Introduction
The paper presents a plan for the creation of a state-of-the-art airport security system. The plan is created for a primary commercial service airport, that is, a publicly owned airport with more than 10,000 passenger boardings per year (that is, revenue boardings that can be scheduled service or not) that also receives scheduled passenger service or enplanements (FAA, 2015). This is the category of airports with the maximum number of passenger boardings, which makes it particularly important to ensure its security. The main topics that will be discussed include the security force, the layout and its significance for security, the passenger screening, and the integration of all the layers of security. The security management of freight air carriers will also be discussed briefly. According to FAA (2015), this kind of carriers offer the service of air transportation for cargo; to receive the title of cargo service airports, the total annual weight of the cargo landed must exceed 100 million pounds.
The airport, the security system of which is being planned, is supposed to be situated in the US, which defines a number of specific requirements and sets a particular background to security management.
Airport Security: Key Factors
Threats
The threats that airport security systems try to eliminate are numerous. It is well-known that in the US, the true recognition of these threats started to develop after the events of 9/11; as new terrorist attacks took place, the understanding of security also improved (Elias, 2010; Alards-Tomalin et al., 2014; Stewart & Mueller, 2014). Indeed, terrorism is among the major threats that airports have to foresee and prevent, and the tragedies of 9/11 or Moscow’s Domodedovo airport demonstrate the significance of these efforts worldwide (Stewart & Mueller, 2014). Apart from that, criminal activity is of vast concern for airports. The main targets in an airport include the aviation infrastructure, aircraft, and “hostile exploitation of air cargo” (Elias, 2010, p. 104). The latter threat refers, for example, to smuggling and theft; the terrorist strategies typically include bombing and shooting, biological or chemical attacks as well as hijacking. The threat to aviation infrastructure includes the direct threat to airports (for example, the destruction of infrastructure as a result of bombing). Still, it is obvious that airport security is aimed at mitigating the rest of the threats as well as the direct ones.
The major challenges of airport security consist in making it cost-efficient and ensuring the customer satisfaction along with their safety (Stewart & Mueller, 2014; Lenot, 2015).
Costs
The issues of the costs of airport security have been raised, for example, by Stewart and Mueller (2014) who demonstrate that the modern airports can be deemed “too safe” indeed. In fact, the authors appear to question the attractivity of airports for terrorism, pointing out that there are busier areas in the cities. Still, given the current geopolitical situation, the threat of ISIS and its imitators, it seems that the safety of the population is of primary importance (Yourish, Watkins, & Giratikanon, 2015). It should be pointed out that government institutions like Federal Aviation Administration (FAA) and Transportation Security Administration (TSA) provide funding and grants for technological development of airports, including commercial ones (Elias, 2010, p. 275). In other words, the government appears to imply that security in the sector must be maintained and is ready to allocate resources for this purpose.
Even though cost-efficiency is, obviously, a matter to be concerned with, as a best-case scenario, this plan is guided by the supposition that all the necessary budget is provided.
US airport security
The US airport security policies and strategies are connected to the Aviation and Transportation Security Act (Public Law [PL] 107-71) that was enacted following the 9/11 tragedy in November 2001 (Elias, 2010, p. 99). PL 107-71 (2001) entitled the newly created Transportation Security Administration to create the strategies for the establishment and maintenance of security in the sector. The publicly available plans have been developed by the Department of Homeland Security in such a way that they were complimenting the National Infrastructure Protection Plan. The result, the National Strategy for Aviation Security, along with a number of supporting plans, was released on March 26, 2007 (Elias, 2010, pp. 99-102).
The framework that is used for the US airport security is that of risk management: it defines risk as a function of threat, vulnerability, and consequences. It is not denied that the risks cannot be completely eliminated, so the goals of the US strategy for aviation security is aimed at deterring as many threats as possible and minimizing the difficulties that security measures could cause for passengers (or cargo transportation) (Elias, 2010). The key actions that are presupposed by the strategy include the maximization of security awareness and promotion of international cooperation as well as the implementation of layered security and the maintenance of the continuity of the processes in the sector (Elias, 2010, p. 110). For a single airport, the latter two actions are of primary importance.
Security Force
The security force ensures the smooth implementation of major layers of an airport’s security and contributes greatly to the attempts of making the security processes as convenient as they can be (Elias, 2010).According to Elias (2010), airport security tends to involve state and local law enforcement. It is not uncommon for airports to introduce specific policies concerning the security force depending on the specific needs of an airport; for example, Houston George H.W. Bush Intercontinental Airport employs horse riders for the perimeter patrols as a result of the specifics of the landscape (it is heavily wooded). As a general case, though, this plan presupposes the involvement of local law enforcement as the means of providing trained and qualified security force with an appropriate background (Elias, 2010). SWAT training for airport police has been suggested, but it is also demonstrated that the increase in security level, in this case, can be described as minor and, according to Stewart and Mueller (2014), not cost-effective, which is why it will be considered excessive for this case. The law enforcement employees will form the bulk of the airport’s security force and will be providing security support in the airport’s terminal and other facilities and responding to suspicious incidents, behaviors, and threats. Apart from that, they will be involved in perimeter patrolling, checkpoint screening and other relevant activities. It is also noteworthy that, trained bomb-sniffing dogs (explosives detection canine teams) with handlers have been used in airports for more than 40 years, which demonstrates their efficiency (Elias, 2010, p. 289). Therefore, the airport will want to employ this kind of security force as well.
TSA personnel is capable of providing trained personnel that carries out baggage screening operations and oversees cargo screening; apart from that, the Administration can provide the trainers who teach the already employed law enforcement members or other employees the specifics of the modern equipment (Hoggan, 2012, Elias, 2010). Indeed, airport security technologies are being improved continuously, and, as a result, continuous training is required for the employees who operate it. This is a major aspect of security force training that cannot be overlooked (Hoggan, 2012). In other respects, the training of the employees and their organization is going to be defined by the responsible department.
It should be also pointed out that the flying crew is also expected to be trained to react to a case of emergency in an appropriate way; all-cargo pilots can be armed to be able to protect the planes. Similarly, airports strife to increase security awareness for all the employees to improve the safety of themselves and the customers (Elias, 2010). Still, these employees are not the security force per se, even though they can contribute to the security of the airport and should be encouraged to do so.
Airport Lay-Out
The lay-out of an airport needs to ensure the safety; at the same time, it is supposed to be convenient and needs to improve the passenger flow or at least not hinder it. The airport perimeter will include the passenger terminal (that consists of the “nonsterile area” before the checkpoint and the sterile one after it), the departures area (it includes gates, services, retail); the air operations area (where all the flight operations take place; includes runways, taxiways, and so on); the cargo operations area; the aircraft parking as well as the car parking (Elias, 2010; Lenot, 2015). The nonsterile zone of the terminal needs to be connected to the lane to ensure convenient entry to the airport; the sterile area needs to provide convenient access to the departures area. The cargo operations area needs convenient access to air operations area; the car parking should be detached from the complex that is described above for security reasons (Lenot, 2015).
Layout and Threats
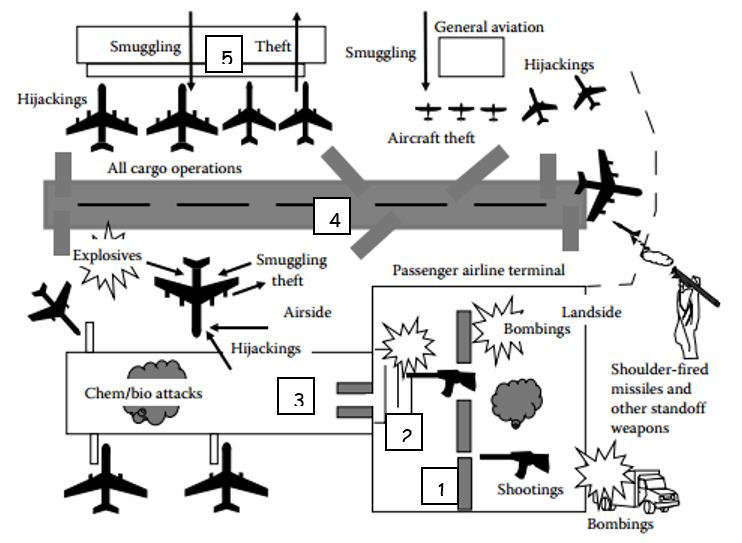
According to Lenot (2015) and Elias (2010), different airport areas are typically subjected to different threats. Indeed, the chemical and biochemical attacks are more likely to occur in the terminal area; the nonsterile area is more likely to be subject to shooting and bombing as the checkpoint is aimed at preventing the possibility of bringing weapons to the sterile area. The nonsterile area is also vulnerable to car bombs that can crush into the terminal as it had happened, for example, during Glasgow airport attack (Stewart & Mueller, 2014). The obvious danger for the perimeter, except for trespassing, is standoff weapons, for example, shoulder-fired missiles as suggested by Elias (2010). Figure 1 represents the said threats as demonstrated by Elias (2010) in the book “Airport and aviation security.”
Layout and Security
As a result of the various attack possibilities, airport security is multi-layered. The layout of an airport is directly connected to its security, which, in turn, is in many ways dependent on the access control, law enforcement, and surveillance, although other methods of protection are also used.
The perimeter is protected with the help of intrusion protection technologies, which includes fences and various sensors (Lenot, 2015). Law enforcement presence is another significant aspect of perimeter protection. The most popular and modern choice of perimeter surveillance is thermal imaging cameras. Their advantages include long range, reliability, and high performance. They can be used in combination with short-range infrared cameras that are installed directly on the fence (Elias, 2010).
The parking is protected through surveillance, access control, and automatic license plate recognition: all these measures also allow smooth operation of the sector through the improvement of traffic flow as the information about the parking is always updated. Access control, in fact, works throughout the airport and presupposes limited access to critical areas. It is enabled through the identification and validation of employees credentials. The Security Identification Display Areas, as demanded by TSA, presuppose continuous checking of employees security identification (Elias, 2010).
Ground surveillance radar is used to track the movements of aircraft and other vehicles throughout the airport. GPS tracking of vehicles is used for the same purpose. This kind of surveillance provides the information about the traffic that is necessary for operators and enables them prevent collisions and notice suspicious behavior (Elias, 2010).
The lane that is closest to the terminal needs to be designed to stay as far away from the terminal as possible and convenient to minimize the possible effects of a car bomb going off (Stewart & Mueller, 2014). Obviously, the car bomb can also be crushed into the terminal, and the detachment of the lane does not ensure absolute protection. In this case, the usage of specific materials, including, for example, shatterproof glass tends to improve the safety of terminals due to the fact that glass shards are of extreme danger for busy areas of an airport, and the terminal can be described as such (Stewart & Mueller, 2014).
To sum up, by implementing a consistent security system, the airport will be able to ensure the safety of its customers with the help of state-of-the-art technology used within every area that is included in the airport’s perimeter. To deal with the enormous influx of the information, computer vision algorithms are used to improve the information flow and avoid human factor mistakes (Elias, 2010).
Screening Passengers System
Passenger screening is another level of airport security that is achieved with the help of multi-layer measures. Passenger screening process is supposed to consist of the following layers. The reservation process is the first layer (protected with the help of no-fly lists as well as other profiling databases that allow defining the high- and low-risk customers) while the airport security is the second one (it is ensured with the help of closed-circuit TV as well as sniffing dogs, law enforcement officers, Computer Assisted Passenger Pre-screening Systems and other similar technologies). The security checkpoint can and tends to be regarded as another layer of security due to the numerous screening processes that it includes: the checking of the identity as well as the boarding pass, the metal detector, baggage screening (both carry-on and checked), secondary screening. Finally, the layer of airplane security includes the federal flight deck officers, cockpit doors that are hardened as well as the flight crew that is trained to respond to the cases of emergency (Elias, 2010, p. 110). The specific pieces of equipment that are supposed to be used by the airport for different layers of passenger screening are listed and described below.
Technology and Passenger Screening
Nowadays, TSA demonstrates the way modern technology can be used to ensure security throughout multi-layered passenger screening. The described equipment is used by the Administration’s employees at the airports where they operate; the advantages of this equipment are enough of incentive to use it for this plan (Hoggan, 2012).
Pre-Screening
The Secure Flight system is used before the passenger arrives at the airport: it determines the trustworthiness of a passenger with the help of trusted customers lists (TSA, 2015). The system collects a minimum amount of information for the sake of privacy protection, and, naturally, ensures that it is handled appropriately.
Checkpoint: The Passenger
The Credential Authentication Technology/Boarding Pass Scanning System is used to detect fraudulent or altered identity documents and facilitates the process of identity and boarding pass check through automatization. This relatively new technology ensures a higher level of security as it possesses a great ability of fraud identification that is achieved by enabling it to compare the features of the documents presented to a set the features “known” to the system.
Metal detectors and millimeter wave advanced imaging technology (AIT) as well as the pat-down method are used to screen passengers for metallic threats and (in the case of the two latter option) nonmetallic ones as well. It is claimed that the new technologies are safe for the people of any health condition, even pregnant women, but the pat-down screening can be regarded as a suitable option in case the technological alternatives are not trusted. Also, in case the detectors react to a person, he or she may be asked to undergo the procedure. To exclude the possibility of incidents, the procedure should be carried out in private with two officers present; the passenger can choose to be accompanied by another person (TSA, 2015).
AIT is a relatively new technology that deserves more detailed description. It is actively promoted by TSA as a harmless and efficient system that does not use X-ray. New AIT units are delivered with the necessary training that is typically provided by specifically certified instructors. Among the advantages of the AIT, the Automated Target Recognition functionality can be noted: it is an advanced capability of the system that obsoletes remote Image Operator, which improves the learning period for new operators. At the same time, the capability ensures a high level of detection along with improved anomalies displaying (Hoggan, 2012). For the time being, AIT is the state-of-the-art technology that should be used at the airport.
Automated Wait Time is a system that is used for the sake of improving the passenger flow: is enables operators to determine the traffic in queues and relocate resources if needed. This system also provides the information for the customers themselves (monitors). Apart from that, it decreases the length of queues: long queues can be considered an attractive target for terrorists (Stewart & Mueller, 2014). In such a way, both the safety and convenience of the customers is ensured.
Specific detection systems include explosive detection systems that have been improved recently by the explosive trace detection technology. The latter enables the security officers to swab luggage or passengers’ hands and place the swab inside a trace detection unit that analyzes it, defining the traces of explosives, if any. Naturally, sniffing dogs can be used for the same purpose. In fact, the usage of all the mentioned measures as a system is what provides high-level security at the airport.
It should be specified that all the checkpoint procedures have the potential of decreasing enplanement intentions of customers in case the said procedures are perceived as excessively complicated (Alards-Tomalin et al., 2014). Here, it may be worth mentioning that TSA (2015) has created a new, “lighter” form of passenger screening that, however, is only used for low-risk passengers. It requires less inconvenience (does not demand to remove shoes, belts, and taking certain items from the bag), but not every customer is eligible for such a procedure. At the same time, passengers tend to realize the importance of the mentioned procedures, and the increased security awareness of the customers may improve their perception of checkpoint security (Elias, 2010; Alards-Tomalin et al., 2014)
Luggage
Advanced X-ray Technology is used for carry-on luggage screening, and the upgrades of this technology are aimed at improving the detection capabilities (the version of 2012 was improved in the terms of explosive detection). Apart from that, it has been shown that the technology tends to improve the efficiency of the checkpoint screening and increases the speed of passenger flow.
Bottled liquid scanners are the technology capable of distinguishing between harmless and harmful liquids contained in passenger’s baggage. These scanners are also being improved with time to ensure advanced detection ability and an increased range of liquids that can be detected.
Checked baggage screening is typically technology-assisted, but a physical check may also be required, including a random check. In this case, a notice of inspection is placed inside of the bag (TSA, 2015).
To sum up, the plan presupposes the usage of the multi-layered, advanced-technology passenger screening that is typically used by US airports. As pointed out by Hoggan (2015), the mentioned pieces of equipment are constantly upgraded to ensure a higher level of protection; they also require trained personnel to operate the, which presupposes continuous additional expenses. The latter needs to be taken into account, but passenger screening is among the most significant aspects of airport security and it needs to be consistently thorough.
Passenger Screening Issues
It is also worth mentioning that the so-called “elevated risk screening” (pat-down, physical baggage checking ) significantly increases the inconvenience of the passengers. While a 2010 survey showed that about 70% of the US population recognizes the significance of these procedures and admits that they are important for the safety of the community, the perceived humiliation and intimidation has an adverse effect on the traveling experience as well as enplanement intention (Alards-Tomalin et al., 2014). The problem of perceived safety is that it is not very predictable; as the study by Alards-Tomalin et al. (2014) demonstrates, the correlation between the perceived professionalism of the personnel and the perceived safety during elevated risk screening is not always found. Therefore, the only reasonable way of dealing with the problem appears to be the improvement of the experience for the customers since it is, unfortunately, often inescapable. The measures that are suggested by TSA appear reasonable (for example, companionship for the pat-down procedure is bound to reduce some of the perceived intimidation); apart from that, it is important to ensure competence and commendable behavior of the personnel.
Systems Integration
The principle of multiple levels of protection, which has been mentioned in the plan several times, is connected to the idea of defense-in-depth that was initially used for nuclear industry. Nowadays other industries also hold it as a basis for the safety decisions, especially in case the threats are as significant as those of airport security (Bakolas &Saleh, 2011). To put it simply, this strategy presupposes creating multiple layers of security rather than a single one. The layered approach to security systems is expected to reduce the vulnerability to threats in the field (Elias, 2010, p. 110). This effect is achieved through the fact that the layers are, in fact, overlapping and constitute a consistent and continuous framework for security.
As it has been demonstrated above, the layers of airport security screening include at least two of them: the screening of the area and that of the passengers. Apart from that, the workers-related activities (workers screening, vetting, access control) can also be regarded as another layer of security (Elias, 2010). Finally, as suggested by Elias (2010), the passenger themselves may provide a level of security, which can be achieved through the improvement of security awareness among customers (110). It should be pointed out that all the layers are interrelated and would be much less effective if used separately.
At the same time, all the mentioned layers are multi-layered with numerous technology-assisted security measures that are used to achieve the desired level of safety. For example, the numerous screening technologies used to ensure the perimeter security compliment each other (short-range and long-range equipment that reacts to various sources of disturbance) to ensure an advanced level of safety. Here, a key part of the system integration is the computerized processing of the screening data that is used to assist operators, who could have been overwhelmed by the amount of information (Elias, 2010, p. 287).
At the same time, the screening is, again, a layer of security. It is run by and facilitated by the security force; but apart from that, the security force provides the next level of security: the response to the threats that is based on screening data. Naturally, the security system is mostly aimed at avoiding any kind of actual danger and preventing accidents, but this layer is of extreme importance.
To sum up, the suggested plan includes a complex, layered security system that includes state-of-the-art equipment, which is used for screening and preventing threats. Qualified personnel ensure the smoothness of security operations and are ready to respond to threats in case the latter are not prevented. The additional aim of security system consists in improving the experience to avoid creating negative enplanement intention among customers, which is especially important for a commercial airport. Still, it is important to point out that the said aim is additional, the primary one being the security.
Security Management of Freight Air Carrier
An air carrier is a “complex, multifaceted system responsible for moving a vast amount of freight, express packages, and mail” (Elias, 2010, p. 333). Air cargo shipment, in general, contributes significantly to cargo shipment as well as trade both in the US and around the world. In other words, it is an attractive target for crime, the risks including terrorism (bomb placement as well as hazardous materials smuggling) and cargo crime (theft, contraband, pirated goods distribution). Hijacking and sabotage are additional threats.
The security of a freight carrier naturally presupposes checking the cargo. Since the 9/11 events, more attention is paid to the physical check instead of relying solely on the screening of documents and records. At the same time, given the difficulty of the procedure, other measures are also relied upon, including first and foremost the profiling systems that allow defining low- and high-risk cargo. To facilitate cargo inspection, x-ray screening, explosive detection systems, chemical trace detection systems, and millimeter wave imaging systems are used (Elias, 2010, pp. 340-351). Most of these systems are costly and not particularly convenient (for example, EDS that can examine only the objects of very limited size), but they are improved continuously. Bomb-sniffing dogs are also often used to improve security. Cargo inspection is carried out by personnel of the airport, but TSA employees oversight these procedures. Finally, arming pilots and instructing them on the usage of the arms to protect the cargo and the craft from hijacking is another viable option for a freight carrier (Elias, 2010).
It should be pointed out that air cargo handlers are expected to undergo specific training that builds awareness and improves performance: this regulation was imposed by TSA in 2006 (Elias, 2010, pp. 357). Apart from that, it can be noted that since the beginning of the century, there has been a tendency of increasing the attention paid to cargo carriers; congressional appropriators have been increasing the funding allocated to cargo-related issues (Elias, 2010). It may be concluded that the significance of air cargo security has been recognized, and freight carriers are expected to correspond to the current standards.
References
Alards-Tomalin, D., Ansons, T., Reich, T., Sakamoto, Y., Davie, R., Leboe-McGowan, J., & Leboe-McGowan, L. (2014). Airport security measures and their influence on enplanement intentions: Responses from leisure travelers attending a Canadian University. Journal of Air Transport Management, 37, 60-68. Web.
Bakolas, E., & Saleh, J. (2011). Augmenting defense-in-depth with the concepts of observability and diagnosability from Control Theory and Discrete Event Systems. Reliability Engineering & System Safety, 96(1), 184-193. Web.
Elias, B. (2010). Airport and aviation security. Boca Raton, FL: CRC Press.
FAA. (2015). Airport Categories. Web.
Hoggan, K. (2012). Testimony on TSA’s use of technology to support a layered approach to security. Web.
Lenot, D. (2015). A Layered Approach to Airport Security. Security Today. Web.
PL 107–71. (2001). Web.
Stewart, M., & Mueller, J. (2014). Cost-benefit analysis of airport security: Are airports too safe? Journal of Air Transport Management, 35, 19-28. Web.
TSA. (2015). Security Screening. Web.
Yourish, K., Watkins, D., & Giratikanon, T. (2015). Recent Attacks Demonstrate Islamic State’s Ability to Both Inspire and Coordinate Terror. New York Times. Web.
