Introduction
Wi-Fi is an acronym for Wireless fidelity though this is just an unofficial use. This is a technology which was built on a standard known as the IEEE 802.11. The standard is tested and maintained for compatibility with systems by the Wi-Fi alliance which came up in 1999. For a company to get certified with the use of this standard, it must have fulfilled the radio, security and the authentication standards (Basili & Rombach, 2007). This standard was first used commercially in the year 1999, in the month of august. The term can be said to have been coined from the radio standard high fidelity (Hi-Fi) which has been in the market since the early 1030s (Tang et al, 2010).
Benefits
There are quite some remarkable benefits of using Wi-Fi as compared to the use of a wired network. In applications which are embedded, there is the upper hand of a great deal flexibility (Tang et al, 2010). In this case the management of a certain network is able to enjoy better monitoring of their systems, controlling and disseminating information. Due to these flexibilities, access to remote locations is enhanced thereby reducing the costs of operation.
Some of the most conspicuous benefits of the technology include: –
- Wireless Ethernet: Wi-Fi, like Ethernet are 802 standard networks thus they share the same backbone of elements. This therefore means that Wi-Fi is a replacement of the Ethernet.
- Extension of access: due to the absence of use of normal cables and wires for connection, this standard therefore increases connectivity to places which would otherwise be too expensive to reach or else inaccessible through cabling (Tang et al, 2010).
- Reduction of costs: the reduced cost is the money that would have otherwise been used to buy cables and lay them down. Amongst the supporting factors for this are cheap wireless routers, no trenching, and all other physical connections.
- Mobility: someone who is using a wireless connection can always move unlike wire connected individuals
- Flexibility: due to extension of access, reduction of costs and the mobile effect, there is more room for other applications and also room for creativity in newer applications.
Wi-Fi and embedded systems
From the above discussion, it is evident that the use of wireless networks has escalated in use mostly top embedded systems. According to some research which has been done, most of the internet devices will be non computer based but will be basically embedded systems. The embedded systems come with interfaces which operate on the basis of Wi-Fi interfacing as follows: –
- Industries and control systems where cabling and wiring can be very expensive or cumbersome. Such industries are those with machines that move continuously
- In emergency situations which are always in transit such as in the army while in combat
- Mobile systems like the one in assets
- Surveillance materials which need to be concealed in all aspects. It is not possible with cables
- Manufacturing, medical and educative areas.
Wi-Fi and security
Security is a critical question in almost all computer systems and it comes with a vast amount of concern. In security, devices should be able to know the nodes that they are communicating to and also the people or other systems that are sourcing information from as this might lead to corruption, distortion or use in ways that are malicious (Basili & Rombach, 2007). In Wi-Fi security has an extra hurdle considering that cabling has a bit of assurance in the one trunk sending and receiving of data packets. In Wi-Fi, the fact that the information is just on the air means that it is possible to interrupt by people, read or even distorted.
Security strategies
For a successful and secure wireless network, some objectives need to be considered; data integrity, mutual authentication and private communication.
- Mutual authentication: – this is a procedure that is used to verify the identity of the client and that of the access point. This is essential in that these two sides have the ability to cause insecurity. The access point secures all network connections which gives access to resources in any computer. The essence of the access point being identified in the network is to inhibit other fake access points from having access to security information like login details which then bring forth denial of service.
- Privacy of information: Security in computer networks is about what can be solved through algorithms for encryption and use of dynamic keys like the RSA (Stapko, 2007).
- Data integrity: this enhances that data gets to its destination exactly the same way that it was sent.
There are many protocols which can be put in place to avert the dangers mentioned by the above goals. Some of the known strategies of security in Wi-Fi include WEP, WPA and WPA2.
Wired Equivalency Privacy (WEP)
This strategy was introduced by IEEE 802.11 standard. This mode was established with the initial instructions of providing the same security as in the normal wired local area networks. There was no much provision of security from this method due to the vulnerability that it posed. This makes it have a lot of disadvantages.
To begin with, mutual authentication is at times unable to secure the PC from sniffing access points. At the same time the devices communicating have static keys for the WEP security which ensures that there is no security at the level of the user. This makes any users who access the device retrieve the information. This static key is always used in both encrypting the information and also in authenticating thus possibly exposing the information.
Authentication in Wi-Fi
This happens in basically two ways; open key and shared key modes. In open key, the client joins an ad hoc network without being asked a question thus no authenticity. In shared key, the two communicating sides have a certain secret key which has to be shared before access to the network is allowed.
Encryption in WEP
For encryption, a static key is used with pre-configuration done to the access points and also to the clients. This happens to minimize sniffing of the packets holding the key considering that it remains at a solemn point. It is however worth to be noted that the key can be intruded easily (Ross, 2008).
Data integrity in WEP
This is based on a CRC 32 algorithm where a check value is used to provide integrity. This algorithm is used in most cases to detect flaws in packet transmission thus resulting in avoidance of errors. This has the disadvantage that the wireless network can be interfered with without prior knowledge of the WEP.
Disadvantages of WEP
From the above discussions, it is evident that WEP has quite some serious flaws. Some of them are lack of mutual authenticity, encryption and authentication using the same key, encryption keys can be cracked, and checksum values do not offer adequate integrity of data and the lack of dynamism in key generation.
IEEE 8.11i
“Wi-Fi Protected Access” is a release of the Wi-Fi alliance in a bid to improve on WEP. It consists of both WPA and WPA2 which only differ in the methods of confidentiality and the integrity of data (Ross, 2008).
Both WPA and WPA adhere to the IEEE 802.11 standards. In IEEE 802.11i there are personal operation mode and enterprise operation modes which define how the Wi-Fi network behaves.
The enterprise authentication mode requires the availability of more memory for it to be effectual as required.
Operation of WPA and WPA2
In personal mode, there is a compulsory application of the PSK “Pre-Shared Key”. The wireless node is authenticated only if it has comprehension of the key. This is possible through encryption and decryption on both the communication channels which is aided by the PSK. The generation of the PSK is through a passphrase which is a minimum of n8 ASCII characters and a maximum of 63 characters (Mukherjee, 2007). The passphrase should be composed using the normal password protection protocol like order of characters, words and so on (Gast, 2005).
In wireless network encryption using WPA there is a requirement for provision of the access point with a passphrase rather an encryption key which can be in character length or in binary bits. “Temporary Key Integration Protocol” helps the Wi-Fi clients to generate unique keys for encryption. This helps in the enhancement of security in that if one of the keys is sniffed, the entire communication is not endangered and that knowledge cannot be able to give access to the main key (Ross, 2008).
IEEE 802.1X
In this control mode, the access control to the, the network resources for Wi-Fi is controlled by a port. This is a layer 2 protocol where there is no assignment of the IP addresses thus ability to prevent invalid access to computing services.
802.1X architecture
This architecture is composed of the following components; the supplicant is the device that wants authentication for access to resources in a network, the authenticator is the device that needs proof of access to only those wireless devices that can prove their identity and the authentication server is the device that performs the role of granting permission (Mukherjee, 2008). The diagram below indicates the dependency between the three components.
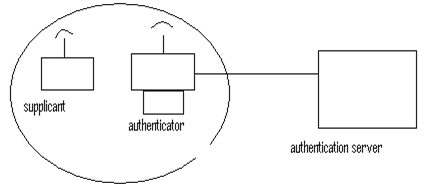
In most cases the supplicant is a wireless station which needs to join a network; the authenticator is an access point that passes the access communication from the supplicant towards the authenticating server. In this server, the authenticity of the supplicant is checked before permission is granted. If the results of the authentication are successful access is determined (Gast, 2005).
Public key cryptography mode of mutual authentication
For implementations which use EAP-TLS, they are conversant with the TLS 1.0 protocol. In this method the digital certificates are used to authenticate the clients and the servers in the network. This enhances that the identity with the public key is true. This is the key that can then be used for encryption. The recipient of the data packet is in hold of the private key which he can then use to decrypt the message. Other kinds of ensuring security in Wi-Fi networks is the enhancement of a mutual authenticity using user names and respective passwords which must be possessed by both the clients and the servers (Mukherjee, 2008).
Data integrity and encryption
The problems in WEP which affect the integrity of data have consequently been looked into when using WPA and WPA2. The method which is used for encryption is the same though there becomes a difference when it comes to decryption as it uses a PMK “Pairwise Master Key”. The material that is used to get the key can be found in two ways. The first way is using a static key that he is hidden using a secret that is shared whilst the other one is using a value that is derived dynamically. This value can also be gotten through the authentication of the EAP (Dawes, 2007).
TKIP
TKIP “Temporal Key Integrity Protocol” has to be used when implementing the solutions that will use WPA as the security standard. In WPA2, the use is not a must. This security protocol is very superior as compared to the other protocols despite the fact the protocol is based on RC4 which is the same standard which is in use for WEP a sub standard protocol. Despite the similarities, WEP has various disadvantages as compared to TKIP (Dawes, 2007).
- TKIP is 48 bits long whilst WEP is 24 bits, thus shorter,
- WEP uses pre shared keys which are static whilst the keys in TKIP are dynamic and derived each frame at a time,
- For WEP, there is no protection fro replay whilst in the latter mode, IV is the frame counter which is used to protect replay,
- WEP has the same key to authenticate as well as to encrypt, in TKIP, use pre shared keys which get the PTKs rather that using it for encryption in a direct manner,
- WEP’s algorithm for data integrity is not adequate whilst TKIP uses a special code known as MIC “Message Integrity Code” for the integrity of data.
Conclusion
This paper has critically reviewed the aspect of security as it applies to Wi-Fi systems. Standards have been discussed and different security options which are applied to protect data on transit in wireless communication have also been looked into. It is evident that the question of security is a critical issue that should be maintained to the highest standards.
References
Basili, H.D. & Rombach, (2007) ‘The TAME Project: Towards Improvement-Oriented Software Environments’, IEEE Transactions on Software Engineering, vol 14 P.758-773.
Dawes, B. (2007) “Analog in, digital out: Brendan Dawes on interaction design” Internet & Information Technology 3: 25-76.
Gast, S. (2005). 802.11 Wireless Networks, The Definitive Guide, 2nd ed. Cambridge: O’Reilly.
Mukherjee I. (2008) “Even the Dial-up Internet Users, temp. IP Address Owners Deserve an FQDN Address”, The Journal of American Science, 2(1).
Mukherjee I. (2007) “A practical approach to inexpensively link distributed facilities of New Horizon College of Engineering for Data Communication”. The Journal of American Science; 2(4):49-52.
Ross, J (2008). The Book of Wireless: A Painless Guide to Wi-Fi and Broadband Wireless, Second Edition. San Francisco, CA: No Starch Press.
Stapko, T. (2007). Practical Embedded Security. Cambridge: Elsevier Science & Technology.
Tang, S. et al (2010). WiMAX Security and Quality of Service: An End-to-End Pespective, New York: John Wiley and Sons.
Bibliography list
Back Track bootable wireless/security auditing. Web.
Fluhrer, Mantin, Shamir WEP Weakness. Web.
Kismet. Web.
Kuo, C et al, Low-cost Manufacturing, Usability, and Security: An Analysis of Bluetooth Simple Pairing and Wi-Fi Protected Setup. Web.
Linux WPA supplicant. Web.
Paramvir, B. et al, Enhancing the Security of Corporate Wi-Fi Networks Using DAIR. Web.
Potter, B. Wireless Hotspots: Petri Dish Of Wireless Security. Web.
Real 802.11 Security: Edney, Arbaugh. Web.
Salem, B. N. et al, Reputation based WiFi Deployment Protocols and Security Analysis. Web.
Sweetser, Frank. Introduction to Wi-fi Security, WPI network operations and security Protocols and Security. Web.
Gast, Matthew S. (2005). 802.11 Wireless Networks, The Definitive Guide, 2nd ed. Cambridge:O’Reilly.
