Introduction
The main goal of computer forensics is the discovery of evidence in a lawful manner. The recovered information can then be used in a court of law against a suspected offender (Sheetz, 2007). Maras (2011) has indicated that computer forensics is made up of four distinct steps; acquisition, identification, evaluation and presentation. The electronic evidence gathered becomes very useful in court to prove the act of wrong doing (Maras, 2011). According to Kirschenbaum, Ovenden and Redwine (2010), forensics is meant to assist one establish how authentic the recovered files are, check the characteristics of the files and create a document that captures every single event and the process involved.
According to Arthur and Venter (2011), forensic investigations are traditionally known to follow clearly stipulated guidelines so as to maintain the credibility of every single storage device that is involved in the investigation. One of the things that the investigator must do is to ensure that the subject matter of the computer system used during the forensic analysis is well protected. The investigator must see to it that no damage, corruption or changes to data or any virus attacks mess up the devices being used for the forensic analysis (Arthur & Venter, 2011). The computer forensic specialist is also expected to locate all the necessary files from the devices being investigated. This includes any existing normal files found in the system, others that could have been deleted but still exists in the system, hidden files, as well as those encrypted or protected by passwords (Arthur & Venter, 2011). If any the computer forensic expert discovers that some files were deleted, he or she is expected to recover as much of such files as possible. The investigator is also required to try as much as he or she can to disclose information from any files that are not visible (Arthur & Venter, 2011).
If legally permitted, the computer forensic specialist must access all the contents of the hidden or protected files. Another requirement is for the forensic expert to do an analysis of any important data that is discovered in special sections of the disk. This will include sections of the disk such as those made up of unallocated space among others (Arthur & Venter, 2011). A computer forensic expert is also expected to print out the analysis of the computer system being investigated. The print out may include the list of files as well as data discovered on the digital media, an synopsis of the system layout, the structure of files and how the information on the system is authored or owned. The generated print out will also give an idea about any malicious handling of the information stored on the computer system or devices under investigation (Arthur & Venter, 2011). Finally, the computer forensic specialist is expected to give consultation or testimony when needed. Such testimonies will usually be very useful in court process to provide the required evidence (Arthur & Venter, 2011).
This paper discusses the approach taken to investigate a crime based on a given scenario. As a computer forensic specialist, I am expected to provide on scene technical expertise and support for a militia group raid against the government. The paper is divided into different sections that are in line with the activities to be undertaken.
Preparing to Respond
Given the very sophisticated nature of digital criminal activities being witnessed globally, computer forensics specialists are forced to use varied and very highly specialized software as well as hardware tools to investigate crimes that involve the use of computer equipment. To ensure that the integrity and reliability of the devices involved is not compromised, the computer forensic experts have to adhere to some strict guidelines. The tools are available with functionalities that differ from one to another, cost variations and different levels of complexity (Arthur & Venter, 2011). While some of these tools only serve a single purpose, there are others that will be used repeatedly and for a number of functions. Apparently, the differences in functionality are the ones that lead to the complexity of the tools. It is therefore very important for computer forensic specialists to ensure that the right tools are chosen for a particular investigation (Arthur & Venter, 2011).
Tools for the Investigation
Research has shown that there are quite a number of tools that available and can be used in the process of carrying out a forensic investigation. Some tools that will be critical for conducting a successful investigation in the given scenario include; PC Inspector File Recovery, Encase, Forensic Tool Kit and FTK Imager. Another important tool to carry is ProDiscover Basic. A forensic disk controller is another tool that is of hardware nature and also comes in very handy when capturing the image of the disk during the forensic analysis process (Nelson, Phillips & Steuart, 2010). PC Inspector File Recovery is available as a free product while Encase, Forensic Tool Kit and FTK Imager are commercial tools and a computer forensic expert will therefore require a license to use it (Arthur & Venter, 2011). These tools are briefly explained in the following subsections.
PC Inspector File Recovery
As stated earlier, this tool is freely available and as such an investigator will not require a license to make use of it during the forensic analysis. It is quite useful to an investigator in two vital areas; besides being used to effectively detect all files stored on every storage media attached to the computer, it can also be used to recover data that has been deleted from a storage device (Arthur & Venter, 2011). The tool has a simple interface that makes it easy to use and this greatly contributes to its strength as a reliable data recovery tool (Arthur & Venter, 2011).
Encase
Unlike the PC Inspector File Recovery, this tool is a commercial one and according to Arthur and Venter (2011), it appeared in the forensic market in the year 1998. It provides functions such as disk imaging and can also be used to analyze and verify the data recovered. One unique characteristic of this tool is the fact that it can be used to recover data by simply inspecting the unallocated spaces on the disk which may contain information that could be very useful during the forensic investigation (Arthur & Venter, 2011). Encase allows the computer forensics expert to view the files detected on the storage media on a cluster by cluster basis. It makes it possible for one to see all the important details regarding the files such as the date and time the file was last accessed, the time when the file was created, and the last modifications that were done on the file (Arthur & Venter, 2011).
Forensic Tool Kit
This tool is also available commercially and it allows the computer forensics expert to see files on any chosen storage media. It allows the investigator to the immediately create message digest 5 (MD5) or hash values for files observed in an investigation (Arthur & Venter, 2011). It has a simplified and interactive user interface but unlike the other forensic tools discussed, it does not support offer support for data recovery (Arthur & Venter, 2011).
FTK Imager
This tool is also commercially available and besides making it possible for the computer forensics expert to view the recovered files it also provides an opportunity for him or her to get an image of the storage media. The effectiveness of the tool in data recovery is largely dependent on the time the file was deleted. The tool is ineffective if the recovery is done long after the incident. By generating MD5 or hash values, the tool guarantees the integrity of the storage media (Arthur & Venter, 2011).
ProDiscover Basic
This is a forensic analysis tool developed by Technology Pathways and that can be used to acquire and analyze data from varying file systems. It would be among the very first tools that a computer forensics specialist may use (Nelson et al., 2010).
Arrival at the Scene
Although the supervisor has done her best to give background information about the case, there are certain things that need to be clarified before investigations can officially begin. According to Arthur and Venter (2011), it is important to link a suspect to a crime by using the date and time. This is a vital piece of information without which, it will be of no use to proceed with the investigation. So far, there has not been any mention of the location of the logistics manager at the time when the raid took place. It will therefore be important for me to establish from the supervisor the exact location of the logistics manager at the time when the crime is reported to have taken place. Something else to be clarified by the supervisor is the association between the ABC’s logistics manager and the anti-government militia group. It would certainly be helpful to know to what degree the logistics manager was involved with the militia group. The supervisor has only mentioned that the logistics manager sympathized with the group but this does not provide strong evidence to show that the manager was connected to the group’s criminal activities.
As the police officers prepare to enter the building ahead of me to get hold of the logistics manager, my instructions for them will be to ensure that the arrest comes as a surprise to logistics manager lest he gets an opportunity to tamper with the evidence at his desk just before they get to him. I will also want the officers to make sure that they leave the manager’s office as they found it. Sheetz (2007) found that digital evidence can be very volatile and hence the need to be extremely cautious. It has also been confirmed that the first people to arrive at the crime scene can very easily tamper with the evidence and make the investigations quite difficult (Nelson et al., 2010).
Scene Examination & Evidence Collection
Wilkinson and Haagman (2007) identified a number of computer items that can be used productively during a computer forensic investigation. In the given scene, shown in figure 1, there are several pieces that could be holding potential evidence. These include three computer system units placed under the table, hard disks, Compact Disks (CDs), a flash disk, telephone set and monitors. Inside these system units, it is possible to get storage media such as the hard disk, floppy disks, jazz disks, and probably compact disks and digital versatile disks (DVDs) left within the CD/DVD drives. These devices can help to reveal any data that could have been saved in them and that may be of great support to the investigations. According to Sheetz (2007), the most evidence that is recovered for a forensic investigation will often come from storage system whether it is removable or fixed inside the computer system unit. There are also two monitors on the desk and although a printer cannot be seen in the vicinity, some pages seem to be lying around and could be of help too. Unlike in the case of the monitor, a printed output will provide very powerful evidence that is of non-volatile nature. Although monitors will only display information momentarily, they too can supply very useful evidence for the investigation (Sheetz 2007).
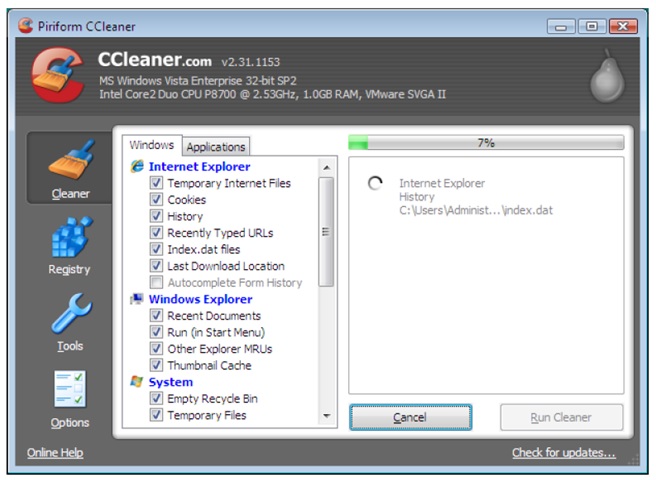
At the site of the above window, the first thing to do will be to immediately stop the progress of the operation by clicking the cancel button to prevent the process from going any further. The completion of the task could get rid of critical evidence from the system. Next, I may have to use a camera to capture the screen as it is as evidence.
The evidence I will collect from the scene include; the hard disk drive, the flash disk, some papers lying around the manager’s desk and that may look suspicious, the CDs or DVDs, and the telephone set. Using ProDiscover Basic, I will take the image of the system disk. I will carefully collect and pack the storage media in antistatic bags so as to avoid exposing them to any form of damage. Antistatic bags are used to store computer accessories in such a way that they will not be affected by external interferences.
The main purpose of the chain of custody document is to enable the investigator to keep track of the evidence collected. It is used to help capture what has been seized, how the seized items will be stored, transferred or even disposed. When the case finally gets to court, it may be used to show the integrity of the evidence presented before the court.
In answer to the Supervisor, I will let her know that other potential digital evidence that may exist include personal digital assistants, cell phones and any other mobile devices. If these are also available, it would be important to have them as well.
Interviews
Before leaving the scene, I will need to know from ABC’s Lead System Administrator a number of things. I will, for example, want to know why according to him, the suspect was involved in the crime. I would also like to know what systems are used by the organization and the kind of data stored in them. Finally, I would like to know from him, when the crime occurred and how this was discovered (Anson & Bunting, 2007). Additionally, I would like to know the kind of security measures the organization has in place and if I could be allowed to access the proxy server log that contains details captured about the suspect’s machine during the perceived time of the crime as this can be helpful in tracking the suspects’ communications.
I believe that it is important to ask the suspect some questions at this point especially considering that the computer users can serve as a very useful source of information that can later be used in the investigation. Information such as the user’s system configuration, his or her favorite applications and knowledge about the type of encryption technologies they use are very critical to understanding how evidence may be collected. However, I would hesitate to do so if it turns out that the suspect is not willing to respond to my questions. According to Nelson et al (2010), the rights of all people are protected by the law of search and seizure and all investigators are required to be professional and abide by the laws. This will also help the computer forensics expert to guard his or her integrity.
Initial Examination
Apart from the information found on the hard drive, other details that can be fetched from the computer before the forensic examination begins are; access details for files that were saved on storage that is not connected to the computer and any information about the use of the recycle bin.
Message Digest 5 (MD5) is an algorithm which ensures the integrity of an image file is not compromised (Arthur & Venter, 2011). It makes use of a 128-bit message digest referred to as a hash value to perform its function. The message digest is alleged to be very unique to an image file just as finger prints are to human beings (Arthur & Venter, 2011). The fact the MD5 report shows an error discovered indicates that security was compromised and presents a problem that needs to be investigated.
Forensic Examination
The “C:$Recycle.Bin” directory represents the recycle bin which stores all the files that were deleted from locations on the disk. The “C:Program Files” directory is the location where application files for the programs running on the computer reside. The “C:UsersRobertsDesktop” directory refers to the desktop directory associated with the user Roberts who is the suspect in this case. Finally, the “C:UsersRobertsDocuments” directory represents the default save location for Roberts’s files.
To determine the exact owner of the file, I will have to check the properties of the Microsoft Excel spreadsheet file. These properties can be checked by right clicking on the file and selecting properties from the resulting context menu. From the properties dialog box, the identity of the owner can be established by clicking the details tab and checking the author property to find out the owner of the spreadsheet document.
Metadata is data is data that is kept about another data. In this case, it will be data that has been kept about different information sources such as the files on the hard disk and other storage media. Metadata is very important to digital forensic examination as it allows the investigator to gather crucial evidence about the gathered evidence.
Reporting
The spreadsheet discovered provides a basis for linking the suspect to the planned raid by the militia group. The fact that one of the explosives that was transferred was very similar to the one used in the raid confirms the allegations made by the Supervisor and is good enough to make the investigations team believe that the suspect actually took part in the raid. Given that the type and weight of the transferred explosive corresponds to the one used in the raid, it is possible to show that the suspect was involved.
Testimony
A fact witness is one who testifies about matters they know of, have seen or directly heard about (Gutheil, 2003). On the contrary, an expert witness will draw his or her conclusions from data. This may include data that has been collected by others and made available.
It always helps to look at the jury when answering questions so as not to give the impression that one is telling a lie. Facial expressions are quite informative during an interrogation and it is possible for one to tell whether or not truth is being told by looking at the eyes. Many times, people who are lying will tend to look a way from the person they are lying to. It is therefore important for the forensic specialist to be careful about maintaining an eye contact with the jury.
The challenge in testifying on digital evidence and digital forensics results from the fact that it may be quite difficult to communicate with the audience considering many may not be conversant with the technical terms used. The unfamiliarity with computer jargon may create a lack of interest and could make the audience fail to listen effectively. Without proper listening, the outcome of the interrogation may end up being biased.
I will answer the defense attorney by reaffirming that I am not in any way being unfair. Besides, I do not know the suspect and was just called in to carry out investigations. I therefore do not have a single reason to falsify evidence against his client and as such, it is wrong for him to make the said allegations.
Conclusion
In spite of many hurdles being encountered during the investigation process, it is important for a computer forensic specialist to maintain his or her focus to the end. The investigator should display confidence all the way must never be intimidated by any one at any stage of the process. In this particular case, the defense lawyer came with a very intimidating approach that could easily derail a less confident investigator.
One important lesson to learn is that the gathering of evidence should be done in a very speedy manner to avoid incidences like what happened in this case when the suspect later denied the computer forensics specialist the authority to continue examining his digital evidence.
References
Anson, S., & Bunting, S. (2007). Mastering Windows Network Forensics and Investigation. Indianapolis, India: John Wiley and Sons.
Arthur, K. K., & Venter, H. S. (2011). An Investigation into Computer Forensic Tools. Pretoria: Forensic Focus. Web.
Gutheil, T. G. (2003). Influential Publication: Types of Witnesses. Arlington, VA: American Psychiatric Association. Web.
Kirschenbaum, M. G., Ovenden, R. & Redwine, G. (2010). Digital Forensics and Born-Digital Content in Cultural Heritage Collections. Washington, D.C: Council on Library and Information Resources. Web.
Maras, M. M. (2011). Computer Forensics: Cybercriminals, Laws, and Evidence. Sudbury, MA: Jones & Bartlett Publishers.
Nelson, B., Phillips, A., & Steuart, C. (2010). Guide to computer forensics and investigations. Boston, MA: Course Technology, Cengage Learning.
Sheetz, M. (2007). Computer forensics: an essential guide for accountants, lawyers, and managers. Hoboken, New Jersey: John Wiley and Sons.
Wilkinson, S., & Haagman, D. (2007). Good Practice Guide for Computer-Based Electronic Evidence. Sawston, Cambridgeshire: 7Safe Information Security. Web.
