Introduction
Recognizing the absolute priority of data for society, it is justified to strive for its maximum protection. The issue of finding options to protect critical data is a significant challenge, and one of the most effective working methods is encryption. This fact has become the basis for in-depth research examining data encryption procedures and their varieties. To direct the report, it was decided to discuss potential cybersecurity mechanisms for a fictitious food production organization.
Since it is recognized that the organization’s management is unfamiliar with network security theory, the concepts and ideas cited in this paper are discussed in sufficient detail so that the information is perceived by management. The report is a useful synthesis of the available broad information and is therefore relevant both for the author, who is improving their competence, and for the reader interested in learning more about encryption procedures.
The Objectives of Network Security
The base from which the signal originates in the telecommunications system is subject to multiple risks, differentiated into physical and virtual ones. Typically, physical threats are not predictable or controllable but instead are caused by direct interaction with the base’s servers or computer devices (“Potential security,” 2021). For example, any natural disaster, theft, or destruction can result in the loss of commercially sensitive data that cannot be recovered if the user has not previously created cloud backups. Meanwhile, the exchange of information between the two computers is not tangible, and therefore once data has been sent from them, manipulation of it is no longer possible.
Nevertheless, during the transmission of information between points, the possibility of interception or theft is not excluded, which creates some pressure on the development of protection systems. In general, information security objectives include preventing data leakage, theft, or distortion, achieving a sufficient security level of stored data, realising through the prevention of unauthorized reading, and blocking the possibility of obtaining useful information from stolen material (Passi, 2018). Thus, with the proper protection level, even stolen materials will provide no tangible benefit to the cybercriminal because they have been securely encrypted beforehand.
Simultaneously, creating a data encryption system, implemented through careful design of a model that encodes information with a specific pattern is known only to the sender, requires caution. If developers are unreasonably careless, encrypted information can be easily compromised even without an encryption key (Gervais, 2017).
On the other hand, modern cybercriminals’ technical capabilities, especially when industrial and cross-national espionage is considered, have reached certain heights. In other words, unsophisticated encryption keys can be spoofed using matching mechanisms. It follows that stolen information, encrypted unreliably, will eventually end up in the hands of attackers. To summarize the analysis of information security objectives, it should be noted that it must be aimed at improving the security, availability, confidentiality, and integrity of data. Together, accessibility, integrity, and confidentiality form a well-known concept in the encryption environment, which is commonly referred to as the CIA triangle: Figure 1.

Plan of Protection
Creating a specific architecture for a fictitious product organization begins with identifying the key nodes that make up its foundation. This includes the database management system, which contains commercially important information for the firm. Subsequent nodes include LAN, SOAP, network usage protocols, and the use of employees’ personal and work devices from which software-based workflow management can be accessed. It seems clear that in the context of the complexity of a fictitious company’s IT system architecture, ensuring the proper level of cybersecurity is an important need. LAN systems can be vulnerable since they are a sequence of physically connected computers, and thus information between them can be intercepted (NIST, 1994).
The most likely threats to LAN systems are network packet hijacking, incorrect use of communication ports, unauthorized access to all network traffic, spoofing, and other methods by which attackers can steal data. That is why it is a critical need for company management to ensure sufficient security management, which includes protecting data and access at various levels. Specifically, any protection begins with limiting access to confidential data, which can be accomplished through a system of differentiated access levels and authorization protection (Stefani & Ferrari, 2017). Identity management should be used for cybersecurity, implemented through the control of authorization and employee access to data.
The information has the property of confidentiality and cannot be disclosed to third parties or employees without the proper level of access to it. In addition, it is in the best interest of the management of the fictitious company to worry about educating their employees about personal online security measures implemented through prohibiting clicking on unfamiliar links, increasing computer literacy, and keeping track of known social engineering techniques (Salahdine & Kaabouch, 2019). Finally, to maximize the protection of key commercial data, appropriate physical protection of local devices should be provided.
Specific measures may include establishing passwords for access to the premises, using CACs, 24-hour security guards, and entry and exit searches. Finally, to protect employees from episodes of social engineering and maintain the confidentiality of email, it is appropriate to introduce a training system to the organization, allowing a qualitative rise in computer literacy staff.
Data Hiding Technologies
Recognizing the importance of providing network security, it is appropriate to consider the range of potentially useful cryptographic data protection systems that can be implemented in a fictitious company’s organizational practices. Typically, they differ in the principle that underlies encryption (McFadden, 2018). For instance, the Caesar cipher belongs to the substitution categories, in which each character of the original alphabet is shifted to the left or right side by a certain but constant number of steps. The essence of the polyalphabetic cipher is the application of multiple alphabets to the original text: an illustrative example of such a cipher is the Vigenère method, in which an unconnected sequence of letters can be created using a short codeword, using the Cipher Table.
Symmetric encryption subsystems, the essence of using the same keys to encrypt and decrypt the original message, are also highly popular for data protection. The Vernam cipher, an algorithm that consists of fragmenting a text message into symbols written in binary form, has absolute cryptographic strength. Then a Boolean function XOR is applied to the resulting code, and the cipher outputs a sequence of alphanumeric characters whose repetitions do not mean the same initial character. Another example of symmetric encryption is using a block cipher, where the original message is divided into blocks of a fixed length, encoded individually: the result is ciphertext.
The AES algorithm fragments the message and converts one 128-bit block into another using the secret key needed for this conversion. Once the data is put into a 4×4 matrix format, the encryption key is added using an XOR operation. After that, conversions and substitutions are performed using the SPN block cipher algorithm. A second conversion with the same secret key is used to decrypt the resulting 128-bit block. Another type of symmetric encryption, namely Triple DES, has high reliability and higher message processing time (Allan, 2019). The technique consists of successive triple use of non-linear and linear message transformations, including using a Feistel network, utilizing three different encryption keys.
An intriguing example of cryptographic data protection is the RSA system, which assumes a public key. The user creates a public cipher based on two large numbers and auxiliary values: if the code is simple, it will be easy to read the message with it, but the procedure becomes more complicated if a long key is generated. The public code remains public, but the decryption rules are described in a secret code accessible only to the user.
In addition to encryption algorithms, methods of hiding information are relatively reliable. In particular, some compromise between encryption and data hiding is texture block encryption, which describes the transfer of a textured area to a place with a similar texture. As a result, the copied area covers the protected area and the data is hidden. Faster protection is realized by means of a digital watermark designed to protect the copyrights of materials. This is used by applying a semi-transparent protective symbol to the object, whether text, video or image, preventing the possibility of unauthorized copying. Finally, hiding data from images is also possible through the use of masking and filtering functions. These procedures have different purposes, because masking hides an important part of the material, as in the case of bank cards, and filtering mechanically categorizes users according to their level of access. All of these together constitute a range of useful security strategies that can be used in a fictitious company.
Threats to Information Security
The set of nodes includes the DNS server, the company’s web servers, social engineering, loss of operating system integrity, or storage media theft. It follows that there are a considerable number of factors that must be considered in advance before a company decides to implement an information security system to achieve maximum security against external and internal threats. It should be started with social engineering, which is the psychological manipulation of users with access to specific actions or disclosing sensitive information. Typically, the attack on employees is carried out through phishing or email, when under the pretext of useful messages comes a link to viral material (Chiew et al., 2018). As a result, unwittingly, the user gets caught in an information trap and reveals commercially valuable information to intruders.
On the other hand, the threat in an employee’s context can come from within when the user personally steals and discloses data to third parties. This scenario seems even more dangerous, as scammers do not need to pick up the decryption key because the employee personally discloses the already decrypted data to them (Buchan, 2019). Regardless of the user’s intentions, however, this threat is solved by regular training on improving the information culture and making the login system more complex, for example, through two-factor authentication. To monitor internal spying, a company can use auditing and checking outbound traffic on work computers.
Another important target of hacking is the DNS server, which can be hacked to bypass blockers set on a personal computer. Since the DNS server acts as an intermediary, attacks on DNS are the most sensitive. For example, an attacker can send a request to the target computer sent to DNS to establish an address. However, a vulnerable DNS sends a massive number of unnecessary files in response until the computer is paralyzed. The obvious solutions to this problem are to securely encrypt the data passing between the computer and DNS, update the DNS server, or set limits on the amount of cached data to be poisoned.
An alternative option to attack the DNS server is idle scan, characterized as a series of forced disclosures of the working computer’s IP address to determine the port’s openness (Selçuk, 2017). However, it is essential to note that this method is an indirect verification technique that does not directly interact between the attacking computer and the target. Protecting against such threats consists of enabling a firewall, implementing outbound filtering, and, for example, randomizing the IPID sequence.
One of the most sensitive areas for cyberattacks is web servers, which are used to keep the network up and running. For example, a typical operating computer sends an HTTP request to a server, in response to which the server returns an HTTP response with media content attached. Attacks on this communication are among the most common since the job computer is not directly involved. Examples of such threats include DDoS, which drives a system to failure, SQL Injection, which violates database read rules, or MITM, which compromises the communication channel between individuals (Melnick, 2018). Each of these scenarios is different, but common strategies to eliminate threats are DDoS attack inspections, use of ISP/Firewall configuration, data encryption, and authoring authentication with regular monitoring of intermediaries.
Common Access Card
Encryption ranks very high when it comes to securing the way data is stored, as modern cryptographic techniques offer the best security. It is safe to say that many of the commercially available cryptographic offerings are so secure for the user that the loss of the decryption key can make it completely impossible to access the material (“Encryption concepts,” n.d.). In most modern enterprises, however, this security level seems excessive, so employees store their access keys on physical ID cards, creating a network of access levels called CAC (Parsovs, 2020). Since commercial data protection is a priority within a fictitious company, it is appropriate to propose an identity management strategy in production. In particular, such an initiative is formed by introducing an access card system, giving each employee a unique level of access.
This eliminates the possibility of unauthorized entry by junior employees into higher security levels, which is a key advantage for network security. According to the CAC strategy, deploying access levels requires each employee to have unique, personalized data, be it biometric tags or code words. The data collection stage is followed by categorization so that each access card contains encrypted access information and an encryption key is required. For example, when going through the checkpoint, the employee would only need to put the card in the reader to verify their identity. For more serious scenarios where increased security is required, two-factor authentication is used. Applying an access card to decrypt data or confirm identity is accompanied by a codeword or numeric password. Ultimately, such a system will significantly increase network control and improve overall security.
Moreover, employee can lose their physical card, which means that the threat of data theft will be maximum. In this case, CAC’s strategy proposes using two-factor authentication because, in addition to the card, the employee must also know the PIN that is requested when utilizing the access card. Simultaneously, the information stored on the card is securely encrypted using a 2048-bit algorithm to ensure the highest level of security. It follows that the deployment of CAC is a successful strategy that simultaneously solves two problems: the creation of access levels and data protection.
Email Security Strategy
Within a company, employees can be exposed to phishing attacks or spam, which, if not handled properly, can lead to emails being compromised. This is especially true in the case of stolen data of the head or military institutions’ commanders, whose access to sensitive material is elevated. Phishing not necessarily aims only at gaining access to the emails but can also be directed at implicitly accessing the employee’s work computer. To minimize outbound threats, it is appropriate to utilize an email security strategy implemented through several forms. Thus, training users’ computer culture is the right solution, allowing them to reduce risks and save more useful information preventively. This helps to teach employees not to open spam emails, not to click unfamiliar links, and primarily not to provide access to their digital key to third parties.
Another area of email protection is regular monitoring and auditing of the system for threats. More specifically, such expertise can be implemented through auditing and anti-virus software that identifies vulnerabilities and inhibits hacking threats. On the other hand, system monitoring can be performed by examining outgoing and incoming traffic flows over available POP3, SMTP, NNTP, or IMAP protocols (“Types of network protocols,” 2018). Traffic control and filtering can be carried out by installing firewalls that prevent unwanted requests from entering the local network. In the context of the measures already mentioned, encryption methods and the setting of access levels should be highlighted.
Thus, email correspondence can be securely encrypted using the user’s key, and even if stolen, emails will not yield any useful information to intruders. This is done through the user having a private key, which must not be compromised. Then any information sent from computer A will automatically be decrypted by computer B, increasing telecommunications’ security. Simultaneously, the access levels will define the privileges of each level of the hierarchy to the corporate mail and thus provide an additional layer of protection. Ultimately, all of the above examples of email security strategy implementations make it possible to create a secure, invulnerable virtual environment in which the use and transmission of data are unobstructed.
Conclusion
This report has deeply investigated the network security systems and information security principles based on cryptographic methods. In particular, network security allows protecting the useful information of an enterprise or institution from intruders. It was shown that the number of potential threats to network security is large, and each of them has proposed its management strategies. To improve network security, it is also appropriate to deploy an access level strategy through CAC and enhance email protection.
The Laboratory Work
To put the theoretical knowledge of encryption systems into practice, laboratory work on understanding cryptography was performed. More specifically, this work was based on the use of verbatim methods of hiding data within another, more enormous array. To do this, the original text message was placed on an image so that it would appear encoded and not visible when viewing the image.
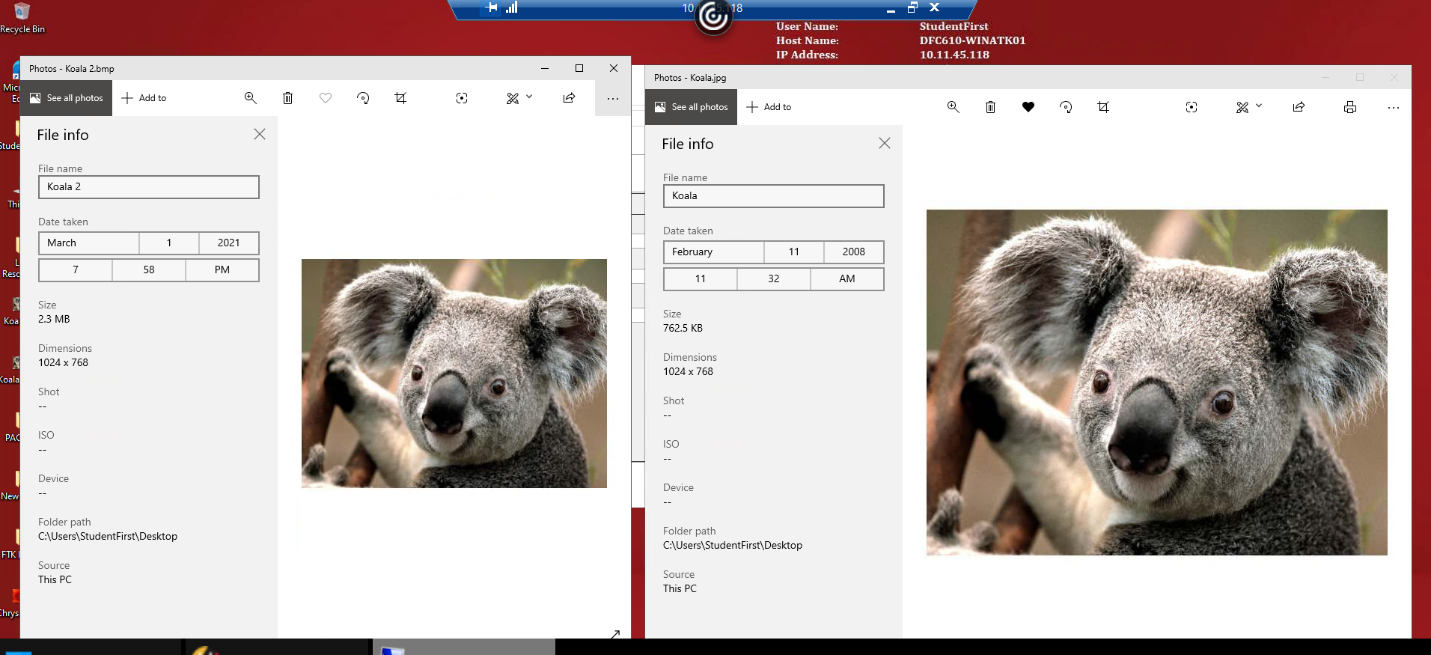
The OpenStego tool was used for this purpose. Precisely, using the built-in functionality, the text message (Figure 2) was placed on the Koala’s original photo. A comparison of the properties of the two images (original and modified) allows determining that the weight of the second image has become greater (Figure 3), which means that the inclusion of text in the file has been implemented successfully.
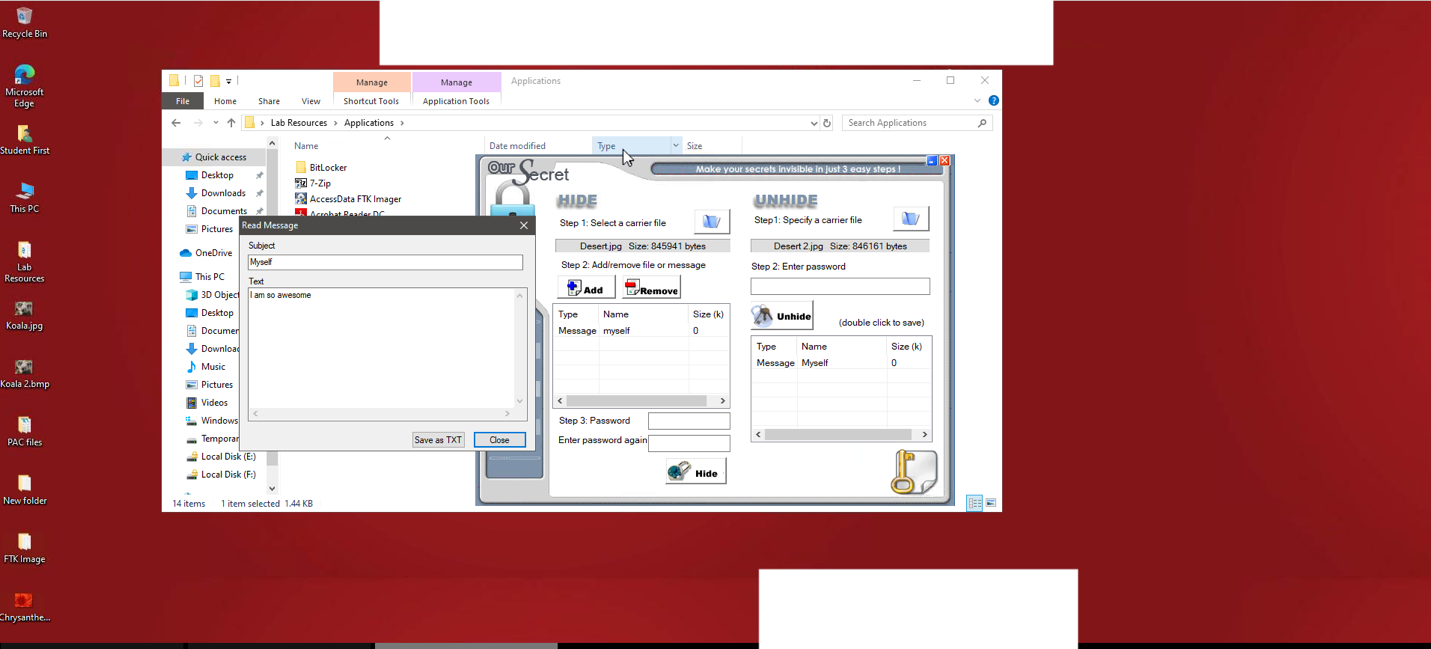
In addition, the built-in OurSecret tool was used for a similar study, which involved placing a text message on the desert image and then checking it. As can be seen in Figure 4, the text message “I am so awesome” was inserted into the original image, after which the weight of the image increased by 220 bits.
As a result, in this laboratory work, the mechanisms of hiding textual information in the image through two software programs, OpenStego and OurSecret, were investigated. It was shown that the weight of the modified images increased in a regular way, which was a confirmation of the fact of stenographic concealment. Nevertheless, it is critical to clarify that the use of this tool did not allow to encrypt the text message using one of the known algorithms but hid it in the file structure of the image.
References
Allan, M. (2019). 6 types of encryption that you must know about. GoodCore. Web.
Buchan, R. (2019). Taking care of business: Industrial espionage and international law. The Brown Journal of World Affairs, 26, 143-150.
Chiew, K. L., Yong, K. S. C., & Tan, C. L. (2018). A survey of phishing attacks: Their types, vectors and technical approaches. Expert Systems with Applications, 106, 1-20.
Encryption concepts. (n.d.) IBM. Web.
Gervais, J. (2017). Encryption: What you need to know. LifeLock. Web.
McFadden, C. (2018). 11 cryptographic methods that marked history: From the Caesar cipher to enigma code and beyond. Interesting Engineering. Web.
Melnick, J. (2018). Top 10 most common types of cyber attacks. Netwix. Web.
NIST. (1994). Guideline for the analysis local area network security: Federal information processing standards publication 191. Web.
Parsovs, A. (2020). Estonian electronic identity card: security flaws in key management [PDF document]. Web.
Passi, H. (2018). Determining the duties and responsibilities of an IT security team. Grey Campus. Web.
Potential security threats to your computer systems. (2021). Guru99. Web.
Salahdine, F., & Kaabouch, N. (2019). Social engineering attacks: a survey. Future Internet, 11(4), 89-106. Web.
Selçuk, S. (2017). What is Idle Scan?. Icterra. Web.
Stefani, E., & Ferrari, C. (2017). Design and implementation of a multi-modal biometric system for company access control. Algorithms, 10(2), 61-71.
Types of network protocols explained with functions. (2018). ComputerNetworkingNotes. Web.
Walkowski, D. (2019). What is the CIA triad?. F5 Labs. Web.
