from a hostile environment including modification of programs and data with the potential to damage the functionality of the entire system.
Context of the problem
Many organizations have shifted from the old computing models to new technologies in the provision of computing services. Typically, two technologies widely used in the provision computing services include virtualization and cloud computing. However, virtualization and cloud computing technologies are susceptible to security risks and threats despite many organizations adopting the new computing approach. In virtualization and cloud computing, users make use of powerful computers which are remotely located. Despite the effectiveness of this technique therefore there are question which have been raised in light of the remoteness of the computers and specifically the sharing on a common hardware. There is a general feeling that this technique makes information vulnerable to hacking. Assistant professor Dr. Xuxian Jiang from the North Carolina State University argued that:
One of the major threats to virtualization — and cloud computing — is malicious software that enables computer viruses or other malware that have compromised one customer’s system to spread to the underlying hypervisor and, ultimately, to the systems of other customers. In short, a key concern is that one cloud computing customer could download a virus — such as one that steals user data — and then spread that virus to the systems of all the other customers. (North Carolina State University, 2010, p. 1)
Studies and researches are been carried out to find ways of keeping the hypervisor absolutely isolated and thus safe from interference from other users. Thus, the research will endeavor to establish and crystallize an understanding of both technologies to provide concrete reasons for the trend towards the technologies witnessed in large computing firms and other organizations that offer services through the cloud. Therefore, the research will endeavor to establish the relationship between the technologies, security issues, and the trend despite the security issues.
Problem Statement
Virtualization and cloud computing are new and complementary technologies organizations have adopted in offering computing services, causing many organizations a lot of anxiety due to the security risks and threats associated with the technologies. Thus, the need to understand comprehensively the theoretical propositions of the technologies, their relationships, and security issues associated with the technologies. That has further reinforced the need to understand the rationale of the observed trend where organizations are moving towards the adoption of the technologies despite the security threats associated with virtualization and cloud computing.
Hypothesis
Virtualization and cloud computing are two technologies that complement each other, with many organizations shifting from the old computing approaches to the new computing technologies in view of the benefits inherent in the technologies despite the security challenges experienced with the adoption of the technologies.
Primary Research Question
The primary research question will give the general direction of approach of this paper by taking into context the problem statement above. in a move to keep abreast with current changes in technology and ensuring efficiency in the provision of computing services, organizations are adopting new technologies in their systems. Virtualization and cloud computing are widely being implemented by different organization hence the need to comprehensively examine these technologies in the light of the utility obtained and security threats they pose. This is achieved by examining the following research questions.
Research questions
- What are the challenges that organizations face when achieving the goal of provision of computing services?
- What organizations have included virtualization and cloud computing and were on a path to real accomplishments in the provision of computing services?
- How can an organization successfully conceptualize, develop and implement Information Technology and apply appropriate strategic planning principles and practices that will embrace and include virtualization and cloud computing in their provision of computing services?
Terms and definitions
Computer – A machine made of hardware, software, peripherals, and other accessories. The machine requires software consisting of programs and applications to function as intended.
Computer Security – Refers to the implementation of standards and guidelines, the technical and software applications that would protect the computer system, as well as the information stored and transferred electronically from one computer to another.
Cloud computing – A computing technique that offers computing services to clients such as software, data, and storage facilities on a shared platform. Cloud computing is therefore a service.
Virtualization – An automatic computing technique that allows multiple operating systems to run on existing hardware platform upon which other programs execute. Virtualization provides incremental growth of the computing environment to accommodate rising computing needs without increasing the hardware platform.
Limitations
Significance tests and statistical data analysis will not be conducted to evaluate the impact of virtualization and cloud computing on organizations moving from old computing models to the new technologies.
Delimitations
To ensure the validity of the results, the study uses delimitations including using a few case examples including Google.com while dwelling more on academic study to answer the research questions. Thus, the study will concentrate on theoretical propositions and academic research to try to establish a comprehensive baseline of understanding virtualization, cloud computing, the relationship between the technologies, and benefits organization derive from these technologies.
Assumptions
The main assumption is that the findings are commensurate with computing needs in the practical environment.
Theoretical Support
Virtualization
Virtualization is defined as “the ability to run multiple operating systems on a single physical system and share the underlying hardware resources” (Wilde & Hubber, n.d). On the other hand, cloud computing is defined as “the provisioning of services in a timely (near on instant), on-demand manner, to allow the scaling up and down of resources” (Wilde & Hubber, n.d). Thus, virtualization is one of the dynamic factors of cloud computing that provide an interoperable platform for cloud computing. Typically, virtualization provides platforms such as operating systems, hardware, and software resources upon which cloud computing offers on demand services with scalability options based on demand for services. Typically, virtualization has its foundation on the concept of a virtual machine. A virtual machine executes its tasks on a physical platform under the supervisory mode of a virtual machine monitor (VMM), often referred to as hypervisor. Xen. VMM is a product that belongs to the family of open source software products (Krutz & Vines, 2010).
Virtualization enables the implementation of cloud computing by abstracting software and other computing platforms from users while hosting multiple operating systems to execute tasks concurrently (Virtualization Overview, 2006). It is important to note that virtualization and cloud computing are complimentary in offering services to the user. However, virtualization allows for optimization of utility and grid computing technologies in the cloud and supports the dynamic pooling of resources towards the latter goal (Krutz & Vines, 2010). Virtualization is therefore viewed as a technology that allows IT resources to be virtualized at different levels of data storage, server services. In addition to that, virtualization allows for the multiplexing of network operating systems. Virtualization has experienced an exponential growth with organizations, individual customers, and corporate organizations in the recent past (Virtualization Overview, 2006).
Impact of Virtualization
The impact of virtualization will be studied has shown throughout in CPU resource utilization as one of the significant benefits of virtualization. Typically, the benefit is realized by allowing fewer CPU cycles and support for off-host architecture in minimizing performance problems due to large amounts of data traffic in a virtual environment (Krutz & Vines, 2010).
Organizations intending to upgrade their IT infrastructure find the process technically less intensive, less demanding, and simplified. In addition to that, virtualization allows users and stakeholders to own the entire migration process from old to new technologies in different environments (Virtualization Overview, 2006).
One such is the thin environment. In a thin environment, a server with a capacity of 200 GB, which is intended to be scaled to 400 GB, will have to acquire a complete physical capacity similar to 400 GB. On the other hand, dynamic allocation of space in a similar server in a virtualized environment for available space can be increment online and allocations are serviced on demand without any detrimental effect on users and the performance of the server. In addition to that, virtualization enables efficient utilization of energy and other performance related functions. Virtualization also allows for incremental addition or scaling of resources on demand in an efficient manner. Other additional benefits include fault tolerance, economies of scale, data servers, usage protocols on server levels, and virtual machine mobility. Based on the benefits realized from the use of virtualization technologies, different organizations have pursued integration and use of virtualization technologies to exploit the benefits associated with the technology. One typical example is VMWARE (Scheffy, 2007).
Organizations using Virtualization
Many organizations have adopted virtualization technologies based on a range of benefits already outlined above. Among the firms in the list include VMWARE. VMWARE is an example of a firm that has pioneered a number of virtualization technologies including the VMware pioneered x86-based virtual technology in 1988 which exploited the concept of software and hardware virtualization in a virtual environment. In a typical VMware environment, a uniform image created in a virtual environment by the virtual machine consists of different servers across which workloads are balanced in a virtual center. The platform thus created provides a baseline for operating systems, which also provide a platform for other applications and utilities to execute in the virtual environment.
Organizations have experienced the need and cost savings related to IT services and tasks leading to a reduction in the number of staff in their IT departments. One such approach of downsizing and saving on the cost of IT staff is automation. Thus, organizations have realized ne of the best strategies to include cloud computing and virtualization. However, moving to the new computing environments have raised the concern for the need for organizations to emphasize on security and related needs to ensure organizational data is kept safe (Redhat, 2007; Lorincz, Redwine & Sheh, 2003).
Virtual PC and Virtualization
A virtual PC is a tool that enables users to exploit the services provided on a virtualized platform to access services from the cloud. That, establishes a strong link between virtualization and cloud computing. The above statement provides the rationale to investigate the virtual PC in relating to virtualization and cloud computing as discussed below.
A virtual PC provides the capabilities to access services for the users by running and accessing different services from the virtualized environment to the cloud. However, different operating systems have different configurations, software, and hardware requirements for virtual PCs (Lorincz, Redwine & Sheh, 2003).
Security in a Virtual Environment
Typically, operating systems security is often compromised, thus usurping system integrity. That demands for a secure root virtual machine to disallow any interference with guest programs from modifying the functionality of the virtual environment. On the other hand, in a cloud-computing environment, security is also of paramount importance to ensure data and applications integrity, discussed under the cloud computing section (Jain, 2007). Nonetheless, virtualization and cloud computing have different security perspectives and implementation strategies are enforced with the main goal of preserving system and data integrity. In the virtualized environment, different strategies used to enforce security at different levels are discussed below.
Security Issues
Detection is one of the technologies used to identify and isolate malware and the security threats with the potential danger to modify data, which might lead to a potential disaster. Typically, various security threats inherent in a virtual environment especially targeting the running environment of a virtual machine are identifiable. One such is the susceptibility of hostility in a virtual environment. These hostilities might lead to corruption of data and procedures in the virtual environment. A number of perspectives detail the security threats and their potential impact in a virtual environment. These include, but not limited to complete compromise, partial compromise, to abnormal compromise of the security of the virtual environment.
Cloud Computing
The services in the cloud are modeled into cloud platform as a service (PaaS), cloud software as a service (SaaS), and cloud infrastructure as services. It is defined as “the provisioning of services in a timely (near on instant), on-demand manner, to allow the scaling up and down of resources” (Wilde & Hubber, n.d). These services define the architecture of cloud computing. Cloud computing is modeled on private, hybrid,community, and public clouds. This technology encapsulates various elements that are integral to its genesis. These include utility computing, to ensure effective service delivery to customers and grid computing that endeavors to provide optimal solutions to computational problems. This approach rivals parallel processing where resources are pooled together to provide optimal solutions to problems through advanced computing powers. In addition to these, autonomic computing is another element that automates a computing device to perform its tasks without external controls as used in breathing systems and other practical areas of applications (Ormandy, n.d).
On the other hand, virtualization from the above definition of cloud computing provides the platform for cloud computing, implying that cloud computing takes virtualization to the next level (Jaeger, Lin & Grimes, 2008).
Cloud computing integrates existing technologies to create the cloud computing concept. Thus, it is a computing solution traversing different application areas in the modern world of Information Technology, which has been experiencing an exponential growth with time. In addition to that, the concept integrates technologies leading to the creation of a new cloud computing architecture defined by cloud access devices that have been expanding with time.These devises are conceptualized in a virtualized environment (Jaeger, Lin & Grimes, 2008).
These technologies include thin clients and browsers for accessing enterprise applications such as SAP and Oracle, high-speed broadband access that forms the backbone of cloud computing, and Server firms and data centers that place demands for large computing capacities. Some of the areas where cloud-computing technologies have been integrated include Google.com. According to Jaeger, Lin & Grimes (2008), Google has pooled together a large number of servers to provide tremendous computing powers for its services.
On the other hand, virtualization is a concept that describes the abstraction of computer resources from applications to end users. It enables the implementation of multi-tenancy on shared and scalable platforms for different tenants and offers dedicated services to customers. Different tasks and task executing environments logically partition physical resources to optimize their usage, as is evident in a Virtual Machine Monitor.
Virtualization comes with a variety of benefits to the consumer. These include abstraction of shared resources such as databases, operating systems, data storages, and applications. To realize the benefits due to virtualization, different environments define and incorporate the concept in different ways. Some of the areas where virtualization has been applied as a platform to implement cloud computing include systems such as sun micro system, Sun xVM in its supervisor environment, and a host of other technologies (Jaeger, Lin & Grimes, 2008).
Virtualization focuses on security issues that span users and service providers. Typically, all forms of external services, customers, and service providers need to work in a secure environment. Service providers therefore endeavor to ensure that cloud-computing infrastructure integrates security measures to prevent inadvertent or intentional modification of files and data while on transmission. Thus, the need for cloud service providers to show evidence of security audits for their services based on evaluations conducted against established benchmarks. One of the auditors for these cloud computing services providers includes SAS 70. A typical example of service providers certified to comply with security needs include Google and Microsoft. On the other hand, security compliance requirements regimes include European Data Privacy Directives, among others (Jaeger, Lin, Lin & Grimes, 2008; Varia, 2008).
Current Situation
Arguments show that cloud computing service providers subject their systems to security audits to create the kind of confidence in users of their services despite the fact that individual users are responsible for the ultimate security of the system. Data is stored at specific locations designated by the customer and not the service provider. That inspires a degree of confidence in the user of the system. Data encryption and segmentation typically provides secure data storage facilities. It is incumbent upon the service provider to use well designed and reliable encryption techniques based on algorithms that are not easy to decrypt. In addition to that, data recovery techniques should be enhanced continuously to stay abreast with currently evolving technologies. Investigations to identify illegal activities should form the basis of detecting frauds and other criminal activities. Cloud computing service providers should never go under. Most of the firms that provide cloud computing services are financially sound and the threat to go under are minimal.
Security Issues
Like a virtualized environment, cloud computing service providers should incorporate self-regulatory measures to ensure compliance. These include privacy (Jaeger, Lin & Grimes, 2008).
An analysis of cloud computing infrastructure evidently lays demands in meeting some of the basic security requirements. These security requirements are characterized by dependability where a software product provides security against malicious attacks, trustworthiness in which software provides logical protection against malicious attacks, and confidentiality where the software provides protection in the areas of intellectual property rights, encryption, covert channels, traffic analysis, and inference. In addition to that, cloud computing should meet standards for ensuring that data communicated through different mediums should be characterized by the three principles of data integrity. These include security against unauthorized modification and internal and external consistency of data. Cloud computing resources should provide appropriate reliable and timely access to data and guarantee system functionality (Dunlap, King, Cinar, Basrai & Chen, 2002).
This system security should be at the level of security service provided by cloud software. These include authentication, authorization, auditing, and accountability. Authentication ensures the integrity and identity of the user, authorizations focuses on user access privileges, and auditing evaluates system security issues and intrusion detections. This security demands and paradigm discussed above can best be illustrated on a monolithic architecture of an identity and access management framework illustrated below.
Other security concerns include spoofing, a technique where an intruder uses a technique to convince the system that its communicating with a genuine and trusted party to validate a communication, back-door where dial up modems to gain access into a network without going through authorized control mechanisms and hijacking to ensure attackers or intruders do not hijack sessions between trusted communicating parties. Other security concerns include dumpster driving, social engineering, TCP hijacking, man-in-the-middle, and replay (Joshi, King, Dunlap, & Chen, 2005).
Joshi, King, Dunlap, and Chen (2005) argue that cloud computing is an area of technology that is experiencing exponential growth inspired by the low cost associated with the technology. Thus, the cost benefit has had an impact on individual businesses, start-ups, and largely, enterprise business. Individual businesses are attracted to the technology with the expectations of low prices that are paid for the service offered. Service provisions include accountancy services, online banking, advertisements, and office assistants among a host of other services. On the other hand startups may be wooed into this technology given the high costs of starting a new IT department in a firm. The main challenge is scalability as transaction volumes increase. This relies on cross platform interoperability. Excess capacity is handled in its own way. Peak demands are addressed by invoking a pay as you go concept. However, peak capacities in cloud computing are identified as an advantage as it spans more users bringing them into its fold. Firms such as Amazon target high seasons to use their powerful cloud computing capabilities to access more customers based on their e-commerce web operation (Seshadri, Luk, Qu & Perrig, 2007).
Noteworthy are open source software. This have a role and play in cloud computing but attract different perceptions by different users. However, open source software comes with a host of other benefits. Among them is eases of access of software code, ease of adoption, no vendor lock, manageable and modifiable to suit the user, and low or no barrier at all to new users in trying the software (Payne, Carbone, Sharif, & Lares, 2008).
Payne, Carbone, Sharif, and Lares (2008) argue on the other hand that, large enterprises have thrust themselves into cloud computing due to the benefits realized from services offered on the cloud. These institutions use cooperate applications such as cloud applications in critical business functions in the storage of sensitive organizational and individual data. The impact of cloud computing on the large organizations is best illustrated on the diagram below.
From the above diagram, it is clear that control application servers, virtual machines, storage, and network infrastructure on premise are linked to the on premise host while showing the relations between other sections. That is in addition to security collaborations based on the architecture of cloud computing as illustrated below.
From cloud security and privacy
Large and middle owned organizations have realized the benefits that come with cloud computing powers. This is despite the security concerns involved with cloud computing. Large organizations such as the Amazon develop and use cloud computing in their e-commerce activities having realized the benefits accruing from its implementation and use. Since cloud computing is a new computing model, there are concerns about how security can be enforced and maintained at network level, host, data and information levels, and the application level. In addition to that, the adequacy of privacy enforcements by this computing model has been thrown into question. Privacy is a sensitive issue and the concept of cloud computing does not provide adequate description of satisfactory approaches of enforcing privacy on sensitive data.
Cloud computing is an amalgamation of technologies that has experienced an exponential growth in the recent past. It is an integration of grid computing and utility computing that is modeled on private, hybrid, community, and public clouds. The architectural model of cloud computing provides services modeled into cloud platform as a service (PaaS), cloud software as a service (SaaS), and cloud infrastructure as services. It endeavors to provide and enforce security at user and customer levels based on standards that are not clear cut. However, the concept provides such computing abilities in the e-market front and other enterprises to attract a large number of vendors (Lamb, 2009; Michael & Fox, 2009).
It is therefore important for universal standards to measure security enforcements and capabilities of the cloud software in enforcing confidentiality, authenticity, reliability, and privacy as security measures. These requirements should also be developed and enforced for cloud computing service providers as a standard requirement.
While a clear cut definition of cloud computing is not provided, the technology provides a powerful computing model that has experienced exponential growth in privates and public enterprises. Measured services, resource pooling, location independence, exponential elasticity are issues which characterize the technology which is a on-demand self-service, and ubiquitous network access. The services are modeled into cloud platform as a service (PaaS), cloud software as a service (SaaS), and cloud infrastructure as services. These services define the architecture of cloud computing. Cloud computing is modeled on private, hybrid, community, and public clouds. To enforce data integrity, confidentiality, and other security measures, organizations need to come together and device standards against which security measures have to be evaluated (Payne, Carbone & Lee, 2007). A public cloud infrastructure is a cloud-computing model that provides infrastructure and services to the public and organizations take ownership of the public cloud. On the other hand, the hybrid cloud is an integration of private and public cloud infrastructure. Typically, the hybrid cloud accumulates the benefits of both the public cloud and the private cloud.
Why Companies are moving towards Virtualization computing
Research has shown that virtualization provides a platform upon which organizations such as Google.com, Amazon.com offer services based on cloud-computing technologies with the number of new entrants growing by the day to fulfill their business objectives. However, these technologies come with a myriad of security issues though many companies are shifting towards the virtual cloud and discarding their old computing models. A number of factors attracting organizations into the mentioned computing models include the cost effectiveness of conducting computing services from the cloud without incurring the cost of setting up IT infrastructure. In addition to that, many organizations find the provision of services to be web based thus moving many of the resource requirements to the virtual computing environment.
Typically, contemporary approaches to software and hardware resource usage has been identified to be a costlier and inefficient approach. In addition to that, the old architectural approach of organizing hardware and software layers adds to the inefficiency of old systems. Thus, a better way to address organizational computing needs in an efficient and cost effective manner has been to leverage organizations in adapting to the cloud computing environment (Lorincz, Redwine,& Sheh, 2003).
The five fundamental characteristics of cloud computing leveraged by the benefits discussed above have significantly contributed to the movement of organizations towards the cloud. The five characteristics include ubiquitous network access, high degree of elasticity, location independence, measured services, resource pooling, and Ubiquitous network access (Krutz & Vines, 2010). In addition to that, cloud computing can be modeled after the private cloud model, public cloud, hybrid cloud, and community cloud to serve specific needs of organizations. On the other hand, organizations owning the cloud can lease their services to different users on demand. However, it is possible either for the clouds to be owned privately or by the public (Krutz & Vines, 2010).
The value proposition motivating organizations to move towards virtualization include scalability. Scalability allows IT infrastructure to meet rising demand and performance needs of a business. Krutz and Vines (2010) observe that when computing needs to an organization exceed the capacity of its computing resources, managers find a virtualized computing environment as the best solution to fulfill additional computing needs. That implies that a cloud-computing environment can be virtualized dynamically to allow for high levels of redundancy to ensure reliability and high levels of availability (Krutz & Vines, 2010).
Organizations eye the mutual benefits of customers and suppliers in sharing data and applications without the need to focus on the computing infrastructure as an improved business process (Krutz & Vines, 2010).
The theoretical support will provide the link between virtualization, cloud computing, and the security issues related to the technologies. In addition, the framework will show a strong link between the technologies and concrete reasons that have made companies shift to the new computing platforms. Thus, the need to understand the underlying technologies, security risks, and threats as discussed below will form the baseline for further academic and commercial research on the benefits of shifting to the computing technologies.
Cloud computing and virtualization are two different approaches to computing. However, cloud computing and virtualizations are complimentary. Cloud computing is an integration of grid computing and utility computing that is modeled on private, hybrid, community, and public clouds. The architectural model of cloud computing provides services modeled into cloud platform as a service (PaaS), cloud software as a service (SaaS), and cloud infrastructure as services. On the other hand, virtualization provides a platform upon which cloud computing provides services to end users.
Typically, virtualization is viewed as a single computing environment able to run different applications concurrently while cloud computing spans services on multiple computing locations. Virtualization provides scalability and flexibility in dynamic allocation of resources based on demand. In addition to that, it is possible to create templates to create similar or identical servers in a virtual environment. Research has shown that servers in a virtual environment have the flexibility of being migrated across different platforms without disrupting users and other tasks during the migration period.
Other findings indicate that virtual serves can be migrated to new hosts even when a host is lost. Thus, virtualization embraces the concept of incremental growth by allowing for maintenance without disrupting current users. In addition to that, high availability is a benefit to organizations that embrace the virtualization concept. Other benefits include flexibility and ease of deployment, high levels of redundancies, flexibility in the pooling of resources, and high level of resource optimization.
On the other hand, the research has shown that different companies have embraced the virtualization concept. These include Microsoft, VMware, and several other organizations. It is also important to note that virtualization is supported on different technologies, key benign the virtual machine.
Further findings indicate that virtualization demands security implementations typically defined by data and code executions in a virtual environment. These include accidental modification of data and programs and by either resident programs or hostile programs. A typical example of the relationship between virtualization and cloud computing is best demonstrated in fig 1 below.
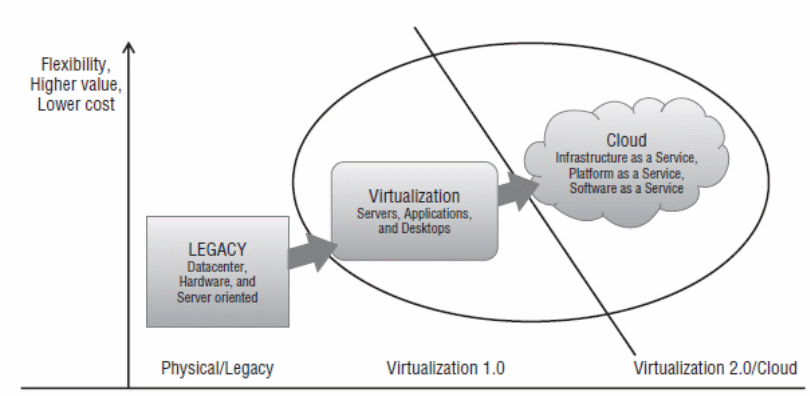
On the other hand, cloud computing, from the above literature, takes virtualization to the next level in computing. Typically, that has led organizations to adapt to the cloud to reap the benefits that come with cloud computing.
Findings on cloud computing benefits include the ability to interlink distant components into a single whole to offer services to different users is one of the benefits of cloud computing. Organizations are saved from the upfront capital investments that require large capital investments to purchase hardware, software, routers, and other hardware requirements to set up a cloud-computing infrastructure. In addition to that, cloud computing provides a platform for the efficient utilization of resources, and acts as a just-in-time infrastructure for the computing needs of organizations. However, a number of security issues need to be addressed by organizations that take their computing tasks to the cloud. These include confidentiality, while virtualization-related security issue includes data integrity. Thus, confidentiality in a cloud-computing environment regards encapsulation and protection of data from unauthorized disclosure of information. Different mechanisms used to implement confidentiality in a cloud include data encryption services, authentication services through the network, and security protocols implemented at the network level. Thus, the virtual environment should afford the security issues reflected in the cloud.
Another security issue includes integrity. Integrity requires that data is not intentionally or unintentionally modified while on transmission will be researched. Intentional or unintentional attacks can cause the loss of data integrity. In the cloud-computing environment, organizations maintain data integrity through different mechanisms, which include use of firewalls, intrusion detection mechanisms and several other techniques to manage system security.
Security implementation strategies inspire a level of confidence in the user of the cloud. Among the strategies, for maintaining confidence worth noting are data encryption and segmentation techniques that typically provide secure data storage services in the cloud. It is the obligation of the service provider to use well designed and reliable encryption techniques based on algorithms that are not easy to decrypt to ensure a secure cloud computing environment. However, there is the need to improve continuously data recovery techniques to stay abreast with current and new emerging computing technologies.
Significance of the Study
The study will contribute significantly to the current body of knowledge in the academic commercial world on the two concepts of virtualization and cloud computing, the relationship between the technologies, and establish concrete reasons that are driving organizations towards the technologies by moving away from the traditional computing approaches despite the security threats and issues associated with the technologies. Virtualization and cloud computing make data storage and other computing services efficiently achievable. Businesses and organizations which are using virtualization and cloud computing are making huge saves and increasing operating efficiently. It is therefore of significance that virtualization and cloud computer clouding are well understood in order to maximally utilize their benefits while minimizing the risks which might be associated with the technology.
Research design and Methodology
The baseline of the study will be qualitative and desk based literature review. The study will take a tripartite approach by focusing on virtualization, cloud computing, and concrete reasons for the shift by companies into the new technologies despite the security threats and risks associated with the computing approach. A qualitative research has its baseline on social sciences that will endeavor to provide the answer to the inquiry on the reasons compelling companies to move towards virtualization and cloud computing despite the security risks and threats inherent in such technologies. According to Miles and Huberman (1994), a qualitative research will provide answers and valuable information on the shift to the new technologies, and might be used to provide some answers on quantitative information such as the number of companies providing computing services on the new technologies. On the other hand, Rutman (1996) views a qualitative research as a complimentary tool in conducting a desk based review of literature to provide in depth information on the current study under investigations. One approach used in the study as a prelude to the research is establishing theoretical support for the basis for academic comprehension of the foundations of virtualization and cloud computing technologies from which companies draw for practical implementation in the computing industry, as discussed in the preceding sections. Several academic and online sources will provide the basis for the literature review to inform the study on the focus of the study.
Organization of the study
The study will be organized along the inquiries based desk based literature, the internet, different journals and researchers who have conducted research on virtualization, cloud computing, the relationship between the technologies, and reasons why organizations are moving towards the cloud. In addition, books will form additional sources of knowledge in the study.
The organizational structure will be as follows: Chapter one will introduce the research proposal and give an introductory outline of what will be covered in the actual study. Among the issue covered in this chapter include context of the problem, a description of the problem statement, the hypothesis, the research question and research sub-questions, limitations of the study, the delimitations and the assumptions upon which the study will be based. Chapters two and three will examine literature in regard to information about virtualization and cloud computing respectively. The study will also give information about the significance of the study, and research design and methodology.
Conclusion
The research will focus on cloud computing and virtualization as complimentary technologies and the rationale for companies moving towards the new computing platforms to enable upcoming organizations understand the rationale for the shift in technologies. Typically, Virtualization and cloud computing are new technologies that provide a platform for the provision of computing services on demand. Virtualization provides a platform to run different applications on the underlying hardware platform by running multiple operating systems on a single physical machine. In addition to that, Virtualization provides a platform consisting of hardware, software, and other applications upon which cloud computing provides services on demand. On the other hand, cloud computing takes virtualization to the next level in computing and provide scalability of the virtualization platforms based on demand for the services offered on the cloud. Cloud computing and virtualization run on hostile environments and the need to enhance security due to the hostility of the executing environment is important. Different firms of security threats affect users of the cloud such as unauthorized access to data, confidentiality, integrity, and availability. Thus, companies, academic institutions, and upcoming organizations will find a strong rationale for adopting cloud computing and virtualization technologies in offering computing services despite the security threats and risks inherent in the technologies.
References
Adams, J. (2011). SPEND NOW TO SAVE LATER?. Bank Technology News, 24(1), 19-21.
Arnfield, R. (2010). How secure is your green IT?. Computer Weekly, 16.
Claybrook, B. (2010). THE Bumpy Road TO PRIVATE CLOUDS. (Cover story). Computerworld, 44(24), 18-23.
Dunlap, G. W., King, S.T., Cinar, S., Basrai, M. A., & Chen, P. M. (2002). Revirt, Enabling Intrusion Analysis through Virtual-Machine Logging and Replay. SIGOPS Operating Systems, Rev., 36(SI), 211–24.
Jaeger, P. T., Lin, J., & Grimes, J. (2008). Cloud computing and information policy: Computing in a policy cloud? Journal of Information Technology & Politics, 5(3), 269-283.
Jain, S. (2007). Microsoft Virtual PC 2007 Technical Reference. Web.
Joshi, A., King, S.T., Dunlap, G. W., & Chen, P.M. (2005).Detecting Past and Present Intrusions through Vulnerability-Specific Predicates, in SOSP’05: Proceedings of the Twentieth ACM Symposium on Operating Systems Principles, pp. 91–104, New York: ACM.
Kroeker, K. L. (2009). The Evolution of Virtualization. Communications Of The ACM, 52(3), 18-20.
Krutz, R. L., & Vines, R.D. (2010). Cloud Security. A comprehensive Guide to Secure Cloud Computing. New York: Wiley Publishing, Inc.
Lamb, J.P. (2009). The Greening of IT: How Companies Can Make a Difference for the Environment. New York: IBM press.
Lorincz, K., Redwine, K., & Sheh, A. (2003).Stacking Virtual Machines – VMware and VirtualPC. Web.
McCann, D. (2010). YOUR CLOUD OR MINE?. Cfo, 26(6), 31.
Michael, A., & Fox, A. (2009). Above the Clouds: A Berkley View of Cloud Computing.
Miles, M. B. & Huberman, A. M. (1994). An Expanded Sourcebook Qualitative Data Analysis –2nd Edition.
North Carolina State University. (2010). New research offers security for virtualization, cloud computing. ScienceDaily. Web.
Overcoming Cloud Computing’s Biggest Challenge: Virtual Network Security; Stonesoft shares five network tactics to help resolve cloud security issues. (2010). M2PressWIRE,
Payne, B. D., Carbone, M., & Lee, W. (2007).Secure and Flexible Monitoring of Virtual Machines. Computer Security Applications Conference, Annual, 0:38597.
Payne, B. D., Carbone, M., Sharif, M., & Lares, W. L. (2008).An Architecture for Secure Active Monitoring Using Virtualization, IEEE Symposium on Security and Privacy. 233–47.
Redhat. (2007). Virtualization Guide: Red Hat Virtualization. Web.
Rutman, D. (1996). Caregiving as women’s work: women’s experiences of powerfulness and powerlessness as caregivers. Qualitative Health Research 6 (1): 90-111.
Scheffy, C. (2007). Virtualization for Dummies. Web.
Seshadri, A., Luk, M., Qu, N., & Perrig, A. (2007).SecVisor: A Tiny Hypervisor to Provide Lifetime Kernel Code Integrity for Commodity Os’s, in SOSP 07: Proceedings of the Twenty-First ACM SIGOPS Symposium on Operating Systems Principles, pp. 335–50, New York: ACM.
Steinert-Threlkeld, T. (2009). The Key Phases of Virtualization. Securities Industry News, 21(13), 14-15.
Thurman, M. (2009). Parting the Clouds at The RSA Conference. Computerworld, 43(18), 25.
Varia, J. (2008). Cloud Architectures. Web.
Virtualization Overview. (2006). White Paper. Web.
VODACOM/NOVELL PARTNER TO SECURELY MANAGE CLOUD SERVICES. (2010). UNIX Update, 21(6), 4-7.
Waxer, C. (2009). Go VIRTUAL OR CLOUD?. Computerworld, 43(24), 27-28.
Wilde, N., & Huber, T.(n.d). Virtualization and Cloud Computing. New York: Wiley Publishing.
Wyse, T. (2). Wyse CEO Discusses Latest Trends in Cloud Computing, Mobility and Virtualization at Cloud Forum 2011 in Tokyo. Business Wire (English).
