Database Security
The concept of cloud computing may be regarded as an Internet-based form of computing in the modern world of data management. Particularly, cloud computing facilitates the storage, management, and processing of data through the application of a system of remote servers hosted on the Internet, as opposed to deploying a personal computer or a local information storage mechanism.
Today, various individuals offer cloud-computing services to organizations to foster their data management processes. Cloud computing vendors act as third parties in the management of institutions’ classified details stored on the Internet. As a result, these organizations end up losing full control of their data, hence subjecting themselves to an array of challenges.
Techno Solutions has hired me as an IT consultant to help in identifying potential security issues such as data breaches and distributed denial-of-service (DDoS) attacks among others, which may arise from providing data to third parties for storage or management. A detailed investigation of the above issues will be followed by recommendations regarded various remediation strategies that Techno Solutions can implement to safeguard its data.
The Cloud Architecture
According to Erl, Puttini, and Mahmood (2013), an organization’s cloud computing architecture is comprised of different aspects, including software capabilities, databases, and applications, which are engineered to influence the power of Internet-based resources. The goal is to solve various security problems faced by contemporary institutions. To realize sustainable and secure business practices, Techno Solutions should develop a cloud-computing environment that integrates sophisticated architecture. Figure 1 below shows the various components of a standard cloud computing architecture.
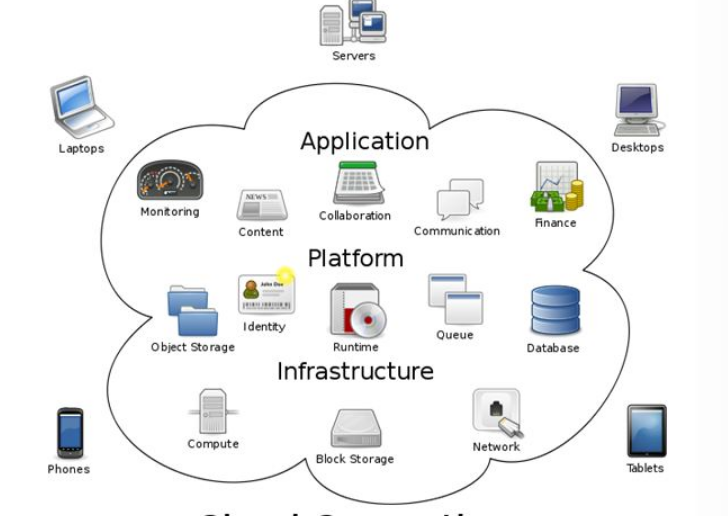
According to Scudder (2011), the above cloud computing structural design is comprised of four primary components that include cloud resources, on-premise resources, software mechanisms and services, and middleware. The above system focuses not only on providing high bandwidth to users but also allowing them to have continuous access to applications and data (Erl et al., 2013). This cloud architecture also fosters the functionality of Internet-based services by facilitating the delivery of on-demand agile networks that allow organizations to swiftly navigate through servers. Besides, it seeks to boost network security by ensuring the effective management of data hosted on the Internet (Scudder, 2011).
Nonetheless, organizations, which operate in the present-day technology-driven business world, cannot rule out the possibility of network security issues emerging from the use of cloud computing services because the above architectural components may encounter interference (Stallings & Brown, 2015). Hence, as an IT consultant, it is fundamental to advise Techno Solutions regarding various security challenges associated with its cloud-computing environment.
Potential Security Issues for Techno Solutions’ Cloud Computing Environment
Over the past few years, concerns have been raised regarding the security of cloud computing services. Particularly, major companies are complaining about data breaches among other information security issues. As a result, many contemporary institutions have become hesitant regarding their adoption of the cloud computing services, especially if a clear security plan is not available (Modi, Patel, Borisaniya, Patel, & Rajarajan, 2013). In this case, organizations such as Techno Solutions need to ensure that their cloud-computing environments incorporate features that enhance the security of any classified data.
Data breaching is one of the potential security issues that are associated with cloud computing. A study conducted by Modi et al. (2013) reveals that most of these intrusions occur due to the failure of an organization to put in place proper security measures that facilitate the protection of data. As such, the absence of proper information safety mechanisms within Techno Solutions’ cloud computing environment is likely to expose this company to data breaches, hence subjecting sensitive information to the risk of being accessed to serve malicious purposes.
Besides, according to Erl et al. (2013), institutions, which use office computers or local servers to store information, are three times less likely to encounter data breaches compared to those that utilize cloud computing storage services. In this concern, the failure of Techno Solutions to maintain a cloud-computing environment characterized by greater data security measures makes it vulnerable to breaches when using Internet-based services.
Distributed denial-of-service (DDoS) attacks also form a potential security threat to an organization’s data stored in cloud computing platforms. Initially, the cloud computing architecture made it difficult to initiate DDoS. However, the Internet of Things (IoT) has made it possible for parties with malicious intent to jeopardize the safety of data on the cloud (Modi et al., 2013). The existence of sufficient traffic to a cloud computing system has the potential of making it a DDoS target ineffective, thus subjecting the entire system to difficulties.
Furthermore, according to Erl et al. (2013), DDoS attacks undermine the accessibility of servers and websites. They may also be applied to interfere with applications such as web security firewalls. As a result, the failure of the cloud-computing environment at Techno Solutions to consider the possibility of DDoS attacks has the potential of undermining the security of the organization’s data.
The deployment of cloud computing services may expose a user’s account to hijacking. The seizing of institutions’ accounts is common in the cloud computing landscape where parties with malicious intentions may utilize a user’s login information to access sensitive information remotely stored on the cloud (Modi et al., 2013). Additionally, attackers may use false information from hijacked credentials to gain entry to the data present in the cloud. Furthermore, as Erl et al. (2013) assert, account hijackers may utilize reused passwords and scripting buds to gain access to information stored in various cloud platforms.
Other methods of account attacks include buffer flow, keylogging, and phishing (Stallings & Brown, 2015). Hence, attackers may use various ways of acquiring login credentials that could allow them to remotely access private data without the knowledge of the respective organization. Techno Solutions should not ignore the need for putting in place the right measures to stop attackers from easily hijacking users’ accounts.
The cloud is also vulnerable to malware injections, which may undermine the security of an institution’s data. According to Modi et al. (2013), to inject malware, attackers may embed malicious codes or scripts into selected cloud services, thereby making them appear as part of the system. This move by attackers may compromise the integrity of sensitive information by stealing it. Malware injections have become one of the largest security threats in the cloud-computing spectrum. Consequently, cloud-computing companies need to implement measures that prevent attackers from introducing malicious codes or scripts to access private information.
Recommended Remedial Strategies
The identified possible security issues regarding cloud computing may harm Techno Solutions’ image as far as its management of sensitive information is concerned. As such, this organization needs to consider the following remedial strategies to guarantee efficiency in its cloud-computing environment.
Firstly, Techno Solutions needs to authenticate all people who have access to its network. This move is vital since it prevents unauthorized people from gaining access to any sensitive information stored on the cloud. Such a strategy is recommended because it enhances the protection of data from breaches that could threaten the well-being of individuals as well as the organization.
Secondly, certification of the entire software running on any computer in the company is also a pivotal measure towards the creation of a cloud-computing environment that is free from attacks, including malware injections. Additionally, all changes to such software need to be legitimate to guarantee the safe installation of updates. Particularly, Techno Solutions should ensure that its cloud vendors automatically validate any software patches before configuring the changes accordingly. They should further advise on the need for proactive management of all security patches.
Lastly, this organization needs to monitor the entire network activity. The goal is to find out the existence of suspicious plans that may threaten its data safety. This measure can be facilitated by deploying an intruder-detection technology that provides the company with an independent view of all network activities. This strategy has the potential of preventing instances of data breaches, DDoS, and malware injections among other security risks that may jeopardize the safety of the proposed cloud-computing environment.
Conclusion
Cloud computing provides an alternative way of storing, managing, and processing datastore on the Internet. The cloud architecture is comprised of various components, including databases, software, and storage systems that provide solutions to business problems. Nonetheless, safety issues such as data breaches, DDoS, and malware injections may affect the proposed cloud-computing environment at Techno Solutions. The need to counter these potential security threats calls for the adoption of data protection strategies such as authenticating people accessing the network, legitimizing software mechanisms, and monitoring the organization’s network activity regularly.
References
Erl, T., Puttini, R., & Mahmood, Z. (2013). Cloud computing: Concepts, technology & architecture. Upper Saddle River, NJ: Prentice Hall.
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey on security issues and solutions at different layers of Cloud computing. The Journal of Supercomputing, 63(2), 561-592.
Scudder, R. (2011). Visualizing the workings of cloud computing with diagrams. Web.
Stallings, W., & Brown, L. (2015). Computer security: Principles and practice (3rd ed.). New York, NY: Pearson.
